An ongoing domain name spoofing campaign is taking aim at retail giant Walmart and other big fish, with more than 540 malicious domains being used to harvest consumer information.
The scam domains are mimicking legitimate sites in name and appearance, in hopes of fooling visitors into entering their personal details, according to analysis from DomainTools. Aside from Walmart, other big-name lures are affiliated with the phishing campaign, spoofing Fortune 500 companies like McDonald’s, online dating sites and movie downloads. An unknown threat actor is behind it all, the firm said, displaying an obvious level of sophistication given the sheer scale of the effort.
One domain in particular kicked off the firm’s investigation and proved to be the tip of the iceberg: www.walmartcareers[dot]us. Purporting to be an employment application site for Walmart, with the look and feel of a legitimate site for the retailer, it gathers personal information from would-be job-seekers. The researchers soon uncovered other Walmart-themed sites that offer gift cards or other services, and the investigation widened from there.
“These sites are so convincing, job applicants are going through entire (fake) application process, even showing up to in-person interviews, only to find out that they have turned over their personal credentials to threat actors,” a DomainTools spokesperson said via email.
Further investigation uncovered registrant details that point to Pakistan and Bangladesh, but a majority of the IP addresses are located in the United States, according to the analysis.
The pages are also successfully evading defenses. Of the 540-plus identified domains in the campaign, only 181 have appeared on blacklists, according to DomainTools. But the others were given average risk scores, which indicates that they have a very high likelihood of being blacklisted in the future, the firm said.
“The number of malicious domains that surfaced in this campaign is alarming and likely an indication of the threat actor or group’s resources and sophistication,” said Corin Imai, senior security advisor, DomainTools, in a blog posted on Tuesday. “Our initial intent was to take a closer look at Fortune 500 companies, but our investigation led us down an unexpected path. Although we successfully detected and to some degree identified the intent of this campaign, we are committed to uncovering its scale as well as more information about those behind it.”
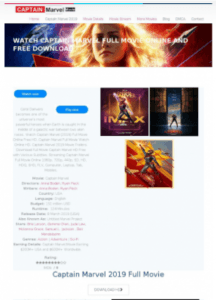 Other sites, such as those claiming to offer movie downloads, collect personal data but also could be used to push malware. As for how successful the adversaries have been in fooling people, the jury is out.
Other sites, such as those claiming to offer movie downloads, collect personal data but also could be used to push malware. As for how successful the adversaries have been in fooling people, the jury is out.
Imai added, “There is enough traffic to these sites to warrant further investigation into whether people are submitting their personally identifiable information and unknowingly turning over their credentials to threat actors.”
Phishing attempts more than doubled in 2018, as bad actors sought to trick victims into handing over their credentials. Researchers with Kaspersky said earlier this year that during the course of 2018, they detected phishing redirection attempts 482.5 million times – up from the 246.2 million attempts detected in 2017. In total, 18.32 percent of users were attacked, researchers said.
Consumers should always verify a site’s legitimacy by checking the URL to ensure nothing looks suspicious before submitting their username and password, credit-card information or personally identifiable information (PII), such as first name, last name, address or Social Security number.
Black Hat USA 2019 has kicked off this week in Las Vegas. For more Threatpost breaking news, stories and videos from Black Hat and DEF CON, click here.











