The Ke3chang cyberespionage group, a.k.a. APT15, Mirage, Playful Dragon or Vixen Panda, has been tied to a backdoor called Okrum that has been used to target diplomatic missions throughout Europe and Latin America.
The attribution widens the scope of known Ke3chang activity, an APT believed to be operating from China.
Ke3change first appeared in 2010, making a name for itself by developing simple but custom malware like the BS2005/Ketrican backdoors and the RoyalDNS malware and deploying it in what was dubbed “Operation Ke3chang.” Almost 10 years later, the group continues to be active according to ESET, using revamped versions of BS2005/Ketrican.
Connecting the Dots
In 2015, Ke3chang made a splash by continuing its previous Operation Ke3chang attacks that centered around Slovakia, using the BS2005/Ketrican backdoor family.
The following year, ESET discovered Okrum, focused on the same type of targets: Diplomatic missions in Slovakia, Belgium, Chile, Guatemala and Brazil, with the attackers showing a particular interest in Slovakia. The attackers were also seen using a related TidePool malware family discovered by Palo Alto Networks that targeted Indian embassies across the globe.
The Okrum activity continued through 2017 and the ESET team has been able to tie it back to Ke3chang, with Okrum observed acting as a first-stage malware that then fetched Ketrican samples to install on a compromised machine.
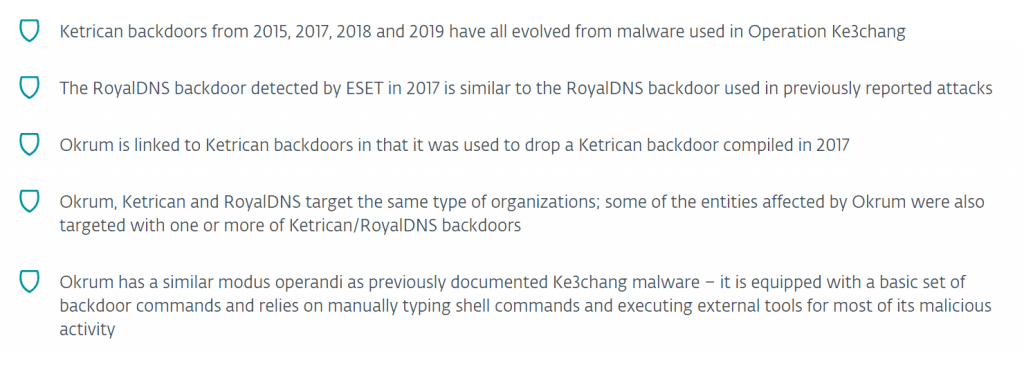
“Our research has shown that the Ketrican, Okrum and RoyalDNS backdoors detected by ESET after 2015 are linked to previously documented Ke3chang group activity, and to each other, in a number of ways,” said ESET researcher Zuzana Hromcová, in an analysis [PDF] posted on Thursday. “[Since then], Ketrican backdoors from 2015, 2017, 2018 and 2019 have all evolved from malware used in Operation Ke3chang.”
ESET laid out the ties in its analysis:
Okrum
The Okrum backdoor, which hasn’t been previously documented publicly, is installed and loaded by two earlier-stage loaders that change frequently in an effort to evade detection, according to ESET.
The actual Okrum payload — an encrypted malicious DLL – uses steganography to slip past defenses, hiding and embedding itself in an innocuous-looking PNG image.
“When the file is viewed in an image viewer, a familiar image is displayed, but the Okrum loaders are able to locate an extra encrypted file that the user cannot see,” Hromcová said.
Okrum is only equipped with basic backdoor commands, such as downloading and uploading files, executing files and shell commands, according to ESET.
“Most of the malicious activity has to be performed by typing shell commands manually, or by executing other tools and software [such as a keylogger, tools for dumping passwords or enumerating network sessions],” said the researcher. “This is a common practice of the Ke3chang group,” she added, noting that the Ketrican backdoors also use similar external utilities, perhaps in an attempt to evade behavioral detection.
What remains to be answered, she added, is how the malware was distributed to the victim machines.
ESET noted that, though Okrum is not technically complex, the fact that the malicious actors behind it tried to remain undetected with novel approaches, along with the visible evolution and code improvements from 2015 to 2019 in Ketrican, show that the Ke3chang APT group is in it for the long haul.
“The Ke3chang APT group (a.k.a. APT15) has rightfully been on the radar of security researchers because of its decade-long operation, targeting high-value victims such as diplomatic entities, and other geopolitical aspects associated with them,” according to the analysis.
Interested in more on patch management? Don’t miss our free live Threatpost webinar, “Streamlining Patch Management,” on Wed., July 24, at 2:00 p.m. EDT. Please join Threatpost editor Tom Spring and a panel of patch experts as they discuss the latest trends in Patch Management, how to find the right solution for your business and what the biggest challenges are when it comes to deploying a program. Register and Learn More