SINT MAARTEN—Malware scanning services could be the next listening outpost for criminals and nation-state attackers as more of these services such as VirusTotal are becoming containers for personal, business and even classified information because of some organizations’ policy decision to upload every file, document and email.
Markus Neis, threat intelligence manager at Swisscom AG, this week joined the growing throng of experts warning organizations to be more selective about data sent to scanning services. At the Kaspersky Lab Security Analyst Summit, Neis shared his research into the problem and how with some crafted Yara rules he was able to return thousands of emails marked as confidential, as well as corporate business plans and government emails. He also found 800 TLP (Traffic Light Protocol) Amber STIX documents from the Department of Homeland Security and 60 documents coming from the FBI which were either TLP Green or TLP Amber. TLP Amber or Red documents are not meant to be shared and are considered classified. Neis said there are no shortage of PGP keys, VPN credent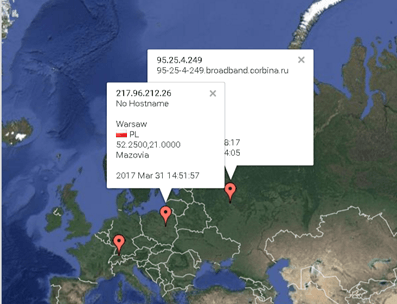 ials and SSH private keys sitting in documents uploaded to VirusTotal and surely other scanning services.
ials and SSH private keys sitting in documents uploaded to VirusTotal and surely other scanning services.
Google-owned VirusTotal has taken measures to cut down on abuses of its service. But licensed VirusTotal users do have the ability to download files (this may not be the case with other malware scanning services); Neis said he uploaded a Word document that contained a Canarytoken that alerted him to when the file was accessed and within two days, it had been distributed and downloaded in the U.S., Germany, Russia and Poland (right).
Third-party business partners are one of the biggest offenders, Neis said. Business data used in outsourcing engagements is often automatically sent to a malware scanner and the original data owners are none the wiser.
“It seems to be a common thing for suppliers or outsourcing contractors in India that they are uploading stuff like that,” Neis said. “India seems to be pretty active in terms of uploading things to VirusTotal.
‘The major thing is that you totally lose control over your data and encryption is no help,” Neis said. “The supplier decrypts it and sends it to VirusTotal.”
The accessibility of critical data would figure to be attractive to those engaged in corporate or nation-state espionage. One equipment manufacturer has uploaded a confidential business plan belonging to a U.S.-based internet service provider. Confidential data belonging to luxury carmakers, telecommunications companies and many Forbes 2000 enterprises can be downloaded. Neis said he attempted to disclose to the FBI about the available TLP Amber flash alerts, but got no response.
Neis started down this path as means of predicting impending attacks against Swisscom. He built a reliable set of Yara rules that enabled him to pull out data directly affecting Swisscom and alert if certain data was present in an upload such as a PGP key.
“That was my first approach. Then I ended up searching for data that was marked as confidential and started with the TLP marking structure because it’s a very easy find,” Neis said.
Neis said he also found tailored malware reports meant to be shared between security companies that normally collaborate on research that were also uploaded.
“These guys do not even trust the security companies from where they were requesting the reports and they were uploading these reports to VirusTotal,” Neis said.
For the time being, it’s likely this behavior of organizations automatically uploading data to scanning services will continue.
“My hope is that people realize we can find to some extent an understanding of what is happening and that a malware repository or scanning service is not something they should use as a strategy where you’re putting your data just to make sure the data you have just received is not a threat to you,” Neis said. “Instead, you should go to your own security team and ask them for help. A lot of people are overwhelmed with all the email and attachments they receive. You can’t blame them. What should happen is that in organizations should start enabling their own employees to learn how they should treat that, and also the security team in turn could start to block VirusTotal on the proxy and create something internal like a central point where you can hand stuff in and the security team can decide whether to upload that.”
This article was updated April 5 with clarifications.










