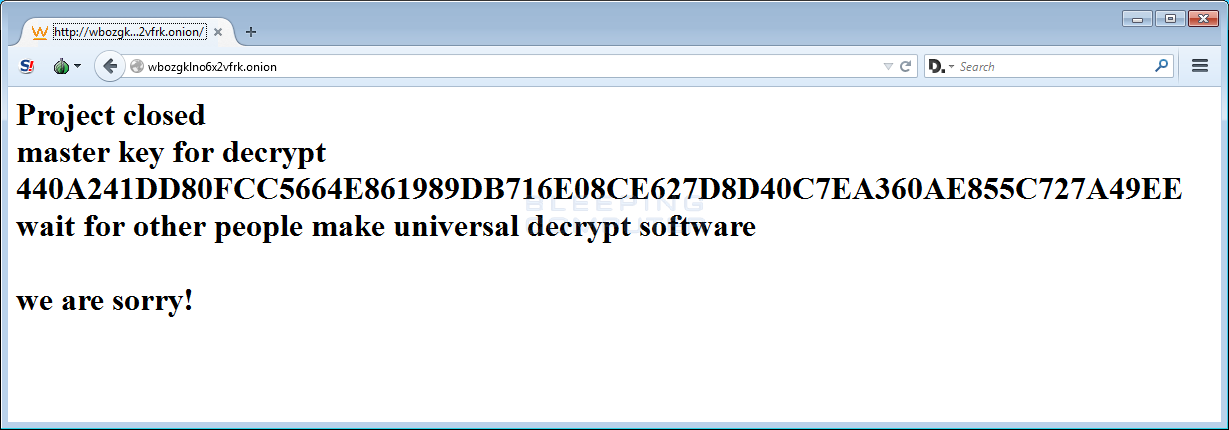
The criminals behind the TeslaCrypt ransomware have closed up shop and publicly released the master decryption key that unlocks files encrypted by the malware.
The news is significant given the investment and constant innovation devoted to TeslaCrypt, which has been one of the most active crypto-ransomware strains since it debuted in February 2015.
Researchers at Bleeping Computer said that researchers had noticed hints that distribution TeslaCrypt was being phased out in favor of CryptXXX ransomware, even though criminals behind the respective ransomware are likely different. A researcher from ESET, Bleeping Computer’s Lawrence Abrams said, asked for the master decryption key on a TeslaCrypt support site and the attackers capitulated, posting the key along with a message that partially read: “Project closed.”
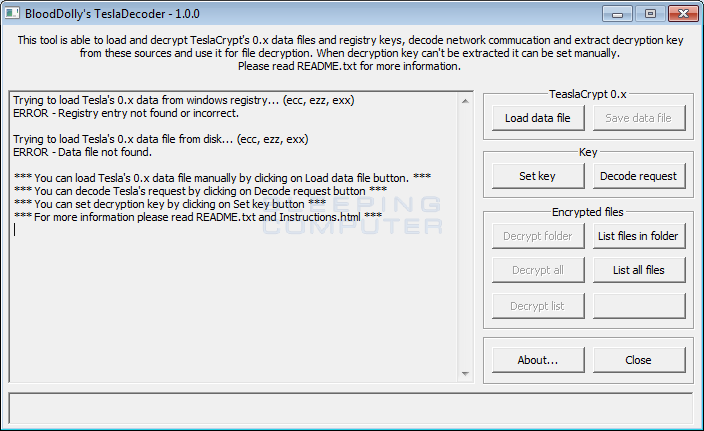
A Bleeping Computer expert with the handle BloodDolly took the key and updated an existing decryptor called TeslaDecoder. The decryptor now unlocks files encrypted by TeslaCrypt 3.0 and 4.0, including files with .xxx, .ttt, .micro and .mp3 extensions.
If CryptXXX is indeed the next darling among ransomware pushers, security researchers may have a bit of a jump on them. Exploit kits moving Locky ransomware, for example, have already shifted gears and are distributing CryptXXX, which not only encrypts local files but also chases down backup files on attached storage systems.
“So far, CryptXXX has been a much inferior ransomware compared to TeslaCrypt,” Abrams said. “TeslaCrypt showed a great deal of experienced coding and knowledge about cryptography. CryptXXX on the other have had both of their versions decrypted already.”
Researchers at Kaspersky Lab have already updated a CryptXXX decryptor twice after the criminals behind the malware rewrote and updated their code to sidestep the first version of the decryption utility.
A post on Bleeping Computer explains how to download and use TeslaDecoder.
At the outset, TeslaCrypt targeted gamers primarily, seeking out and encrypting gaming-related files on compromised computers. It was quickly folded into major exploit kits, including Angler, and before long it was raking in significant ransom money.
TeslaCrypt’s encryption was updated fairly regularly in order to steer clear of security researchers and tools trying to analyze how it worked and decrypt files it had locked down. By early this year, WordPress and Joomla sites infected with exploit kits such as Nuclear were in on the act, moving TeslaCrypt onto computers visiting those sites.
In April, researchers at Endgame Inc., found two separate TeslaCrypt updates that included new obfuscation and evasion techniques, and an expansive and new list of targeted file extensions.
This version of TeslaCrypt, 4.1A, was moving in large-scale campaigns disguised as shipping notifications, signaling a departure from moving the ransomware exclusively via exploit kits.
When version 4.1A executes the .zip attachment in the spam message, a JavaScript downloader is launched which uses Wscript, the Windows Script Host, to download the TeslaCrypt binary from greetingsyoungqq[.]com/80.exe.
Endgame researcher Amanda Rousseau said, adding that analysis of the malware has become a challenge because it initiates many code threads and debugging techniques to frustrate security tools. “It’s really like they are trying hard to hide strings in memory,” Rousseau said. “It’s much harder for [antivirus] to detect if it’s not scanning memory.”
Ransomware has become the most serious malware threat to enterprises and consumers alike. New strains such as Locky, Petya and many others seem to pop up regularly and already, some high-profile attacks have been reported against busy hospitals in California, Kentucky and the Washington, D.C. area, as well as casinos, schools and law enforcement.
It’s likely this will put much of a dent in overall ransomware distribution.
“Distribution has moved over to CryptXXX and we are seeing a new ransomware released almost every day,” Abrams said.