Recent document-based attacks have leveraged malicious macros that if enabled install malware. But, researchers at SensePost have developed a proof-of-concept attack that does not require macros and instead uses an old Microsoft Office feature called Dynamic Data Exchange to execute code on targeted computers.
The feature allows you to pull data from one document and inject it into a second. For example, open a monthly sales report in Word and an embedded field can be dynamically updated with sales data from a separate Excel spreadsheet. What SensePost’s PoC shows is how Dynamic Data Exchange (DDE) can be abused to open a command prompt and run malicious code on a targeted computer.
SensePost reported the DDE attack scenario to Microsoft in August. On Sept. 26, Microsoft responded stating: “It is a feature and no further action will be taken, and will be considered for a next-version candidate bug.”
When DDE is used to swap just data (not to execute command prompts), a relatively benign warning message is presented that says: “This document contains links that may refer to other files. Do you want to update this document with the data from the linked files?”
When DDE is used to open a command prompt a different warning is presented to the user: “The remote data (k calc.exe) is not accessible. Do you wish to start the application c:\windows\system32\cmd.exe?”
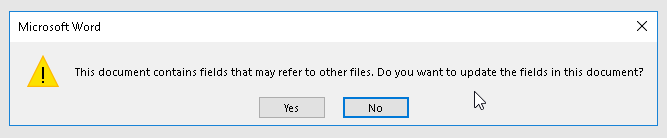
In its PoC, SensePost said it was able to suppress the syntax in the more alarming warning message, making it sound more mundane—closer to the first.
“The second prompt asks the user whether or not they want to execute the specified application, now this can be considered as a security warning since it asks the user to execute ‘cmd.exe’, however with proper syntax modification it can be hidden,” wrote SensePost in its PoC.
The updated syntax reads: “This document contains fields that may refer to other files. Do you want to update the fields in this document?”
Most importantly, unlike with malicious macros that are often flagged by antivirus scanners, this DDE technique does not deliver any security warnings from third-party antivirus software and marks documents as “clean,” according to SensePost.
The malicious use of DDE isn’t new. Last year, the ScarCruft APT group used DDE as one step in a multistage attack designed to bypass antivirus detection. Kaspersky Lab researchers said the attack makes use of Windows DDE.
“This has been mentioned by others as a possible avenue, but to our knowledge, no one has actually demonstrated this to work.” SensePost links to blog post dated March 2017 on PwnDizzle that explains a theoretical attack using DDE.
The DDE feature has since been replaced by Microsoft’s Object Linking and Embedding (OLE) toolkit. But, according to Microsoft, Office still supports legacy documents that take advantage of the feature.










