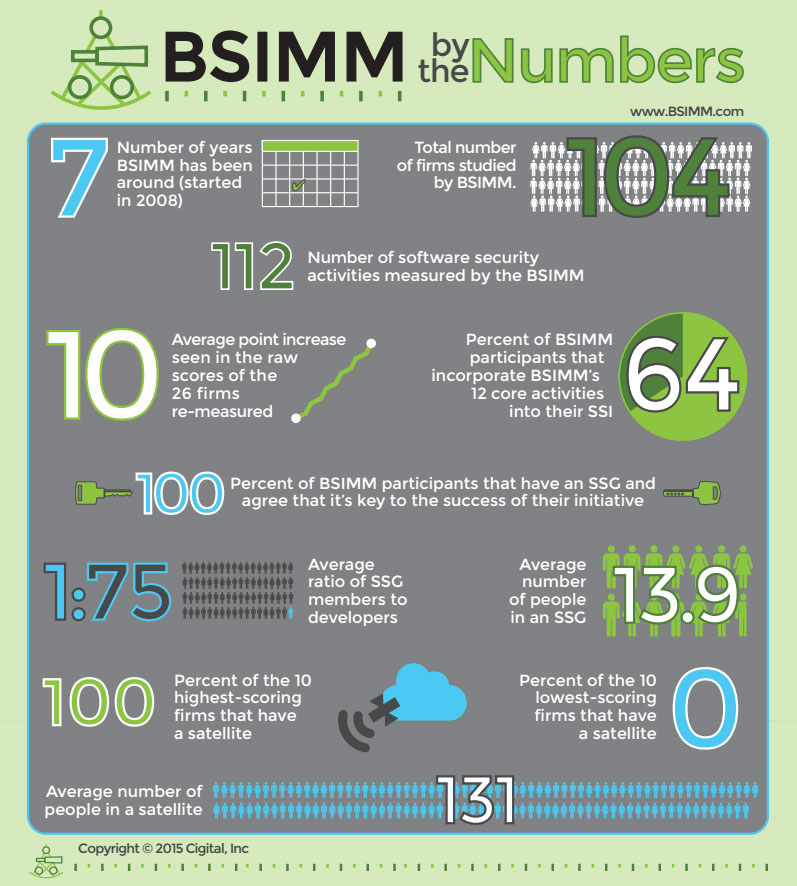
The folks behind the Building Security in Maturity Model (BSIMM), its sixth iteration available today, tout the project as an intersection between science and computer security.
“It’s more like a science experiment that escaped the test tube,” said Gary McGraw, chief technology officer of Citigal, which in 1999 along with Fortify Software, got BSIMM off the ground.
The science is that the framework is used to measure observable software security practices in a dozen core areas, based on interviews with an organization’s top software security person, and those reporting to that executive.
Through now six versions, McGraw said there is a significant set of trending data that participating organizations can use to assess the continuing effectiveness of their programs, while others can evaluate their own practices against peer organizations.
“When you have a measurement that is objective and scientific, and can take that to senior executives and say ‘Here is our space compared to the rest of the world,’ we’re not seeing them get mad,” McGraw said. “They say they must fix it, make investments and work hard to solve the problem.”
BSIMM, which began with measurements of nine participants against nine software security practice areas, now contains data on 104 organizations including very large software vendors (Adobe, Cisco and EMC among many others), financial institutions (Bank of America, JP Morgan and others), and for the first time 10 health care organizations and consumer electronics outfits, or vendors in the so-called Internet of Things space.
Some powerful health care organizations participated, including Aetna, McKesson and Zephyr Health, but the relative maturity of the software security programs at these organizations is low, the results show. In the context of a number of events, including the continuing transition to electronic health records and a growing tide of breaches at Anthem, Community Health, CareFirst Blue Cross and others, these organizations are already under pressure to catch up.
“I’ve spoken to many board members and senior health care executives directly and I think in the beginning, the entire space was misled by HIPAA [Health Insurance Portability and Accountability Act]. When HIPAA came out, it got them to start thinking about patient privacy and protecting patient data and when they did that, they thought they were done,” McGraw said.
An encouraging trend in health care information security, McGraw said, is that a number of security executives who thrived and grew mature programs in financial services are starting to take new opportunities in health care.
“When these senior executives came in they made it clear that security is a lot more complicated than protecting data and filling out forms that people never read,” McGraw said. “Instead, if you want to get out in front of the problem, you have to build systems that are secure in the first place.”
The first BSIMM health care measurement shows that health care is starting at the bottom, well behind leading organizations in the ISV and financial vertical markets, and even IoT. The lag is in all four domains BSIMM measures: governance; intelligence; SSDL touchpoints; and deployment. Under each domain, there are three practice areas that are measured; 112 activities in all.
“Health care is falling short in all 12 practices we report on; in all 12 it’s behind the average,” McGraw said. McGraw said that ISVs, Microsoft in particular behind Trustworthy Computing in the early 2000s, led the way in defining and refining software security practices. Financial services firms, he said, quickly caught up and to this day remain ahead of the field. Health care, McGraw is confident, will catch up in a similar fashion.
“That is an opportunity and senior executives in the health care space know it’s an opportunity. We are not criticizing, but pointing out the state of how their world is instead. It’s time to start fixing it.”