IT services giant Cognizant said that it has been hit by the Maze ransomware group in a cyberattack that has caused service disruptions.
Cognizant, a Fortune 500 company that employs close to 300,000 people, said that it is providing customers with indicators of compromise (IoCs) and other technical details of the attack, which first started on Friday. Public details about how the company was attacked, and which services are disrupted, are scant. Threatpost has reached out for further comment.
“Our internal security teams, supplemented by leading cyber-defense firms, are actively taking steps to contain this incident,” the company said in a statement on its website. “Cognizant has also engaged with the appropriate law enforcement authorities.”
Maze operators in an interview with Bleeping Computer, which first reported the ransomware attack, denied any association with the attack. However, according to the news outlet, Maze has historically been reserved in discussing their association with cyberattacks.
According to Bleeping Computer’s report, the listed IoCs that Cognizant provided to customers include the IP addresses of servers associated with the kepstl32.dll, memes.tmp and maze.dll files, which are known to be used previously in Maze ransomware attacks.
Vitali Kremez, who leads research with SentinelLabs, released a set of Yara rules, used for identifying malware by creating rules that look for certain characteristics, on Twitter for Maze’s tactics, techniques and procedures (TTPs) as they relate to this recent attack.
High alert related to the yet another ransomware attack perpetrated by the Maze group possibly affecting @Cognizant.
Reviewing & mitigating against the usual Maze TTPs (including RDP + remote services as an attack vector) is advisable.
✅Pushed #YARA↘️https://t.co/qcUY464fSf pic.twitter.com/z2zHL5apkm
— Vitali Kremez (@VK_Intel) April 18, 2020
Since the Maze ransomware was first discovered in 2019, its operators have made headlines in a string of recent high-profile cyberattacks, including against the city of Pensacola, Fla., in December. Maze is a particularly nasty threat because its operators often use a tactic which has been called “double extortion,” where they threaten to leak compromised data or use it in future spam attacks, if ransom demands aren’t met.
“The Maze ransomware is part of a new wave of particularly devious strains of ransomware which steal data before encrypting it and threatens to release this stolen data if the victim organisation does not pay,” said Javvad Malik, security awareness advocate at KnowBe4, in an email. “Therefore, even if an organisation has backups from which they can restore data and continue operations, it would not be enough to mitigate all the threats.”
This was seen in a November Maze ransomware attack against Allied Universal, a large American security staffing company. After the company refused to cough up the 300 Bitcoin ($2.3 million) ransom, the attackers threatened to use sensitive information extracted from Allied Universal’s systems, as well as stolen email and domain name certificates, for a spam campaign impersonating the company.
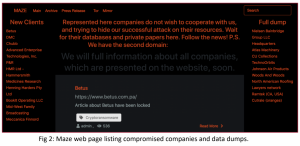
Researchers said that Maze’s operators have since created a dedicated web page, which lists the identities of their non-cooperative victims and regularly publishes samples of the stolen data. Maze has since published the details of dozens of companies, including law firms, medical service providers and insurance companies, who have not given in to their demands.
As of Monday, data associated with Cognizant had not yet been spotted on the site, according to reports.
“The latest ransomware attack on IT services provider Cognizant shows that the Maze ransomware gang isn’t backing down,” Sam Roguine, director at Arcserve, said in an email. “While the hackers have yet to threaten to publish the company’s data if the ransom isn’t paid, encrypting and leveraging data as a bargaining tool is typical for Maze, meaning that affected companies such as Cognizant must treat attacks like these as data breaches.”
Worried about your cloud security in the work-from-home era? On April 23 at 2 p.m. ET, join DivvyCloud and Threatpost for a FREE webinar, A Practical Guide to Securing the Cloud in the Face of Crisis. Get exclusive research insights and critical, advanced takeaways on how to avoid cloud disruption and chaos in the face of COVID-19 – and during all times of crisis. Please register here for this sponsored webinar.