Emotionally vulnerable and willing to offer up any information that lands the gig, job seekers are prime targets for social engineering campaigns. And with the “Great Resignation” in full swing, cybercriminals are having an easy time finding their next victim.
Just since Feb. 1, analysts have watched phishing email attacks impersonating LinkedIn surge 232 percent, attempting to trick job seekers into giving up their credentials.
“Current employment trends help to make this attack more convincing,” a new report from Egress said. “‘The Great Resignation’ continues to dominate headlines, and a record number of Americans left their jobs in 2021 for new opportunities. It is likely these phishing attacks aim to capitalize on jobseekers (plus curious individuals) by flattering them into believing their profile is being viewed and their experience is relevant to household brands.”
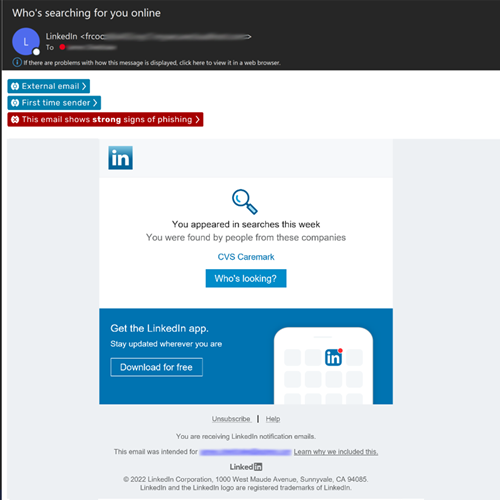
The emails had subject lines that would be enticing to job hunters hoping to get noticed, like, “Who’s searching for you online,” “You appeared in 4 searches this week” or even “You have 1 new message,” the Egress team said.
The phishing emails themselves were convincing dupes, built in HTML templates with the LinkedIn logo, colors and icons, the report added. The scammers also name-checked well-known companies throughout the bodies of the phishing emails, including American Express and CVS Carepoint, to make the correspondence seem more legitimate, the analysts said.
Even the email’s footer lifted the company’s headquarters’ address and included “unsubscribe” links to add to the email’s authenticity, the analysts pointed out.
“You can also see the LinkedIn display name spoofing, which is designed to hide the webmail accounts used to launch the attacks,” the report said.
Once the victim clicks on the malicious links in the email, they were directed to a site to harvest their LinkedIn logins and passwords.
“While the display name is always LinkedIn and the emails all follow a similar pattern, the phishing attacks are sent from different webmail addresses that have zero correlation with each other,” the analysts added. “Currently, it is unknown whether these attacks are the work of one cybercriminal or a gang operating together.”
021722 09:18 UPDATE: LinkedIn sent the following statement to Threatpost:
“Our internal teams work to take action against those who attempt to harm LinkedIn members through phishing. We encourage members to report suspicious messages and help them learn more about what they can do to protect themselves, including turning on two-step verification. To learn more about how members can identify phishing messages, see our Help Center here.”
Data Scraping Attacks on Job Seekers
Besides using potential job leads to trick targets into coughing up their credentials, Imperva, in a separate report, detailed how it stopped the largest bot attack the company has seen to date, on a global job listing site.
Imperva didn’t specifically name the company, but the company said that it was bombarded with 400 million bot requests over 400,000 unique IP addresses over four days that tried to scrape all its job seekers’ data.
The Imperva team added that these types of web-scraping attacks are common and can result in “lower conversion rates, skewed marketing analytics, decrease in SEO ranking, website latency, and even downtime (usually caused by aggressive scrapers).”
But as Imperva pointed out in its report, data scraping is one of those cybersecurity gray areas. Collecting publicly available information isn’t itself a data breach, but collected in mass quantities, it can be a weapon wielded against users in social-engineering attacks.
Last summer, a massive data-scraping attack against LinkedIn was discovered to have collected at least 1.2 billion user records that were later sold on underground forums. At the time, LinkedIn reiterated that the scraped data was public information, not private information, and didn’t qualify as a breach.
LinkedIn isn’t really at fault here, according to Yehuda Rosen, senior software engineer at nVisium.
“This has little to do with LinkedIn specifically – they’re not doing anything wrong here,” Rosen explained to Threatpost. “It boils down to the fact that LinkedIn has hundreds of millions of members – many of whom are very accustomed to seeing frequent legitimate emails from LinkedIn – and may inevitably click without carefully checking that each and every email is the real deal.”
That leaves it to individual users to be mindful of the information they expose publicly and how it could be used to trick them into clicking on a malicious link.
“While I don’t believe that this will hurt LinkedIn’s brand, this does reiterate the importance of email phishing education,” Ray Kelly, with NTT Application Security, told Threatpost by email. “Given these emails are coming from a legit LinkedIn email address makes it especially difficult to identify the danger. My rule is to never click on email links. Always visit the site directly.”
Join Threatpost on Wed. Feb 23 at 2 PM ET for a LIVE roundtable discussion “The Secret to Keeping Secrets,” sponsored by Keeper Security, focused on how to locate and lock down your organization’s most sensitive data. Zane Bond with Keeper Security will join Threatpost’s Becky Bracken to offer concrete steps to protect your organization’s critical information in the cloud, in transit and in storage. REGISTER NOW and please Tweet us your questions ahead of time @Threatpost so they can be included in the discussion.