Researchers have uncovered a previously unknown malicious IIS module, dubbed Owowa, that steals credentials when users log into Microsoft Outlook Web Access (OWA).
Internet Information Services (IIS), Microsoft’s web server/web-hosting software suite, can be extended via various add-ons that are known as modules.
Like plugins for WordPress or Chrome extensions, IIS modules offer an attractive way to side-load malicious features into web-facing applications. In this case, Owowa infects Exchange servers, exposing Exchange’s OWA function. Beyond credential theft, it allows remote attackers to run commands on the underlying server and to establish a foothold for access to the broader network, researchers warned.
“[It] allows the attackers to steal login credentials for Outlook Web Access and gain remote access control to the underlying server,” according to researchers at Kaspersky, in a Tuesday writeup. “Its malicious capabilities can easily be launched by sending seemingly innocuous requests – in this case, OWA authentication requests.”
The module is also stealthy and difficult to detect, and it offers persistence even in the face of software updates from Exchange, according to Pierre Delcher, senior security researcher with Kaspersky’s Global Research and Analysis Team (GReAT).
“The particular danger with Owowa is that an attacker can use the module to passively steal credentials from users who are legitimately accessing web services,” he explained. “This is a far stealthier way to gain remote access than sending phishing emails. In addition, while IIS configuration tools can be leveraged to detect such threats, they are not part of standard file and network monitoring activities, so Owowa might be easily overlooked by security tools.”
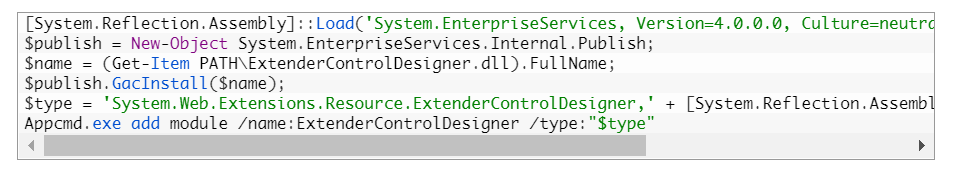
The malicious module can be loaded by a cyberattacker that has initial access to the server environment (perhaps by exploiting the ProxyLogon or ProxyShell vulnerabilities), researchers explained. It’s loaded using the PowerShell script shown below:
“The module is first registered in the global assembly cache, and can then be loaded by the IIS server that is running the OWA application,” according to Kaspersky.
Once installed, the module monitors HTTP requests and responses for OWA traffic by hooking the “PreSendRequestContent” event, according to Kaspersky. When an OWA authentication request is made, it springs into action, first checking that the login attempt was successful by checking that the OWA application is sending an authentication token back to the user. If that’s the case, the username, password, user’s IP address and current timestamp are stored in a file and encoded with RSA encryption.
Cybercriminals can interact with Owowa and exfiltrate the harvested logins by entering specially crafted commands – detailed below – into the username and password fields in the OWA log-in page of the compromised server, according to Kaspersky’s analysis.
- If the OWA username is jFuLIXpzRdateYHoVwMlfc, Owowa will return the encrypted credentials log, encoded in base64;
- If the OWA username is Fb8v91c6tHiKsWzrulCeqO, the malicious module deletes the content of the encrypted credentials log, and returns the OK string (encrypted using RSA);
- If the OWA username is dEUM3jZXaDiob8BrqSy2PQO1, Owowa executes the command that is typed in the OWA password field using PowerShell on the compromised server. The result of the command is encrypted (as previously described) and returned to the operator.
Tracking Owowa’s Development
Researchers uncovered that Owowa was compiled sometime between late 2020 and April 2021, ironically around the same time that the aforementioned ProxyLogon set of four critical vulnerabilities in Microsoft Exchange servers were found, giving attackers the ability to gain access to registered email accounts and execute arbitrary code. The module has been used since then to target government and public-sector victims in Indonesia, Malaysia, Mongolia and the Philippines, including a state transportation company. Researchers suspect there are also victims in Europe.
Kaspersky researchers could not link Owowa to any specific threat actor, beyond noting the use of the username “S3crt” in the coding. The name is linked to the development of other malicious binary loaders, researchers noted. However, the handle could very well be used by multiple individuals. It’s also the username on an account on RAID Forums, which specializes in Core Impact: a popular penetration-testing software suite.
Whatever may be the case with S3crt, the operator is unlikely to be an advanced persistent threat (APT) despite the victimology and obvious goal of espionage, according to the analysis. That’s because the development shows some rookie mistakes.
For instance, the creators ignored explicit warnings from Microsoft regarding several risky development practices for HTTP modules, which may result in server crashes (thus alerting admins to Owowa’s presence). And, they left behind sensitive information on the development environment, clearly visible in publicly available samples. These can be used to find links to further samples or online profiles.
“The good news is the attackers don’t appear highly sophisticated,” said Paul Rascagneres, senior security researcher with Kaspersky’s GReAT. “Companies should closely monitor Exchange servers since they are highly sensitive and contain all corporate emails. We also recommend considering all running modules as critical and checking them regularly.”
How to Protect Against Malicious IIS Modules
To defend against the threat, Kaspersky recommended that organizations:
- Regularly check loaded IIS modules on exposed IIS servers (notably Exchange servers), leveraging existing tools from the IIS server suite. Malicious IIS modules, and Owowa in particular, can be identified by using the command “appcmd.exe” or the IIS configuration tool, which lists all the loaded modules on a given IIS server.
- Check for such modules as part of regular threat-hunting activities, and every time a major vulnerability is announced on Microsoft server products.
- Focus the defense strategy on detecting lateral movement and data exfiltration to the internet, paying special attention to outgoing traffic to detect cybercriminal connections.
- Back up data regularly and make sure it can be quickly accessed in an emergency.
Check out our free upcoming live and on-demand online town halls – unique, dynamic discussions with cybersecurity experts and the Threatpost community.