Lazarus Group is using Windows Update to spray malware in a campaign powered by a GitHub command-and-control (C2) server, researchers have found.
On Thursday, the Malwarebytes Threat Intelligence team reported that they discovered the North Korean state advanced persistent threat (APT) group’s latest living-off-the-land technique while analyzing a spear-phishing campaign that its researchers discovered 10 days ago, on Jan. 18.
The focus of the campaign – in which the APT masqueraded as American global security and aerospace giant Lockheed Martin – is in keeping with Lazarus’ taste for infiltrating the military.
Researchers consider Lazarus, which has been active since at least 2009, to be one of the world’s most active threat actors. The United States also refers to Lazarus as Hidden Cobra: a name used to refer to malicious cyber-activity by the North Korean government in general. “This APT group has been behind large-scale cyber-espionage and ransomware campaigns and has been spotted attacking the defense industry and cryptocurrency markets,” Kaspersky researchers have noted in the past.
According to Malwarebytes’ Thursday report, the Jan. 18 spear-phishing campaign was weaponized with malicious documents that try to lure targets into clicking by using the same “job-opportunities” baloney that the group has dangled before.
Lazarus did the same thing last July: At that time, the APT was identified as being behind a campaign that was spreading malicious documents to job-seeking engineers, impersonating defense contractors who were purportedly seeking job candidates at Airbus, General Motors and Rheinmetall.
Malwarebytes found two such macro-embedded decoy documents, pretending to offer new job opportunities at Lockheed Martin, in the Jan. 18 campaign. Their filenames:
- Lockheed_Martin_JobOpportunities.docx
- Salary_Lockheed_Martin_job_opportunities_confidential.doc
Both of the documents had a compilation time of April 4, 2020, but Malwarebytes said that the campaign was actually used late last month and into this month, as indicated by the domains used by the threat actor.
It All Begins with Word
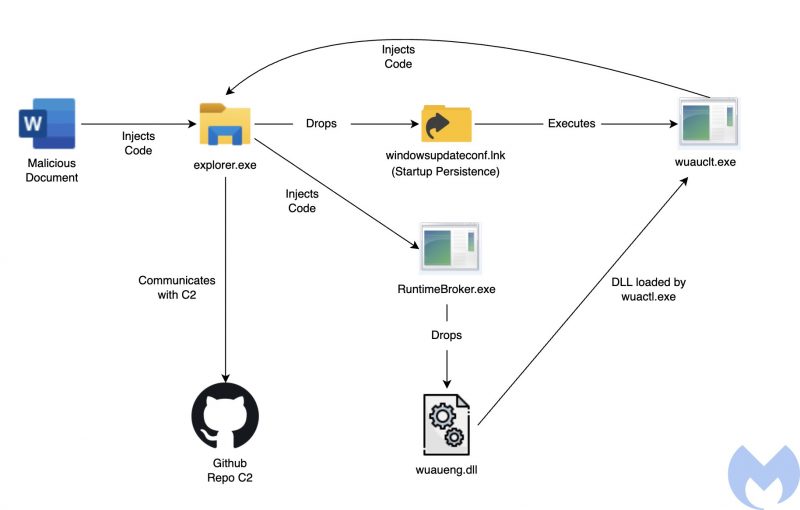
The attack starts by executing malicious macros embedded in the Word documents, researchers described. After a series of injections, the malware achieves startup persistence in the victim’s system.
After a target opens the malicious attachments and enables execution of macros, an embedded macro drops a WindowsUpdateConf.lnk file in the startup folder and a DLL file (wuaueng.dll) in a hidden Windows/System32 folder. LNK files are Windows shortcut files, as in, pointers to original files in Windows.
Next, the .LNK file is used to launch the WSUS / Windows Update client – wuauclt.exe, a legitimate process file popularly known as Windows automatic updates that’s located in C:\Windows\System32 by default. The Update client is used to run a malicious DLL that bypasses security detection.
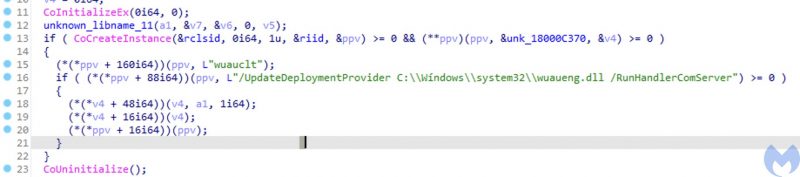
“With this method, the threat actor can execute its malicious code through the Microsoft Windows Update client by passing the following arguments: /UpdateDeploymentProvider, Path to malicious DLL and /RunHandlerComServer argument after the DLL,” the researchers explained.
Malware authors often create files with virus scripts and name them after wuauclt.exe. In fact, in October 2020, wuauclt.exe was added to the list of living off the land binaries (LOLBins): executables signed by Microsoft that attackers use to execute malicious code on Windows systems while evading detection.
“”This is an interesting technique used by Lazarus to run its malicious DLL using the Windows Update Client to bypass security detection mechanisms,” the threat-intelligence team noted. “With this method, the threat actor can execute its malicious code through the Microsoft Windows Update client by passing the following arguments: /UpdateDeploymentProvider, Path to malicious DLL and /RunHandlerComServer argument after the DLL.”
GitHub Used as C2 ‘Rarely’
Use of GitHub as a C2 is rare, the researchers observed, and this is the first time they’ve seen Lazarus doing so.
But it’s an apt choice for the task at hand, they said: “Using GitHub as a C2 has its own drawbacks but it is a clever choice for targeted and short term attacks as it makes it harder for security products to differentiate between legitimate and malicious connections.”
As for the rogue GitHub account being used as a C2 in the campaign, Malwarebytes Labs reported it “for harmful content,” according to its writeup.
Check out our free upcoming live and on-demand online town halls – unique, dynamic discussions with cybersecurity experts and the Threatpost community.