The Petya ransomware strain signaled a new escalation for crypto-malware when it surfaced in March. For the first time, ransomware went beyond encrypting files on local and shared drives and instead set its sights on locking up the Master File Table on compromised machines.
Petya did have its shortcomings and before long, researchers were able to develop a tool that recovered some files lost to infections.
The criminals behind Petya, meanwhile, have addressed another weakness where the malware would not execute if it were not granted administrative privileges in order to target the MFT. A new installer for Petya was found and disclosed on Thursday. It comes with a failsafe; if its installer is not granted the privileges it seeks, it instead installs another strain of ransomware known as Mischa.
The original Petya executable came with a manifest that requested administrator privileges, said researcher Lawrence Abrams of Bleeping Computer.
“This causes Windows to issue a UAC prompt and request these privileges before the code in the executable is actually run. If the victim has UAC disabled, the program will just automatically run with [admin privileges],” Abrams told Threatpost. “This also means that if the user said ‘No’ at the UAC prompt, the program would not run and thus not install Petya.”
Abrams said the Petya gang was “leaving money on the table” in the form of these failed installations. Their counter was the bundle Mischa ransomware into the installer that would execute if Petya failed.
The new version’s manifest states that it will run under the user’s security credentials, Abrams said. Windows then allows the program to start without a UAC prompt.
“When the installer starts, it will programmatically request Administrator privileges. This will cause a UAC prompt to appear and if the user presses ‘Yes’ at the UAC prompt, or UAC is disabled, and it gains admin privileges it goes ahead and installs Petya,” Abrams said. “On the other hand, if it does not get Admins privileges, it moves forward with installing Mischa. Pretty clever method.”
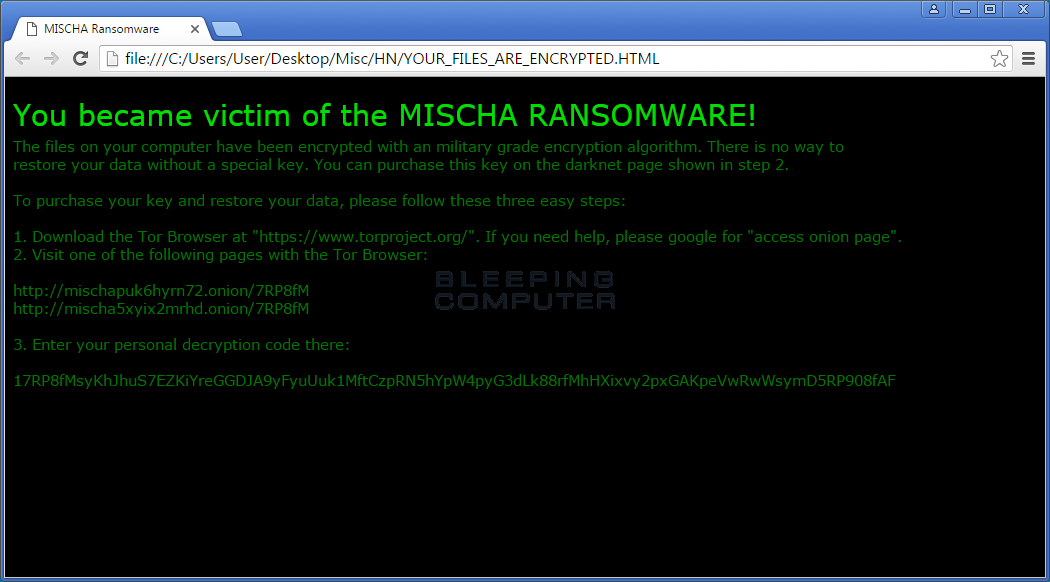
Mischa behaves like most of the ransomware many are familiar with. Once the victim executes link sent in a spam or phishing email, the malware encrypts local files and demands a ransom of 1.93 Bitcoin, or about $875 to recover the scrambled files.
Petya, meanwhile, continues to spread in Germany to enterprise HR organizations via emails with a link to a cloud file storage service purporting to be a job application. The original used Dropbox links that were ultimately disabled by Dropbox. The current campaign is sending victims to files stored on Germany’s TelekomCloud service. The malicious file contains an image of the applicant and a download that starts with PDF, such as PDFBewerbungsmappe.exe, Abrams said.
“When a victim downloads the executable, it will have a PDF icon to make it appear as a PDF resume,” Abrams said. “This executable, though, when started tries to install Petya, and if that fails, installs the Mischa ransomware.”
Mischa scans the local drive for certain data files and encrypts them with AES. The files are also appended with a four-character extension, such as 7GP3, he said.
“While encrypting a file Mischa will store the encrypted decryption key at the end of the encrypted file,” Abrams said. “An annoying aspect of Mischa is that not only will it encrypt your standard data file type (PNGs, JPGs, DOCXs, etc), but it will also encrypt .EXE files.”
The ransom must be paid in Bitcoin through a Tor payment site, Abrams said. The ransom note takes the victim to a payment wizard that explains how to buy Bitcoin and where to send the ransom.
Victims as of yet do not have a file decryptor available for Mischa infections.
“It is always suggested that you attempt to use Shadow Explorer to see if your Shadow Volume Copies are intact,” Abrams said. “These can then possibly be used to restore older versions of the encrypted files.”