A freshly-discovered wiper malware dubbed “ZeroCleare” has been deployed to target the energy and industrial sectors in the Middle East.
According to IBM’s X-Force Incident Response and Intelligence Services (IRIS), ZeroCleare (so-named because of the program database pathname of its binary file) was involved in a recently spotted APT attack on an oil and gas company, in which it compromised a Windows machine via a vulnerable driver. ZeroCleare then pivoted to spread to other devices on the network – setting up the groundwork for a potentially catastrophic attack.
While an IRIS spokesperson told Threatpost that the exact number of organizations that were impacted is unknown, at least 1,400 hosts were affected by ZeroCleare.
“The attack most likely started in Autumn of 2018 with reconnaissance scanning from various low-cost/free VPN providers and gaining access to one of the accounts that was later involved in the attack,” said the spokesperson. “During the summer of 2019, the attackers then used a password spray from a system on the local network to gain access to additional accounts, install ASPX webshells and gain domain administration privileges.”
IRIS analysis showed that ZeroCleare shares certain characteristics with the infamous Shamoon malware in that it overwrites the master boot record (MBR) and disk partitions on Windows-based machines, using a legitimate utility. This renders infected machines inoperable.
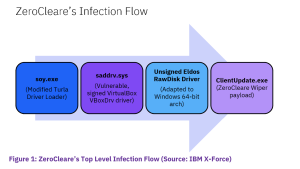
“As Shamoon did before it, the tool of choice in the attacks is EldoS RawDisk, a legitimate toolkit for interacting with files, disks and partitions,” according to an analysis, posted on Wednesday. “Nation-state groups and cybercriminals frequently use legitimate tools in ways that a vendor did not intend to accomplish malicious or destructive activity.”
The vulnerable driver was used to bypass the Windows operating system safeguards that prevent unsigned drivers from running on 64-bit machines – a control that is designed to only allow drivers which have been signed by Microsoft to run on the device.
“Since ZeroCleare relies on the EldoS RawDisk driver, which is not a signed driver and would therefore not run by default, the attackers use an intermediary file named soy.exe to perform the workaround,” according to the analysis. “They load a vulnerable but signed VBoxDrv driver, which the Driver Signature Enforcement (DSE) accepts and runs, and then exploit it to load the unsigned driver, thereby avoiding DSE rejection of the EldoS driver.”
Post-exploitation, the driver was used to load the unsigned EldoS driver and proceed to the destructive phase. At the same time, the adversaries brute-forced passwords to gain access to several network accounts, which were used to install the China Chopper and Tunna web shells after exploiting a SharePoint vulnerability, according the firm.
Also, the attackers attempted to leverage legitimate remote-access software, such as TeamViewer, and used an obfuscated version of Mimikatz to collect credentials from compromised servers.
Iranian Links
ZeroCleare is likely the work of Iran-based nation-state adversaries, according to researchers – specifically, APT34 (a.k.a. OilRig or ITG13). APT34 likely also collaborated on the destructive portion of the ZeroCleare attack with at least one other group, researchers found.
“X-Force IRIS’s assessment is based on ITG13’s traditional mission, which has not included executing destructive cyberattacks in the past, the gap in time between the initial access facilitated by ITG13 and the last stage of the intrusion, as well as the different [tactics, techniques and procedures] our team observed,” the firm said.
More specifically, for initial access, the IP address 193.111.152[.]13, which is associated with recent APT34 efforts, was used to scan target networks and access accounts in the first phase of the attack. In later phases, another IP address joined the fray, 194.187.249[.]103, which is adjacent to another IP address, 194.187.249[.]102.
“The latter was used several months prior to the attack by the threat actor Hive0081 (a.k.a. xHunt),” IRIS noted.
Threatpost has reached out to IRIS for more details on the targets and result of the ZeroCleare attack.
Destructive Attacks on the Rise
Wiper attacks – which focus on destroying infrastructure and disrupting operations rather than on data exfiltration – have been on the rise in 2019, with IRIS observing a 200-percent increase in their telemetry over the past six months.
“The destructive attacks we have seen are being carried out by threat actors of varying motivations who could be employing destructive components in their attacks,” according to the analysis. “Some pressure victims to pay them, others counterblow when they are not paid. When these attacks are carried out by nation-state adversaries, they often have military objectives that can include accessing systems to deny access to, degrade, disrupt, deceive or destroy devices and/or data.”
Essentially, these types of attacks can be carried out in lieu of conventional military tactics, IRIS said.
“It presents Iran, in this case, with a low-cost and potentially nonattributable means of conducting hostile and even warlike activities,” according to the analysis. “With attribution to one specific group becoming a challenge nowadays, working under the cyber cloak of anonymity can also allow Iran to evade sanctions and preserve its relations with international players who may support its economic and nuclear energy interests.”
Free Threatpost Webinar: Risk around third-party vendors is real and can lead to data disasters. We rely on third-party vendors, but that doesn’t mean forfeiting security. Join us on Dec. 18th at 2 pm EST as Threatpost looks at managing third-party relationship risks with industry experts Dr. Larry Ponemon, of Ponemon Institute; Harlan Carvey, with Digital Guardian and Flashpoint’s Lance James. Click here to register.