North Korea-linked APT Lazarus Group has been spotted targeting the cryptocurrency business again, adding Apple users to the mix by using PowerShell scripts to control macOS malware, and honing its Windows strategy.
The campaign has been active since at least November 2018, according to an analysis this week from Kaspersky Lab, which said that various malware payloads are being distributed via documents containing weaponized macros, “carefully prepared to attract the attention of cryptocurrency professionals.”
Some of the documents (for instance one entitled “sample document for business plan evaluation of venture company”) were prepared in Korean, presumably to target South Korean businesses. Another contains a business overview of what seems to be a Chinese technology consulting group named LAFIZ (“we couldn’t confirm if it’s a legitimate business or another fake company made up by Lazarus,” Kaspersky Lab researchers said). Yet another provided information for coin listings with a translation in Korean, researchers said.
The group is using custom PowerShell scripts to communicate with malicious command-and-control servers (C2s) that are hosted on compromised servers. The C2 server script names are disguised as WordPress and other popular open-source files, according to analysis.
“The malicious macro checks the victim’s OS, and if it runs on macOS, it downloads the payload from the remote server,” Seongsu Park, senior security researcher at Kaspersky Lab, told Threatpost. “The downloaded file is a mach-o type (macOS executable file) full-featured backdoor.”
On the Windows front, the payloads demonstrate that Lazarus keeps exploring more ways to evade detection.
“The group builds malware for 32-bit and 64-bit Windows separately to support both platforms and have more variety in terms of compiled code,” according to the analysis. “These Windows malware samples were delivered using malicious HWP (Korean Hangul Word Processor format) documents exploiting a known PostScript vulnerability. It should be noted that HWP documents are only popular among Korean users (Hangul Word Processor was developed in South Korea) and we have witnessed several attacks using the same method.”
The campaign also features an interesting infrastructure segregation, with C2 scripts only hosted on compromised servers.
“We have seen some legitimate-looking servers that are most likely compromised and used in malicious campaigns,” researchers noted in the posting. “According to server response headers, they are most likely running an old vulnerable instance of Internet Information Services (IIS) 6.0 on Microsoft Windows Server 2003.”
Meanwhile, another C2 server appears to have been purchased by Lazarus from a hosting company—Kaspersky Lab researchers said that this was used mainly to host macOS and Windows payloads.
“The significance of their C2 infrastructure is that they managed whole C2 servers in multi-stages,” Park explained. “They compromised legitimate web servers, and configured them as minimum second stage servers. This sort of configuration has a strength that the path can be easily reconfigured if one path is blocked.”
Park added that in general, the campaign is further evidence of Lazarus widening its net, and that it’s targeting whole business segments (especially cryptocurrency businesses) rather than individual users. He noted that therefore, both Windows and macOS users should be more cautious about falling victim to Lazarus.
“If you’re part of the booming cryptocurrency or technological startup industry, exercise extra caution when dealing with new third parties or installing software on your systems,” Park said. “It’s best to check new software with an antivirus or at least use popular free virus-scanning services such as VirusTotal. And never ‘Enable Content’ (macro scripting) in Microsoft Office documents received from new or untrusted sources. Avoid being infected by fake or backdoored software from Lazarus – if you need to try out new applications, it’s better do so offline or on an isolated network virtual machine which you can erase with a few clicks.”
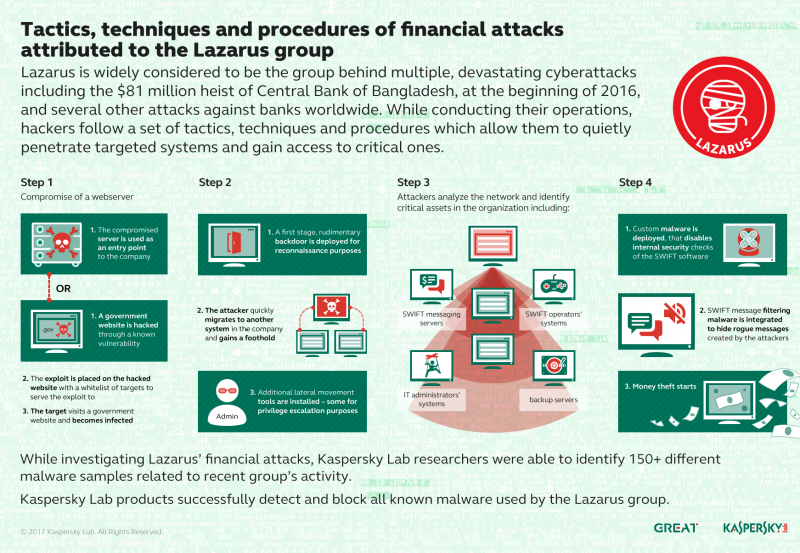
Since at least 2016, Lazarus has been devoting a portion of its resources to going after financial institutions, casinos, financial trade software development companies and cryptocurrency businesses, including the high-profile attack against the Bangladesh Central bank that resulted in more than $850 million in fraudulent SWIFT network transactions.
As an instrument of the North Korean regime, Lazarus is acting to both fund its own operations as well as seek revenue for its government, Kaspersky analysts have said in prior analysis: