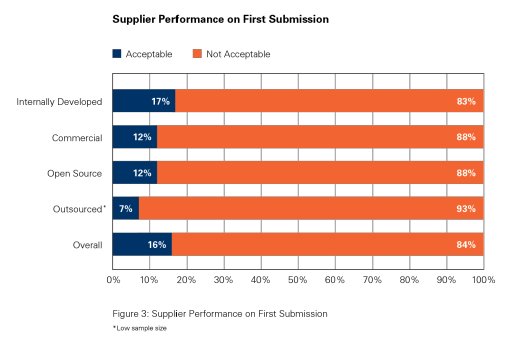
You only have to glance at the headlines to know that the state of computer application security is bad. But a new report from Veracode makes clear how bad: just 16 percent of almost 10,000 applications tested in the last six months received a passing security grade on their first attempt.
The finding, presented in the latest, semi annual State of Software Security Report, is a marked departure from Veracode’s report six months ago, in which 42% of the applications tested passed on their first try. Application security experts at the company reported continued problems with insecure Web applications in use by government agencies, and a plethora of insecure mobile applications.
The precipitous drop in the “pass” rate for applications was caused by the introduction of new, tougher grading guidelines, including a “zero tolerance” policy on common errors like SQL injection and cross site scripting holes in applications, Veracode said.
The report compiles the results of eighteen months of automated and manual testing on 9,900 applications said Sam King, Veracode’s Senior Vice President of Marketing. Researchers at the company expected to see a drop in the pass rate after instituting the new, tougher standard. But they were still surprised by ho big a drop there was, King said.
The new, tougher policy on vulnerabilities like SQL injection and cross site scripting reflect the reality of the threat landscape and the demands of customers, said Chris Wysopal, Veracode’s Chief Technology Officer.
“In the past, applications might get away with a certain number of medium criticality vulnerabilities. But our customers were saying: that’s not right. We don’t want to buy or build anything that has a SQL injection or cross site scripting hole.”
SQL injection and cross site scripting vulnerabilities were among the most commonly used holes exploited by groups such as Anonymous and LulzSec in the last year, King noted. In just one attack in April, dubbed “Lizamoon,” thousands of websites around the globe were targeted with SQL injection attacks that redirected visitors to a rogue anti-virus (AV) site. Indeed, many security experts consider SQL injection attacks to be an “epidemic.”
Veracode found 40% of government Web sites were found to contain SQL injection vulnerabilities on their first scan, compared with 29% of Web sites for financial-sector firms and 30% of software vertical sites. Overall, the prevalence of SQL injection holes declined from the same period six months ago, Veracode found, though that wasn’t the case with government sites.
The story was even more grim with cross site scripting vulnerabilities. Seventy five percent of the government Web sites Veracode tested had cross site scripting holes on their first try. Finance sites faired only slightly better: 67% contained at least one cross site scripting hole and 55% of software industry Web sites.
In past reports, Veracode has warned about the danger posed by the use and reuse of canned, third party application code. That continues to be a problem, said Wysopal. Between 30 percent and 70 percent of internally developed applications turn out to be reused, third party code, mostly in the form of third party libraries, Veracode found. Often that ties directly into the prevalence of vulnerabilities. For example, Veracode believes that the high incidence of cross site scripting holes in government applications is linked to the greater use of the Adobe ColdFusion development platform by developers working within the government.
Veracode researchers also surveyed mobile applications for Google’s Android operating system. Wysopal said that many of the applications tested used encryption to protect data sent back and forth over mobile networks. However, often those applications had sloppy implementations of encryption, with cryptographic “private” keys hard coded into the mobile application. “If anyone gets access to the application – the phone is lost, for example – they could extract that key and have access to personal information,” Wysopal said. “Its difficult for organizations to recover from that kind of loss, which is why its really bad practice to put credentials in applications.”
Still, Wysopal and team found some reason for optimism. The increase in the number of applications tested is a testament to the growing demand for application testing. And Wysopal believes that many common development frameworks are getting better in helping developers spot and prevent common mistakes like SQL injection. There’s more awareness of the problem of Web application vulnerabilities, also, he said.
“Five years ago, it was rare to find a developer who even knew about SQL injection. That’s definitely changing,” he said.









