SAN FRANCISCO – A never before seen credential-stealing malware, dubbed ForeLord, has been uncovered in recent spear phishing emails. Researchers have attributed the campaign to a known Iranian advanced persistence threat (APT) group.
The emails distributing ForeLord were uncovered as part of a campaign, running between mid-2019 and mid-January 2020. The emails were targeting organizations in Turkey, Jordan, Iraq, as well as global government organizations and unknown entities in Georgia and Azerbaijan, researchers said Wednesday at the RSA Conference, which takes place this week.
Citing victimology and code similarity between the macros in analyzed samples, and macros documented in open-source reporting, researchers have attributed the campaign to the Cobalt Ulster threat group (also known as MuddyWater, Seedworm, TEMP.Zagros, and Static Kitten). This APT group has historically targeted government victims in the Middle East to exfiltrate data.
“Cobalt Ulster is an active threat group whose operations are continuous. We believe this adversary is still actively working towards achieving their strategic objectives,” Allison Wikoff, senior security researcher at Secureworks told Threatpost.
As part of the campaign, researchers observed multiple emails using malicious attachments to gain initial access. While historically spear phishing emails by Cobalt Ulster use a government agency, university or intelligence organization-related theme as a hook, this most recent campaign used a “more generic style,” researchers said.
“It was generic in the sense that we have observed numerous threat groups, targeted and commodity, use the tactic observed in the lures,” Wikoff told Threatpost. “Specifically, this tactic employs a generic ‘Enable Macro’ prompt to view the document contents. If the victim does this, the malicious code is executed. This tactic is not unique to Cobalt Ulster.”
Victims are asked to open a ZIP archive containing a malicious Excel file, which then requests that they enable content to view the document. Once they enable the content, security controls were disabled and embedded malicious code was run in the victims’ systems.
The malicious document uses command prompt (cmd.exe) to execute a batch script, which then adds a key to the registry for persistence. Simultaneously, a PowerShell script is executed and uses rundll.32 (a Windows tool that runs program code in DLL files as if they were within the actual program; many viruses also use this name or similar ones) to execute the ForeLord malware. ForeLord is so named because once the malware connects to the command and control (C2) servers, it receives a string of code that says “lordlordlordlord,” indicating that its messages have been received by the C2.
Once downloaded, ForeLord drops several tools used to collect credentials, test those credentials on the network, and create a reverse SSL tunnel to provide an additional access channel to the network.
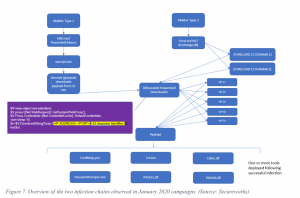 The malware also makes unique use of a legitimate tool called CredNinja.Ps1, an open-source tool that allows penetration testers to quickly test collected credentials or hashes to determine which will work on a targeted Windows domain.
The malware also makes unique use of a legitimate tool called CredNinja.Ps1, an open-source tool that allows penetration testers to quickly test collected credentials or hashes to determine which will work on a targeted Windows domain.
“The threat actors used a list of valid user accounts from the target domain in conjunction with a weak password list to determine potentially accessible accounts,” said researchers. “The password list could be augmented to test credentials captured from credential-dumping tools.”
Researchers say that in spite of Iran’s threatened retaliation for recent geopolitical events, this campaign indicates that Iranian APTs continue to focus on “long-running cyberespionage activity.” Conflict between the U.S. and Iran peaked after U.S. drones on Jan. 3 killed Qassem Soleimani, an Iranian general with the Islamic Revolutionary Guard Corps who was highly-esteemed in Iran. On the heels of Soleimani’s killing, Iranian leaders vowed retaliation. A U.S. government website was vandalized in January by hackers who posted images of a bloodied President Donald Trump being punched in the face and pro-Iran messages.
However, while researchers say that though Iran has not launched a cyber retaliation for Soleimani’s death, they acknowledge that planning and coordinating for a response takes time.
“From a threat management and risk assessment perspective, CTU researchers advise organizations not to conflate ongoing espionage operations with a retaliatory response,” said researchers. “However, continually leveraging threat intelligence to assess and improve controls will help network defenders secure their environments against malicious activity regardless of intent.”
For all Threatpost’s RSA Conference 2020 coverage, please visit our special coverage section, available here.











