Americans who either applied for new jobs, loans, or just wanted to check their credit score via Equifax are having a difficult time getting answers as to whether they are part of the breach of 143 million records that occurred Thursday.
The company disclosed yesterday it was the victim of a massive cyberattack. From mid-May to the end of July this year, Equifax said criminals accessed files including names, Social Security numbers, birth dates, addresses and even driver’s license numbers. Since the revelation, the company’s site has been overwhelmed with worried website visitors that have brought the site to a crawl and at times rendered it unreachable.
Visitors lucky enough to get through are directed to a special site (trustedidpremier.com) setup by Equifax in response to the massive breach. Ironically, it asks privacy-minded users to provide their last name and the last six digits of their Social Security number in order to verify if they have been impacted by the breach. However, even if a user is among the millions of Americans affected by the breach they’re encouraged to return to the site next week to continue enrolling in the company’s ID theft protection and credit monitoring services that are being offered for free in response to the breach.
The site’s legalese has been called into question since Thursday with many astute readers wondering whether their legal rights, particularly the ability to participate in a class action against Equifax are affected by using the site. Eric Schneiderman, New York State’s Attorney General, called the language unacceptable and unenforceable Friday morning. In response Equifax amended its policy with regards to arbitration on Friday afternoon. Schneiderman says his office is “continuing to closely review.”
https://twitter.com/AGSchneiderman/status/906235416738705408
Site accessibility wasn’t the only issue with Equifax’s site in the fallout of Thursday’s breach revelation. For a period of time yesterday OpenDNS was blocking the site, trustedidpremier.com, over suspicions it was part of a phishing attack.
@opendns Come on guys. Your Phishing reporting/detection has been spoofed. https://t.co/B6qwuvbcyQ is the website for @Equifax hack victims pic.twitter.com/vP5wr8Lx6r
— Daniel Pentecost (@davoice) September 8, 2017
The issue was fixed and blamed on a false-positive, mostly because of the “word in domain, freshness of registration, volume of traffic spiking from nothing,” according to OpenDNS founder David Ulevitch.
Being fixed.
— David Ulevitch 🇺🇸 (@davidu) September 8, 2017
Christina Camilleri, a security analyst at Bishop Fox, pointed out on Twitter the site looked suspicious from the get go as it was separate from Equifax’s and lacked proper SPF records.
This Equifax website can't be real, right? RIGHT? Registered on 8/22, asks for last 6 of your SSN & no SPF records. https://t.co/IvjHTeden9
— Christina Camilleri (@0xkitty) September 7, 2017
Alex Heid, a white hat hacker and chief research officer at SecurityScorecard, a service that assesses companies’ cybersecurity strength, told Threatpost on Friday that a cursory glance at Equifax’s network revealed the company was running a handful of legacy systems that may have contributed to the breach.
“Many of the web applications hosted within the Equifax network are written in JSP, and a few pages appear to be coded with ASPX. There also appear to be a large amount of legacy Microsoft IIS web servers in use,” Heid said, “Throughout 2017 there have been several weaponized exploits that have been made public which impact JSP services as well as IIS systems, such as the recent assortment of Apache Struts vulnerabilities as well as a highly popular IIS WebDav exploit attack.”
It’s unclear at this point exactly which exploit attackers used to breach Equifax’s systems.
Heid said the fact the company specified it was a web application vulnerability, paired with the site’s dated software, could have made it easy for attackers however. “The disclosed vector of a web application vulnerability combined with an expansive digital footprint of legacy software and timeline of disclosures for 2017 exploit code seem to have created the conditions for ‘a perfect storm,'” he said.
If that’s the case, there are certainly a number of vulnerabilities that have recently come to light that could be related.
In March, Microsoft said it wouldn’t fix a publicized buffer overflow vulnerability in IIS WebDav 6.0 web server. Instead, it urged users to update to the latest version. Also, just this week, the Apache Software Foundation patched a nasty remote code execution bug that affected all versions of Struts since 2008. The bug affected all web apps that used the framework’s REST plugin. It was the second major vulnerability to plague Struts this year. In March researchers observed an uptick in attacks and scans for a vulnerability that affected Struts 2 after proof-of-concept exploit code was introduced into Metasploit.
Equifax did not immediately respond to a request for comment regarding the security of its site or why trustedidpremier.com was asking for two-thirds of a consumer’s Social Security number to verify whether an individual was part of the breach.
https://twitter.com/gossithedog/status/905946778608050176
Marten Mickos, CEO of HackerOne, pointed out that even if researchers found vulnerabilities in Equifax’s site, they wouldn’t have had an easy time disclosing them.
“A couple bugs have been disclosed via Open Bug Bounty, a non-profit project designed to connect hackers with website owners to resolve bugs in a transparent and open manner,” Mickos said, “One of which was disclosed for their UK website that took nearly five months to resolve, and the second for the U.S. website, which has yet to be resolved.”
The second bug Mickos is referring to is a cross-site-scripting bug, more than a year and a half ago, in March 2016, that still hasn’t been patched: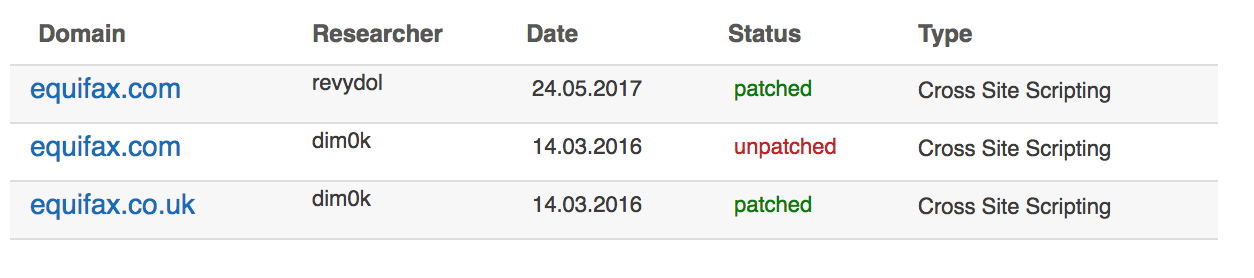
https://twitter.com/dustyfresh/status/905935209983610881
The company said Thursday the incident impacts approximately 143 million U.S. consumers, or 40 percent of the U.S. population. As part of the recent Equifax breach, the company said cybercriminals were able to access credit card numbers for 209,000 consumers and accessed the credit dispute documents of roughly 182,000 U.S. consumers. The company’s Chairman and Chief Executive Officer, Richard Smith, posted a somber YouTube video alongside the disclosure apologizing for the incident on Thursday.
“This is clearly a disappointing event for our company, and one that strikes at the heart of who we are and what we do. I apologize to consumers and our business customers for the concern and frustration this causes,” Smith said.










