The Kronos banking trojan is back from the malware dustbin. After years of lying dormant, hackers have reworked the underlying code and are actively targeting victims in Germany, Japan and Poland.
The latest variant has incorporated a new command-and-control feature designed to work with the Tor anonymizing network, according to an analysis by Proofpoint researchers published Tuesday.
They believe that Kronos has been not only retooled, but may also have been rebranded as Osiris. That’s the name some criminals are using for a nearly identical trojan being sold on underground markets.
“While there is significant evidence that this malware is a new version or variant of Kronos, there is also some circumstantial evidence suggesting it has been rebranded and is being sold as the Osiris banking trojan,” Proofpoint said. The name would be apt: Osiris is the Egyptian god of rebirth.
Since June 27, researchers said they have observed four distinct campaigns containing malicious files that eventually lead to the downloading of the Kronos/Osiris trojan.
The Kronos banking trojan was first discovered in 2014 and quickly made a name for itself as an adept malware capable of stealing credentials and using web injects for banking websites. The trojan also included a Ring3 rootkit to help defend it against other trojans. But in 2016, the once-formidable banking trojan dropped off researchers’ radar screen.
In 2017, Kronos once again made headlines when the Federal Bureau of Investigation accused WannaCry-slayer Marcus Hutchins of building the banking trojan — but actual activity of the malware remained limited.
Now, recent malware-laced spam campaigns in Germany have targeted customers of financial firms with email subject lines that translate into English as “Updating our terms and conditions.” In these offensives, malware samples used the URL “http://jhrppbnh4d674kzh[.]onion/kpanel/connect.php” as its C&C.
“The Word documents contained macros that, if enabled, downloaded and executed a new variant of the Kronos banking trojan. In some cases, the attack used an intermediate smoke-loader,” researchers wrote. A smoke-loader is the name of a small application typically used to download additional malware in an attack.
In Japan, attacks observed in the July 15-16 timeframe were malvertising-based. “[W]e investigated a malvertising chain sending victims to a site containing malicious JavaScript injections,” analysts said. “This JavaScript redirected victims to the RIG exploit kit, which was distributing the smoke-loader downloader malware.”
In Poland on July 15 and 16, attackers used emails with malicious and fake invoice attachments, Proofpoint said. In this campaign, attackers used attachments to exploit the Microsoft Equation Editor vulnerability (CVE-2017-11882) patched last year.
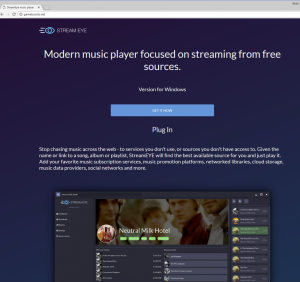
Proofpoint observed a fourth work-in-progress campaign on July 20 that appeared to use an English-language music-streaming website to lure victims.
“We are not yet aware of the exact vector for this campaign, but this instance of Kronos is configured to use hxxp://mysmo35wlwhrkeez[.]onion/kpanel/connect.php as its C&C, and could be downloaded by clicking on the “Get It Now” button of a website claiming to be a streaming music player,” researchers noted.
An analysis of this recent Kronos sample reveals ties to past versions such as the same string encryption technique; the same Windows API hashing technique and hashes; and the same C&C protocol and encryption. The malware code string also contains the self-identifying “Kronos.”
Use of the anonymizing Onion service is new. Researchers also note that current samples have adopted key-logger functionality similar to what they would expect to find with the Zeus Panda banking trojan. Also similar to Zeus were web-inject implementations into the malware.










