The Department of Homeland Security is warning that Iranian hackers are targeting U.S. agencies with destructive “wiper” malware. The statement comes as tensions continue to build between the U.S. and Iran.
Christopher Krebs, the director of the Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency, over the weekend warned of a recent rise in Iranian malicious cyber activity directed at the U.S.
Krebs warned that Iranian “regime actors and proxies” are targeting U.S. industries and governments with destructive wiper malware – which have the singular purpose of destroying systems or data, usually causing great financial and reputational damage to victim companies.
“Iranian regime actors and proxies are increasingly using destructive ‘wiper’ attacks, looking to do much more than just steal data and money,” said Krebs in a statement. “These efforts are often enabled through common tactics like spear phishing, password spraying, and credential stuffing. What might start as an account compromise, where you think you might just lose data, can quickly become a situation where you’ve lost your whole network.”
Escalating Tensions
The warning comes as cyberactivity between the U.S. and Iran continues to heighten.
After Iran downed a U.S. surveillance drone last week, U.S. military cyber forces responded by launching a cyberattack against Iranian military computer systems, disabling computer systems that controlled Iranian rocket and missile launchers, according to Yahoo News.
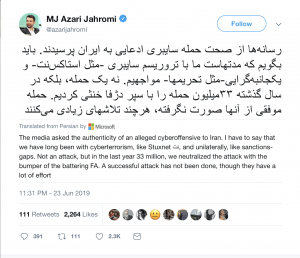
Iran’s minister for information and communications technology, Mohammad Javad Azari Jahromi, claimed Sunday on Twitter that U.S. cyberattacks against Iran have been unsuccessful.
Meanwhile, multiple U.S. cyber intelligence firms have reported that they were targeting by Iranian hackers over the past week. A wave of spear phishing emails was reportedly sent to targets in the U.S. government, as well as the finance, gas and oil markets, according to the Associated Press.
Crowdstrike and FireEye have attributed this phishing campaign to APT33 (also known as Magnallium or Refined Kitten), a well-known threat group that has been behind cyberespionage campaigns in 2017 and is known for its use of destructive malware.
The campaign reportedly began after the Trump administration imposed sanctions on the Iranian petrochemical sector earlier this month, according to the AP.
“The digital strike against Iran is a great example of using Cyber Command as a Special Ops force, clearly projecting US power by going deep behind enemy lines to knock out the adversary’s intelligence and command-and-control apparatus,” Phil Neray, VP of industrial cybersecurity for CyberX said in an email.
Wipers
Wipers are a dangerous type of malware. Wiper malware, including Shamoon, Black Energy, Destover, ExPetr/Not Petya and Olympic Destroyer, are bent on total destruction – as opposed to stealing data or financial information – creating more damage or victims.
APT33 has previously utilized a dropper called DropShot, tied to the StoneDrill wiper malware—a variant of the infamous Shamoon 2, according to a 2017 FireEye report.
Krebs stressed that U.S. agencies should make sure they have shored up their basic defenses (such as multi-factor authentication).
“We will continue to work with our intelligence community and cybersecurity partners to monitor Iranian cyber activity, share information, and take steps to keep America and our allies safe,” he said.