Macro-based malware has crossed the divide between the Windows and Mac platforms.
A cybercrime group whose command and control infrastructure resolves to an IP address geo-located in Russia is using a Word document laced with a malicious macro that executes solely on macOS.
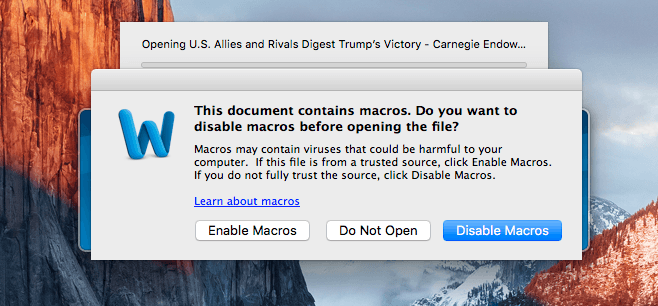
Following the same script as similar Windows-based attacks, the attached documents have a luring subject line, in this case: “U.S. Allies and Rivals Digest Trump’s Victory – Carnegie Endowment for International Peace.docm.” Once a user tries to open the attachment, they’re presented with a familiar dialogue box instructing them that macros must be enabled to view the document. If the macro is enabled, it executes its payload which then tries to download more code from the attacker’s site.
“It’s kind of a low-tech solution, but on one hand it’s abusing legitimate functionality so it’s not going to crash like a memory corruption or overflow might, and it’s not going to be patched out,” said Patrick Wardle, director of research at Synack. Wardle and a number of other researchers, analyzed the behavior of the macros and payload and published a report Monday.
“It’s low tech but it’s going to have a high success rate if people fall for it,” Wardle said. “Anytime you can target users; that’s why ransomware is so successful. That’s why macros work. They’re definitely the weakest link in my opinion.”
The attack works only on Mac versions of Word (attempts to execute on Windows or Pages, Mac-based productivity software similar to Word, failed). It also sidesteps Apple’s Gatekeeper protection which blocks unsigned code from executing; macros will execute since they’re given permission to do so by the user.
Once enabled, the macro decodes data and executes it via Python from an open source project called EmPyre. EmPyre is a legitimate open source Mac and Linux post-exploitation agent often used in penetration testing engagements. The attackers embedded a first stage component of EmPyre into the Word document and its sole purpose was to call out to the command infrastructure at securitychecking[.]org[:]443/index[.]asp for the second stage. The site, however, has gone dark so the researchers cannot be sure of exactly what the second stage was, but it’s likely the remaining EmPyre components.
“I see no reason why the attackers would use just one stage and not the other, especially when the first stage expects the second stage to be encrypted with a certain RC4,” Wardle said. “It’s possible that their code once it executes in the Word document could download and execute anything, but it’s very likely they’re going to download that second piece of the EmPyre agent.”
The second stage of EmPyre, Wardle said, is a persistent Mac backdoor that allows for a number of malicious capabilities, including modules for grabbing browser history, turning on the webcam, keylogging and dumping of hashes.
“From a hacker’s point of view, there’s this great open source module out there with all these different plugins, why not just use that,” Wardle said. “I think that’s what they did.”
It’s unknown who the attackers are behind this campaign, but it’s more than likely a cybercrime outfit given the use of macros and of an available open source tool. As for the securitychecking[.]org, it’s been previously associated with cybercrime activities such as phishing and other malware downloads.
“It looks like it’s some standard cybercriminal stuff. It’s not particularly advanced, they just spray it out there and see how many targets they can get,” Wardle said. “It’s not incredibly sophisticated but it if it works… Look at most ransomware attacks, they’re not using 0days, and it’s becoming an epidemic.”