Intel has stomped out high-severity flaws in its Next Unit Computing (NUC) mini PC firmware, and in its Modular Server MFS2600KISPP Compute Module.
Overall, Intel addressed nine vulnerabilities across six products in its April security update – two of those being high-severity, and the rest being medium-severity. If exploited, the flaws could allow attackers to escalate privileges or launch denial-of-service (DoS) attacks.
Discontinuation Notice for MFS2600KISPP
One of the high-severity flaws stems from a compute module (MFS2600KISPP) used in Intel’s modular server system, which is a blade system for Intel motherboards and processors first introduced in 2008. The vulnerability stems from an improper conditions check, which could allow an unauthenticated user to potentially enable escalation of privilege (via adjacent access). The flaw (CVE-2020-0578) ranks 7.1 out of 10 on the CVSS severity scale.
In addition to this flaw, two medium-severity flaws were also discovered in the same compute module: A buffer overflow (CVE-2020-0576) vulnerability that could allow an unauthenticated attacker to launch a DoS attack (via adjacent access); and an insufficient control flow glitch (CVE-2020-0577) that allows an unauthenticated user to potentially escalate privileges via adjacent access.
All versions of the MFS2600KISPP compute module are affected, but Intel said that it is not releasing security updates to mitigate the bugs – instead, it will discontinue the MFS2600KISPP compute module entirely.
“Intel has issued a product-discontinuation notice for Intel Modular Server MFS2600KISPP Compute Module and recommends that users of the Intel Modular Server MFS2600KISPP Compute Module to discontinue use at their earliest convenience,” according to Intel’s advisory.
On a related note, Intel also disclosed an incorrect default permissions issue in the installer of its Data Migration Software versions 3.3 and earlier, which could allow an authenticated user to potentially enable escalation of privilege via local access. Rather than release patches, Intel said it will discontinue this product as well, which is used to transfer data between solid-state drives (SSDs).
April Patches
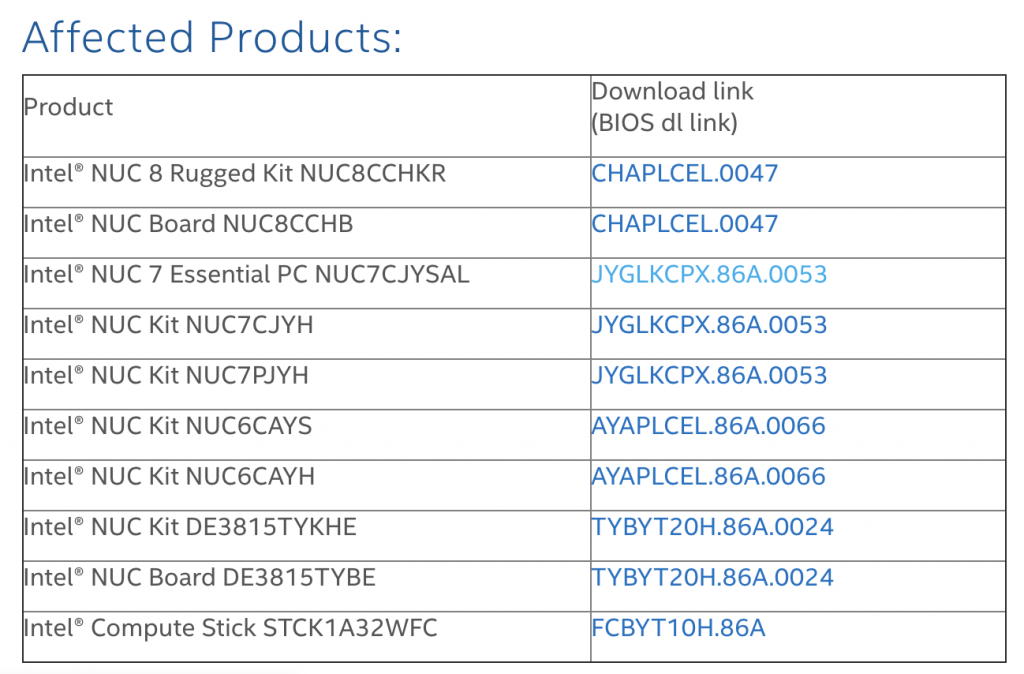
Meanwhile, a high-severity flaw in Intel’s NUC (CVE-2020-0600) could enable users to access escalated privileges – if they have local access and are authenticated. The flaw stems from improper buffer restrictions in the NUC’s firmware.
Below is a list of affected NUC products, from the NUC rugged kit to the compute stick:
Intel also fixed medium-severity flaws in its PROSet/Wireless Wi-Fi software, which allows Intel Wireless or Wi-Fi devices to function properly. The vulnerabilities could give an authenticated attacker escalated privileges via local access (CVE-2020-0557) or allow an unprivileged user to launch a DoS attack via adjacent access (CVE-2020-0558).
Another medium-severity flaw (CVE-2020-0568) in the Intel Driver and Support Assistant (which keeps systems up-to-date by sniffing out available updates) could enable DoS from an authenticated user with local access. And, an uncontrolled search-path glitch (CVE-2020-0598) in the installer of the Intel Binary Configuration Tool for Windows could also give an authenticated, local user escalated privilege. The Intel Binary Configuration Tool is a utility used to change configuration settings embedded in an Intel Firmware Support Package.
The security updates come on the heels of Intel’s March updates, where the chip manufacturer issued security patches for six high-severity vulnerabilities in its Windows graphics drivers. If exploited, these flaws could enable escalation of privilege, denial of service and information disclosure.
Also this week, Microsoft released 115 patches for Patch Tuesday, and Oracle patched a whopping 405 security vulnerabilities – while on the other end of the spectrum, Adobe went light, with only five CVEs addressed for April.
Worried about your cloud security in the work-from-home era? On April 23 at 2 p.m. ET, join DivvyCloud and Threatpost for a FREE webinar, A Practical Guide to Securing the Cloud in the Face of Crisis. Get exclusive research insights and critical, advanced takeaways on how to avoid cloud disruption and chaos in the face of COVID-19 – and during all times of crisis. Please register here for this sponsored webinar.