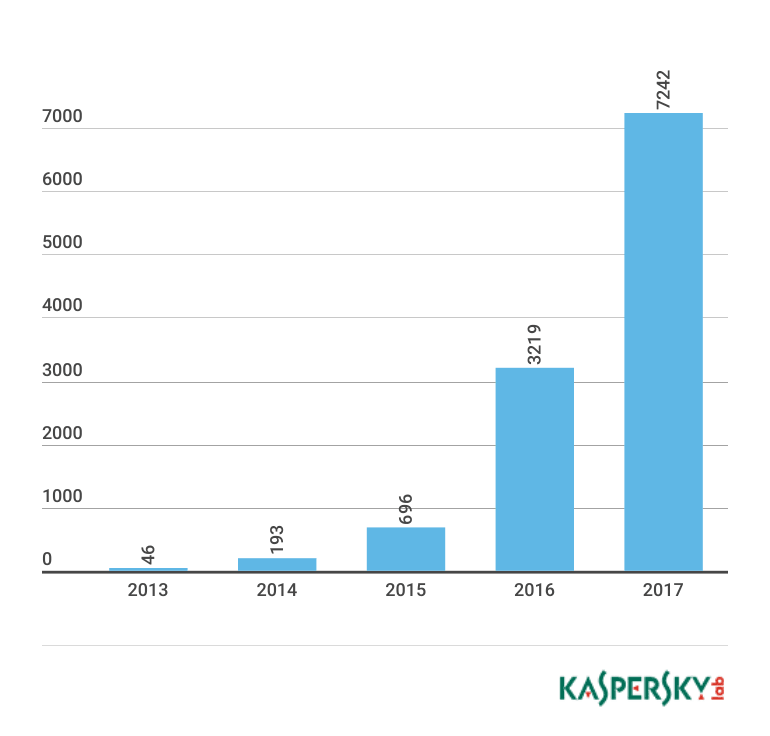
The number of new malware samples in the wild this year targeting connected internet-of-things (IoT) devices has already more than doubled last year’s total.
Honeypots laid out by Kaspersky Lab researchers mimicking a number of connected devices running Linux have attracted more than 7,200 different malware samples through May, all bent on infecting connected devices over telnet and SSH primarily. Last year, Kaspersky detected 3,200 samples.
“After just a few seconds we saw the first attempted connections to the open telnet port. Over a 24-hour period there were tens of thousands of attempted connections from unique IP addresses,” researchers wrote in a report published today on Securelist.com.
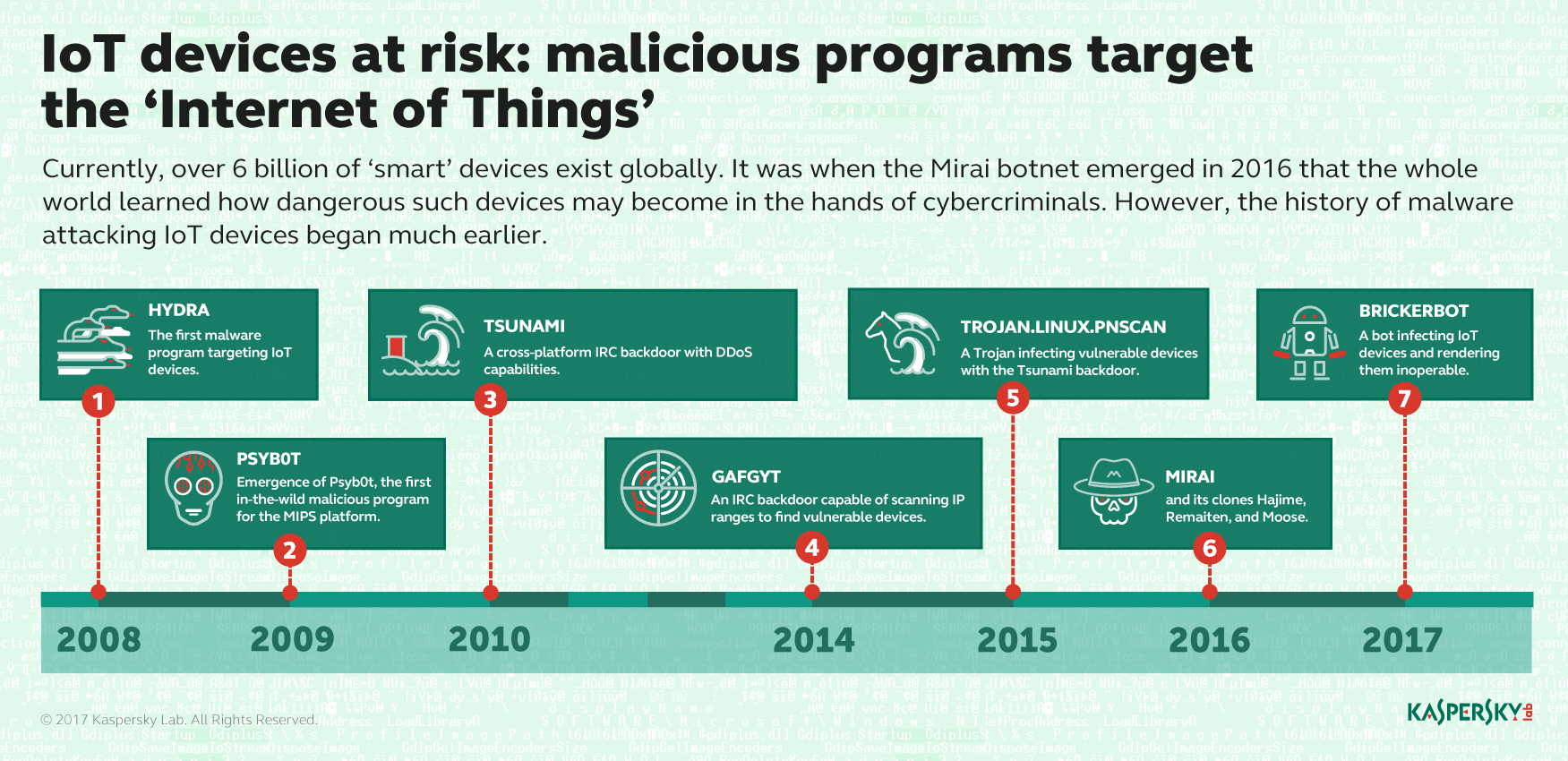
Mirai showed cybercriminals the way last fall, using malware to corral DVRs, IP-enabled cameras and home networking gear into a giant IoT botnet that was used to DDoS a number of high-profile targets. The malware spawned a number of variants and copycats, including the destructive BrickerBot malware family that bricks vulnerable IoT devices running with telnet exposed to the internet with default passwords.
While Kaspersky Lab laid out other risks to running insecure IoT devices such as the co-opting of a home network for illegal activities, most victimized devices are joined to a botnet of similarly infected things.
“The growing number of malware programs targeting IoT devices and related security incidents demonstrates how serious the problem of smart device security is. 2016 has shown that these threats are not just conceptual but are in fact very real,” the researchers wrote. “The existing competition in the DDoS market drives cybercriminals to look for new resources to launch increasingly powerful attacks.”
Given the millions of connected devices running, in addition to exposed telnet and SSH ports, weak or known default credentials, the issue is going to exponentially get worse. This is largely because many of these devices are leaving the manufacturer in a weak state, and even if firmware updates are made available, few devices have an automated update mechanism.
In addition, some devices that do offer remote management capabilities over TR-069, implement the protocol in an insecure manner, Kaspersky Lab said.
“This protocol is designed for the operator to remotely manage devices, and is based on SOAP which, in turn, uses the XML format to communicate commands,” the researchers wrote. “A vulnerability was detected within the command parser.”
The massive Deutsche Telekom attack of last November that affected 900,000 DSL router customers’ Internet, phone and video services was enabled by the TR-069 vulnerability. Attackers can exploit the issue and cause a device to download and execute an attack that, in this case, prevented the routers from resolving domains. The vigilante Hajime malware behaves similarly to Mirai, but has no malicious functionality. It also exploited the TR-069 vulnerability, but only to self propagate and close down exposed telnet ports used by Mirai.
In addition, Kaspersky Lab also cited lousy default admin passwords that are, in many cases, the same not only for a particular model, but across a manufacturer’s product line. Many of the passwords are known, easily guessable, or have been exposed in other data breaches and password leaks. Kaspersky Lab published a long list of default and popular credential combinations used by malware to access connected devices, including those used against telnet and SSH ports.
Meanwhile, most of the attacks captured in Kaspersky’s honeypot were coming from DVRs or IP cameras (63 percent), by a wide margin over networking devices and other unrecognized devices.
As for sources, the IP addresses attacking the Kaspersky honeypot were from diverse geographies, with China, Vietnam, Russia, Brazil and Turkey leading the way. Kaspersky said in 2017 it has detected more than two million attempts from more than 11,000 unique IP addresses, most of those in Vietnam, Taiwan and Brazil.
“The Mirai botnet has shown that smart devices can be harnessed for this purpose – already today, there are billions of these devices globally, and by 2020 their number will grow to 20-50 billion devices, according to predictions by analysts at different companies,” researchers wrote.