Intel on Tuesday revealed a new class of speculative execution vulnerabilities, dubbed Microarchitectural Data Sampling (MDS), which impact all its modern CPUs.
The flaws all ultimately depend on different ways of executing side channel attacks to siphon data from impacted systems – and result in four different attacks: ZombieLoad, Fallout, RIDL (Rogue In-Flight Data Load) and Store-to-Leak Forwarding.
“As a result of the flaw in the architecture of these processors, an attacker who can execute malicious code locally on an affected system can compromise the confidentiality of data previously handled on the same thread or compromise the confidentiality of data from other hyperthreads on the same processor as the thread where the malicious code executes,” Eric Maurice, director of security for Oracle, recently wrote in an advisory.
Here are 10 top takeaways from this latest speculative execution side channel attack impacting Intel chips.
MDS Different Than Meltdown and Spectre
The flaws derive from a process called speculative execution in processors. This process –thrown into the spotlight after the 2018 Spectre and Meltdown flaws came to light – is used in microprocessors so that memory can read before the addresses of all prior memory writes are known.
However, while speculative execution side channel attacks – like Spectre and Meltdown – targeted data stored in the CPU’s memory; MDS instead refers to issues related to microarchitectural structures of the Intel processors other than the level 1 data cache (where memory is stored). Those issues exists in components called buffers, such as Fill Buffers (temporary buffers between CPU caches), Load Ports (temporary buffers used when loading data into registers) or Store Buffers (temporary buffers to hold store addresses and data).
Intel Seeking to Downplay Impact
There are four vulnerabilities in total tied to MDS. Those are CVE-2018-12126, CVE-2018-12127, CVE-2018-12130 and CVE-2019-11091. Intel sought to downplay the vulnerabilities, saying that: “MDS vulnerabilities have been classified as low to medium severity per the industry standard CVSS, and it’s important to note that there are no reports of any real world exploits of these vulnerabilities.”
Indeed, CVE-2019-11091 has the lowest severity, with a CVSS score of 3.8, and exists in the microarchitectural data sampling structure for uncacheable memory in CPUs. CVE-2018-12126 (which exists in the Store Buffer), CVE-2018-12127 (which exists in the Load Port) and CVE-2018-12130 (existing in the Fill Buffer) meanwhile have a CVSS score or 6.5, or medium severity.
Different Attacks Exist to Exploit Flaws
Meanwhile, an array of independent researchers from VUSec, CISPA, Graz University of Technology, and more have developed attacks for these vulnerabilities. Those proof-of-concept attacks were also disclosed Tuesday in coordination with Intel, after mitigations were developed.
Those four different attack vectors are dubbed ZombieLoad, Fallout, RIDL (Rogue In-Flight Data Load) and Store-to-Leak Forwarding. While these attacks are all based on speculative execution targeting the buffer component of CPUs, they all work in different ways, exploit different flaws and result in different impacts.
For instance, while ZombieLoad allows attackers to leak information from other applications, the operating system, virtual machines in the cloud and trusted execution environments; the Fallout attack allows to read data that the operating system recently wrote and to figure out the memory position of the operating system strengthening other attack, and RIDL attack allows to leak information across various security domains
ZombieLoad: The Hard-Hitting Attack
The most severe of these attacks is dubbed ZombieLoad, which attacks CVE-2018-12130, the flaw in the Fill Buffer of Intel CPUs. That’s because this attack leaks the most data – attackers are able to siphon data from system applications, operating system and virtual machines. According to a research paper released on Tuesday, researchers said that disabling hyperthreading is the “only possible workaround to mitigate ZombieLoad on current processors.”
“With ZombieLoad, we showed a novel Meltdown-type attack targeting the processor’s fill-buffer logic. ZombieLoad enables an attacker to leak recently loaded values used by the current or sibling logical CPU,” researchers said.
ZombieLoad was discovered and reported by Michael Schwarz, Moritz Lipp and Daniel Gruss from the Graz University of Technology (known for their previous discoveries of similar attacks, including Meltdown) as well as researchers from KU Leuven, Cyberus Technology and the Worcester Polytechnic Institute.
Only Intel is Impacted (That We Know)
It appears at this time that Intel is the only manufacturer whose chips are impacted. AMD and ARM have both made public statements that the attacks and vulnerabilities related to MDS do not affect their chips.
In a statement, AMD said: “At AMD we develop our products and services with security in mind. Based on our analysis and discussions with the researchers, we believe our products are not susceptible to ‘Fallout’ or ‘RIDL’ because of the hardware protection checks in our architecture. We have not been able to demonstrate these exploits on AMD products and are unaware of others having done so.”
Future Chips Won’t Be Vulnerable
According to Intel’s microcode update guidance, most Intel Core and Xeon chips dating back to 2011 are theoretically vulnerable to MDS-related flaws.
However, Intel said that the new MDS class of flaws is addressed in hardware starting with select 8th and 9th Generation Intel Core processors, as well as the 2nd Generation Intel Xeon Scalable processor family. Future chips will also have integrated fixes, Intel said.
Flood of Vendors Security Advisories
While Intel has provided CPU microcode updates, and recommendations for mitigation strategies for operating system (and hypervisor) software, the company recommends users install the software updates provided by your operating system and/or hypervisor vendor. An array of vendors have released separate security advisories in response to MDS, including Red Hat, Oracle, Apple, Google and Microsoft.
“Microsoft has released software updates to help mitigate these vulnerabilities,” according to a Microsoft advisory released Tuesday. “To get all available protections, firmware (microcode) and software updates are required. This may include microcode from device OEMs. In some cases, installing these updates will have a performance impact. We have also acted to secure our cloud services.”
To completely address these issues, Intel said that there are additional opt-in mitigations to disable hyper threading and enable microcode-based mitigations for all processes by default.
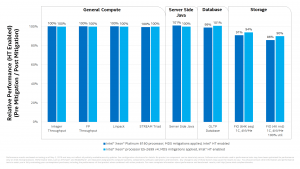
Performance Hits From Fixes Ignite Concerns
News that Intel’s fix for ZombieLoad will slow CPU performance has ignited concerns that people will be dissuaded to update their machines. It was a similar case when Spectre and Meltdown fixes were first introduced in 2018.
For instance, in a security release Apple said that in tests it found “as much as a 40 percent reduction in performance with tests that include multithreaded workloads and public benchmarks” depending on the system.
Intel for its part has a much smaller performance hit estimate: Foe example, in a Core i9 9900K with Hyper-Threading disabled, the company said that the hit could be as little as 9 percent on select data center workloads post-mitigation, for instance.
How can People Know if Their Systems are Impacted?
Researchers said that it is “very likely” that Intel chip users’ systems are impacted by the MDS vulnerabilities and subsequent attacks.
“Our attacks affect all modern Intel CPUs in servers, desktops and laptops,” said Fallout researchers in a post. “This includes the latest 9th-generation processors, despite their in-silicon mitigations for Meltdown. Ironically, 9th-generation CPUs are more vulnerable to some of our attacks compared to older generation hardware.”
Researchers also made a tool, available here, to discover whether their systems are impacted.
Side Channel Attacks Continue
The incident shows that side channel speculative execution attacks continue to plague Intel chips since the Spectre and the related Meltdown vulnerability were disclosed in 2018. For instance, in May 2018, in May, a new vulnerability was found called Variant 4, disclosed by Google Project Zero and Microsoft’s Security Response Center; researchers said it potentially enables attackers to read privileged data across trust boundaries.
Meanwhile, a new Spectre-class exploit, dubbed SpectreRSB, was detailed by researchers from the University of California at Riverside in a research paper in July; while in August, three new speculative execution design flaws in Intel CPUs were disclosed, impacting Intel’s Software Guard Extensions (SGX) technology, its OS and system management mode (SMM) and hypervisor software.
Want to know more about Identity Management and navigating the shift beyond passwords? Don’t miss our Threatpost webinar on May 29 at 2 p.m. ET. Join Threatpost editor Tom Spring and a panel of experts as they discuss how cloud, mobility and digital transformation are accelerating the adoption of new Identity Management solutions. Experts discuss the impact of millions of new digital devices (and things) requesting access to managed networks and the challenges that follow.