A botnet, which is adding new bots every day, has already infected one million businesses during the past month and could easily eclipse the size and devastation caused by Mirai.
The malware and botnet, dubbed IOTroop, was spotted in September by researchers at Check Point who warn that 60 percent of corporate networks have at least one vulnerable device.
Similar to Mirai, the malware targets poorly protected network-connected devices such as routers and wireless IP cameras manufactured by D-Link, TP-Link, Avtech, Netgear, MikroTik, Linksys, Synology and GoAhead.
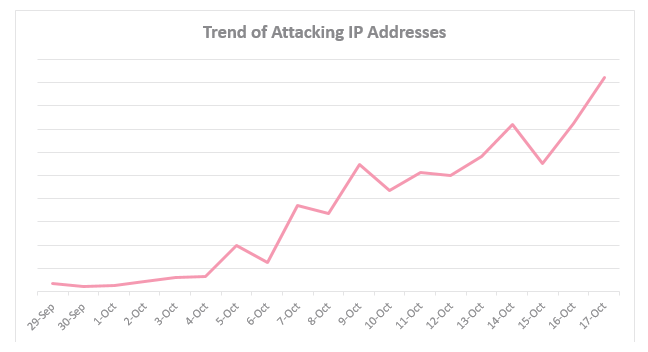
“So far we estimate over a million organizations have already been affected worldwide, including the U.S., Australia and everywhere in between, and the number is only increasing,” according to Check Point’s preliminary research published Thursday.
While this malware appears to share some of Mirai’s code, it is new malware and campaign, said Maya Horowitz, group manager of threat intelligence at Check Point, in an interview with Threatpost.
“This has the potential to be more damaging than Mirai,” Horowitz said. “This is malware that has a much broader range of vulnerabilities to target across a much larger spectrum of products,” she said.
In October 2016, Mirai malware spread itself to IoT devices gaining access via default password and usernames. The malware then roped affected devices into a botnet and carried out distributed denial of service (DDoS) attacks. The largest of such attacks flooded DNS provider Dyn causing several well-known websites to go dark for hours.
Horowitz said the IOTroop malware Check Point is examining has similarities to Mirai, such as the recruiting of a global army of network devices capable of launching crippling DDoS attacks.
“The most interesting difference between this malware and Mirai is that it is far more sophisticated. Attackers are not just exploiting default credentials to compromise devices, but also using a dozen or more vulnerabilities to get on these devices,” she said.
In the case of the GoAhead wireless IP camera, attackers exploited a well known bypass authentication vulnerability (CVE-2017-8225) identified in March and affecting more than 1,250 camera models. For other devices such as Linksys RangePlus WRT110 Wireless Router, adversaries are exploiting a remote command execution vulnerability known since 2014. This vulnerability exists because the router’s web interface fails to sanitize ping targets and lacks the use of cross-site request forgery tokens for protection.
Researchers said they have also identified several command-and-control servers used by adversaries behind the malware that update it with ranges of IP addresses to attack.
“Every infected device gets a range of IP addresses that are used to scan for these dozen or so vulnerabilities,” Horowitz said. “The malware is mostly self-propagating, with minimal C2 intervention. But we are still studying the malware and reverse engineering it to better understand how it works.”
“While we don’t have the completed answers, we do know that the infected devices get a range of IP addresses that the malware is instructed to check for vulnerabilities. And then the IPs of the vulnerable devices are sent back to the C2,” she said.
Researchers believe that the botnet is quickly amassing and may be on the cusp of a massive DDoS attack. “Our research suggests we are now experiencing the calm before an even more powerful storm,” wrote researchers.
Still unknown is who are the threat actors behind the malware/botnet, any targets hackers might have and what the timeline of any attack might be.
“It is too early to assess the intentions of the threat actors behind it, but it is vital to have the proper preparations and defense mechanisms in place before an attack strikes,” said researchers.