Cybercriminals are increasingly turning to a legitimate, Pastebin-like web service for downloading malware — such as AgentTesla and LimeRAT — in spear-phishing attacks.
Pastebin, a code-hosting service that enables users to share plain text through public posts called “pastes,” currently has 17 million unique monthly users and is popular among cybercriminals (such as the FIN5 APT group and Rocke threat group) for hosting their payloads or command-and-control (C2) infrastructure. But now, more malware and ransomware families are starting to utilize another service, with the domain Paste.nrecom[.]net.
This service been around since May 2014, and has a similar function as Pastebin. It also has an API (powered by open-source PHP based pastebin Stikked) that allows for scripting. Researchers with Juniper Networks said that the API feature is lucrative for cybercriminals, who can leverage it to easily insert and update their data programmatically.
“Although using legitimate web services is not novel, this is the first time that we have seen threat actors use paste.nrecom[.]net,” said Paul Kimayong, researcher with Juniper Networks, in a Monday analysis. “Among the malware we have identified are AgentTesla, LimeRAT, [W3Cryptolocker] Ransomware and Redline Stealer.”
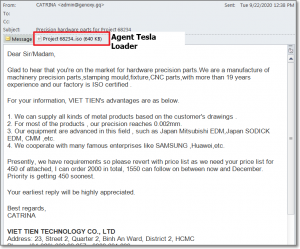
Researchers said that the attacks utilizing the service generally start with a spear-phishing email that includes an attachment (such as a document, archive or an executable). The recipient is tricked into opening a malicious attachment (as the first stage of the attack), which then downloads the next stages from paste.nrecom[.]net.
“We have also seen malware hosting their configuration data in the same service,” said researchers.
AgentTesla is the most active malware family using this service, researchers said. The spyware is capable of stealing personal data from web browsers, mail clients and FTP servers, as well as collecting screenshots and videos, and capturing clipboard data.
Researchers highlighted specific AgentTesla campaigns that target multiple industries related to shipping, supply chains and banks, using spear-phishing emails with archive attachments (such as .iso, .rar or .uue). These attachments, once opened, then install AgentTesla using paste.nrecom.
The developers of LimeRAT, an open-source remote administration trojan coded in .NET (used recently by the APT-C-36 group to target Colombian government institutions) have also utilized the web service to download malware.
Other, newer malware and ransomware are also turning to paste.nrecom. One of these is W3Cryptolocker, a relatively new ransomware that surfaced in July. Researchers found that the initial-stage loader was hosted on a potentially hacked site, italake.com. Once the loader was downloaded, W3Cryptolocker was executed, after which it encrypted most files in all drives and created a “Read_Me.txt” file on each folder with the ransom message.
And, Redline Stealer, a malware that surfaced as recently as March and has targeted healthcare and manufacturing firms in the U.S., also makes use of the service. Researchers said they found samples posing as a Bitcoin miner archived into a RAR file. The RAR file contained an executable (MinerBitcoin.exe) that downloaded the Redline Stealer payload from paste.nrecom.
Looking ahead, researchers warned that more malware families will turn to legitimate web services to host their malicious infrastructure.
“Using legitimate web-services like pastebin or paste.nrecom for malware infrastructure gives cybercriminals an advantage, as these services cannot be easily taken down due to their legitimate use,” said researchers.
On October 14 at 2 PM ET Get the latest information on the rising threats to retail e-commerce security and how to stop them. Register today for this FREE Threatpost webinar, “Retail Security: Magecart and the Rise of e-Commerce Threats.” Magecart and other threat actors are riding the rising wave of online retail usage and racking up big numbers of consumer victims. Find out how websites can avoid becoming the next compromise as we go into the holiday season. Join us Wednesday, Oct. 14, 2-3 PM ET for this LIVE webinar.