A spam campaign pushing the info-stealing LokiBot trojan leverages a novel technique to avoid detection. According to researchers, the spam messages include malicious .zipx attachment hidden inside a .PNG file that can slip past some email security gateways.
According to Trustwave SpiderLabs, that first spotted the .PNG/LokiBot messages, the spam campaigns delivering the trojan have been limited in scope, so far. “This represents an extension to the existing ways LokiBot is delivered via email,” said Phil Hay, senior research manager at Trustwave.
LokiBot is a prolific trojan designed to covertly siphon information from compromised endpoints. The malware is known for being simple and effective and for its adoption of diverse attachment types. The malware is a commodity in underground markets, with versions selling for as little as $300.
Trustwave researchers said the spam message delivering the payload LokiBot has three distinct characteristics. First, the attachment used in the spam campaign has a .zipx extension, meaning it is a compressed archive. These types of compressed files are notorious for harboring malware and are flagged by email security gateways as dangerous.
In an attempt to avoid detection, hackers behind the malspam trick email security gateway scanners by obfuscating the archive, using the file signature of a .PNG (portable network graphics) format. Attackers use the .PNG file structure, complete with a .PNG “header” and “IEND”. That way when the malicious file (RFQ -5600005870.zipx) is scanned it is identified as a .PNG image, even though it has a .zipx extension. The actual archive code – harboring LokiBot – is appended to the end of the .PNG file signature.

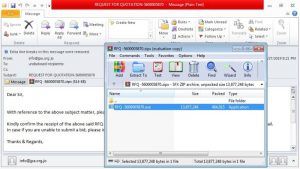
The .zipx archive uses the file signatures of a .PNG image file to avoid detection and also allows the .PNG image to be viewed. This is .PNG image is of a JPG icon.
“In a PNG file IEND is supposed to mark the end of the image, and is supposed to appear last. But in this file there is a bunch of data after IEND,” according to a technical write-up co-authored by Rodel Mendrez, senior security researcher at Trustwave and Hay. “The PNG format specification appears to allow for such extraneous data, it is up to the application to decide to try and interpret or ignore such data,” researchers wrote.
They added, the malicious attachment (RFQ -5600005870.zipx) can be displayed in an image viewer as a .PNG image of a .JPG icon. Perhaps another attempt at tricking perimeter defenses.
Click Attachment Launch LokiBot
As slick as the obfuscation is, getting infected takes effort.
To get infected a victim must first click on the message attachment (RFQ -5600005870.zipx). Doing so might, or might not, launch the right archive decompressor application – depending on client side applications installed on targeted computers. According to researchers, the WinRAR utility is one of the only file decompressing utilities that reliably open and decompress this .zipx archive. Other utilities, such as 7-Zip and WinZip, fail to open the specific file – likely because of the extraneous data packed inside the file signature.
Now, after the 500 KB .zipx archive is extracted by WinRAR to a 13.5 MB payload, the user must double-click the unpacked RFQ -5600005870.exe file.
“This first stage function [of the .exe] is to decrypt the main payload into the memory and execute it using a common technique called Process Hollowing, where a new process is created in a suspended state, its memory is unmapped and the malicious code replaces it,” researchers wrote.
Post-Exploitation
The Lokibot command-and-control tools are written in the PHP (Hypertext Preprocessor) programing language and almost always uses the file name “fre.php”, researchers said. “So, fre.php could be blocked at the gateway,” they said. The bot control panel source has been leaked to GitHub and uses the same fre.php file name, they added.
Trustwave said the malspam samples it found were blocked at its email gateway. “Two of the multiple layers had detected it as either spam or potentially malicious. But I can’t speak for other gateways,” Hay said.
“The wider point is that, because it is hidden in a real PNG file, it may not be recognized as a Zip archive, and therefore gateways may simply ignore it,” according to researchers.