A hacked insulin pump is the last thing a diabetic wants to worry about when life-saving fluids are pumped into their body. Sadly, concerns about medical device IT security are a healthcare reality.
Last year, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued more than a half-dozen warnings tied to connected drug pumps alone. Vulnerabilities found in pumps made by Baxter International and Becton Dickinson Alaris System, for example, could be exploited to launch a DDoS attack, alter system configurations or siphon off patient data.
The Diagnosis
Cybersecurity has also become a major theme for the Federal Drug Administration, which oversees medical-device safety. In 2020, the FDA issued a flurry of warnings urging medical device-makers and hospitals to patch their hardware against a slew of vulnerabilities, ranging from SweynTooth and URGENT/11 to Ripple20 and SigRed.
[Editor’s Note: This article is part of an exclusive FREE eBook, sponsored by ZeroNorth. The eBook, “Healthcare Security Woes Balloon in a COVID-Era World”, examines the pandemic’s current and lasting impact on cybersecurity. Get the whole neatly-packaged story and DOWNLOAD the eBook now – on us!]
Ripple20 for instance is a group of bugs found in June 2020, plaguing 53,000 medical device models. The flaws give remote attackers the ability to execute remote code, according to Forescout research.
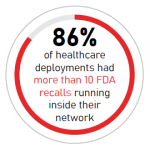
A year-long analysis of 5 million internet-of-medical-things (IoMT) devices found that 86 percent of healthcare deployments had more than 10 FDA recalls running inside their network, according to Ordr. Recalled IoMT devices can be considered either defective, posing a health risk or both.
 Underlying Symptoms
Underlying Symptoms
Experts warn medical-device security is a chronic problem, now exacerbated by COVID-era healthcare challenges. Hospitals have been forced to prioritize budgets and staffing to focus on lifesaving care – meaning that IT security often takes a back seat. Adding insult to injury, hackers are aware of this, and are also now capitalizing on these healthcare strains with a barrage of ransomware and phishing attacks and more.
Universal Health Services was one of several hospital networks hit in 2020 with ransomware attacks, causing major day-to-day disruptions to over 400 facilities across the U.S., Puerto Rico and United Kingdom. According to Tom August, a longtime CISO in the healthcare field, the medical-device aspect of such disruptions can’t be ignored.
“The likelihood is low, but there is a really high potential impact if one of these devices is attacked,” August said. “Maybe you put ransomware on my computer. That’s bad. But if you have malware on a medical device that a patient hooked up to, there is tremendous, wide-open risk to human life.”
Medical History
It should be recognized that medical-device security has long been a challenge, suffering the same uphill management battle that the entire sprawling mess of IoT gadgets has faced. That is, a lack of security-by design, unclear mechanisms for patching and updates, and the potential for configuration mistakes (like forgetting to change default passwords).
 “The coronavirus isn’t creating more vulnerabilities in medical devices, it’s laid bare the problems that already exist,” said Tim Erlin, vice president of product management and strategy at Tripwire.
“The coronavirus isn’t creating more vulnerabilities in medical devices, it’s laid bare the problems that already exist,” said Tim Erlin, vice president of product management and strategy at Tripwire.
The segment also faces some unique challenges. For instance, because of strict FDA guidelines over device configuration and legally-binding vendor support contracts, patient-care facilities often must rely on slow-to-move vendors for patching, upgrades and replacements – a rare and expensive process.
“Medical devices are a blind spot for hospitals,” August said. “In many cases, hospitals can’t manage the devices – vendors do. We can’t patch them, because vendors won’t allow it. We can’t install anti-malware protection because vendors say it breaks the warranty.”
The Cure
Reducing medical-device cybersecurity risks may be especially challenging, but there are some best practices that can help.
Taking a medical-device inventory is a first step at identifying the scope of the cybersecurity challenge. The Ordr study found that 51 percent of IT teams are unaware of what types of devices are touching their network.
Ordr also discovered Facebook and YouTube applications running on MRI and systems like Windows XP.
“Using medical devices to surf the web puts the organization at a higher risk of falling victim to a used ransomware and other malware attacks,” according to the report.
Meanwhile, suggestions for locking down IoMT devices include assessing a device’s exposure to the internet, disabling unnecessary or unused services on devices and segmenting critical networks by IoT-device needs.
Download our exclusive FREE Threatpost Insider eBook Healthcare Security Woes Balloon in a COVID-Era World , sponsored by ZeroNorth, to learn more about what these security risks mean for hospitals at the day-to-day level and how healthcare security teams can implement best practices to protect providers and patients. Get the whole story and DOWNLOAD the eBook now.










