UPDATE: Updated with comment and clarification from Google.
Researchers say that Google’s Gmail application for iOS fails to perform a task called certificate pinning under certain conditions, which could expose the users of affected devices to man-in-the-middle attacks capable of monitoring encrypted email communications.
Google told Threatpost in an email interview that this research does not constitute a vulnerability in the Gmail application because of the level of user interaction required to trigger an exploit.
Certificate pinning is a process designed to prevent attacks enabled by spoofing a back-end server’s SSL certificate. In this case, the back-end server would belong to Google. When certificate pinning is deployed, the specific certificate used by the app sending the message is double-checked upon receipt. When Certificate pinning is not deployed, the recipient merely checks that the app sending the message is using a trusted certificate.
Lacoon Security said it reported the vulnerability to Google on Feb. 24. Lacoon Security said Google acknowledged the bug told the company it was fixed. Lacoon’s Avi Bashan, however, says that the security vulnerability remains exploitable in Gmail’s iOS app.
“Several months after providing responsible disclosure, Google has not provided information regarding resolution and it still remains an open vulnerability,” said Michael Shaulov, CEO and co-founder of Lacoon Mobile Security. “This vulnerability leaves iPhone and iPad users at risk of a threat actor being able to view and modify encrypted communications through a Man-in-the-Middle attack”
For its part, Google doesn’t consider this a vulnerability.
“This is not a vulnerability in the Gmail app,” a Google spokesperson told Threatpost. “The scenario that Lacoon raises would require a user to take explicit action — specifically, purposefully installing a malicious Root Certificate Authority that gives a hacker access to their app. Messages you send through Gmail app on iOS are safely transferred through Google’s servers unless you’ve intentionally reconfigured your device.”
The alleged vulnerability does not affect Gmail applications on Google’s Android or any other operating system. Nor does it impact Gmail users that access their email on iOS through Apple’s Mail application.
Bashan claims Lacoon unexpectedly found the bug during an ongoing analysis of security on Apple’s iOS mobile platform. He claims an attacker could perform a MitM without any indication to the victim.
“We were quite surprised by this finding because Google had implemented certificate pinning for their Android Gmail app,” Bashan wrote. “Clearly, not implementing this for iOS was an oversight by Google.”
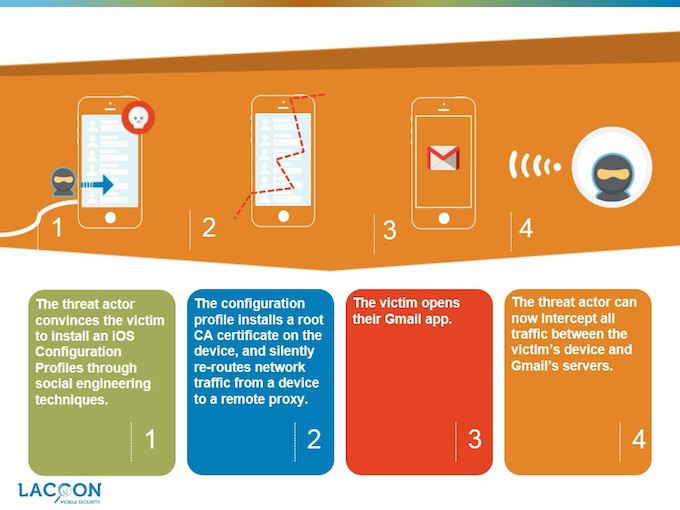
Per Lacoon’s explanation, the following four steps are required to exploit this vulnerability to create a MitM:
-
Hacker tricks victim into installing a configuration profile containing the root certificate and the details of the server to reroute the traffic to. (Note: to do this, a threat actor can use a variety of social engineering methods such as sending an email, purportedly from the IT department, requesting to install the configuration profile.)
-
Reroutes victim’s traffic through the server under the threat actor’s control, defined by the malicious configuration profile.
-
Creates spoofed certificates which are identified as valid by the victim’s device.
-
Intercepts all traffic between the attacked device and intended server.
Collin Mulliner, a researcher at the SecLab at Northeastern University, confirmed to Threatpost in an email that the attack would work, but called it impractical because the victim would have to install the iOS configuration profile.
“If you require actual user interaction to perform an attack it gets harder,” Mulliner said. “Also no automated attacks are possible here, you cannot just intercept traffic of any device but first have to target each user to have them install the ‘bad’ configuration file.”