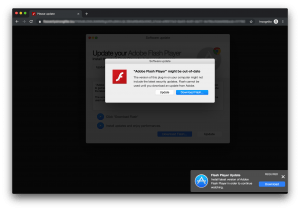
Never-before-seen Mac malware, dubbed OSX/CrescentCore, has been discovered in the wild. The trojan, spotted on various websites masquerading as an Adobe Flash Player installer, drops malicious applications and browser extensions on victims’ systems when downloaded.
OSX/CrescentCore is spread via various websites, where it is masqueraded as an Adobe Flash Player installer. However, the “installer” is actually a .dmg file (an Apple disk image) that delivers the malware.
“One variant of OSX/CrescentCore was observed dropping potentially unwanted applications, rogue software like OSX/AMC (short for ‘Advanced Mac Cleaner’),” Joshua Long with Intego told Threatpost on Tuesday. “Another variant of OSX/CrescentCore tried to install a malicious Safari browser extension.”
The malware was discovered by researchers being distributed via numerous sites – some of which popped up on Google search results. One such site, called “GetComics,” purported to share digital copies of new comic books for free.
The malware was also spread via high-ranking Google search results, which were observed redirecting users to multiple sites.
“We were actually in the process of coming up with a name for CrescentCore, and searched for ‘CrescentCore’ in quotation marks, and one of the links in the first page of search results redirected to a page that happened to be distributing a new sample of CrescentCore,” Long said.
The researcher said that oftentimes malware distributors will find vulnerable blogs or other sites with high Google search engine rankings, and add a redirection mechanism that bounces through a number of affiliate links – ultimately redirecting users to a fake Flash Player landing page.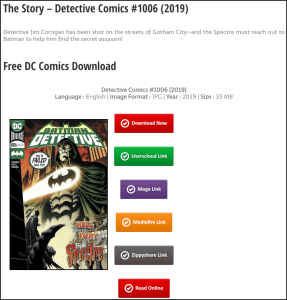
“So if a result for a previously almost unused word like CrescentCore happened to show up in search results, it’s extremely likely that other search results are poisoned with redirections to this malware as well,” he said.
After looking further into these search results, researchers found that a page (hosted at any of a large number of domains) was displaying an Adobe Flash Player update warning popup. When clicked, this popup distributed either the new OSX/CrescentCore malware or previously discovered OSX/Shlayer malware.
However, “Unlike the typical, everyday, fake Flash Player updater, OSX/CrescentCore has some extra capabilities in an effort to make it more difficult for antivirus software to detect, and more difficult for malware analysts to examine and reverse engineer,” according to Intego’s analysis published last week.
Once downloaded the malware touts advanced features allowing it to skirt detection, including the capability to sniff out whether it’s running within a virtual machine environment (a common way to check machines for malware) or if antivirus software is present on the machine – if either are determined, it will simply shut down.
“Malware analysts often examine malware inside a VM to avoid unintentionally infecting their own computers while working with dangerous files, so malware authors sometimes implement VM detection and behave differently to make it more difficult to analyze the malware’s behavior,” said researchers.
If neither are detected, the malware will then install a LaunchAgent which helps it achieve persistence even further on the infected machine. LaunchAgent, which is a folder that can be installed in Macs’ Library folder that specifies code that should be run every time that user logs in, is commonly utilized by malware to achieve persistence on macOS.
The malware is signed using multiple Apple Developer IDs registered to someone named Sanela Lovic; known identifiers so far include 5UA7HW48Y7 and D4AYX8GHJS, said researchers.
The malware is only the latest discovered to be targeting Mac systems. Last week, researchers said they have discovered never-before-seen Mac malware samples (OSX/Linker) which they believe are being developed to target a recently-disclosed vulnerability in the MacOS operating system. In May, a bug was disclosed in the macOS security feature Gatekeeper that allows malicious code execution on systems running the most recent version of Mojave (10.14.0).
“Mac malware developers are actively becoming more clever, attempting to make it harder to detect the malicious nature of their software,” said Long. “As we learned with OSX/Linker, makers of Mac malware are also experimenting with new ways of bypassing Apple’s built-in protection mechanisms, even attempting to use zero-day vulnerabilities to do so.”