Dozens of Mexican journalists, lawyers, and even a child, had their devices infected with commercially produced spyware during the past two years as part of an overarching campaign believed to be carried out by the nation’s government.
The spyware, Pegasus, came in the form of text messages masquerading as correspondence from the United States government, the Embassy of the United States of America to Mexico, and even emergency AMBER alerts about purportedly stolen children.
The Munk School of Global Affairs at the University of Toronto’s Citizen Lab, a research laboratory that regularly uncovers surveillance and spyware that directly impacts human rights, described the campaign in a report Monday morning. Citizen Lab calls the most recent effort as “the clearest evidence yet that government-exclusive spyware is being used in an effort to infect and monitor Mexican journalists.”
Our @citizenlab report done in collaboration with Mexican NGOS @article19mex @socialtic and @r3dmx https://t.co/lODEiOPmJk
— profdeibert (@RonDeibert) June 19, 2017
The report posits that NSO Group Technologies, a cyber arms-dealing firm based in Israel, sold the spyware suite to the Mexican government in order to spy on journalists and activists known to promote anti-corruption legislation.
The controversial company made headlines last summer after its mobile spyware Pegasus was found tied to “The Trident,” a chain of iOS zero-day exploits. Apple scrambled to fix the zero days with an emergency iOS update in August. Researchers with Lookout Security and Google found an Android variant of the software, Chrysaor, earlier this spring.
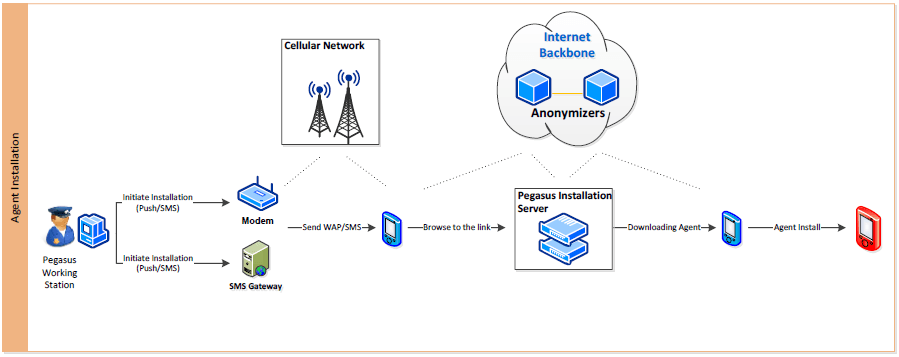
There are very few limitations to what Pegasus can do. The spyware allows third parties to take screenshots, capture audio, read email and exfiltrate data from targeted phones. It can also be used to intercept or spoof emails, thwart end-to-end encryption, and track users’ movements, researchers say.
In today’s report, Citizen Lab maintains the latest batch of individuals hit by Pegasus were either investigating or working against government corruption and human rights abuses in Mexico. Researchers at the laboratory claim they’ve verified that 11 different victims received 76 SMS messages containing NSO exploit links.
One of the victims, the son of an investigative journalist who at the time was a child, in the United States, was among those targeted–likely to gain access to his mother. Combined, the mother and son received nearly 50 malicious SMS messages, the lion’s share of those contained links to NSO’s exploit infrastructure.
While Citizen Lab can’t definitively pin the messages on the Mexican government and NSO Group, the activity fits a pattern linked to both. Researchers, assisted by Mexican non-governmental organizations R3D and SocialTic, said in a report released in February, that several Mexican government food scientists and health advocates were hit by similar, malicious links, also believed to be spread, allegedly, by the Mexican government.
In the more recent campaign, victims received text messages; some contained “personal and sexual taunts,” some warned of kidnapping.
The messages that purported to come from the U.S. Embassy tried to trick victims into clicking through by telling them there was an issue with their visa application. Other messages tried to provoke victims into clicking through by including fake news updates; one warned of armed men outside a house. Another message warned a victim they were being watched by people in a suspicious van and included images of said van.
Fake AMBER alerts, emergency broadcasts traditionally sent to mobile devices when a child has been abducted, were also sent to victims.
All messages contained links which when clicked would verify the victim’s handset model and send in turn, send back a remote exploit.
“The operation also included more mundane tactics, such as messages sending fake bills for phone services and sex-lines. Some targets only received a handful of texts, while others were barraged with dozens of messages over more than one and a half years,” the report reads.
According to Citizen Lab, the bulk of the infection attempts took place during two periods: in August 2015 and between April-July 2016.
NSO Group, which was recently put up for sale for more than $1 billion, has previously expressed that the intent of the company is to assist “authorized governments” with technology that helps them “combat terror and crime.”
“The company sells only to authorized governmental agencies, and fully complies with strict export control laws and regulations. Moreover, the company does NOT operate any of its systems; it is strictly a technology company,” the company said in a statement last August, following revelations of “The Trident” exploits.
Neither NSO Group, nor Francisco Partners Management, the private equity firm that owns the group, immediately returned to a request for comment on Monday.
According to the New York Times, which also reviewed the SMS messages and published an article on Citizen Lab’s report Monday, three unnamed Mexican federal agencies have collectively spent $80M on the NSO Group’s spyware since 2011.
As Citizen Lab points out, it’s unlikely a federal judge in Mexico would have authorized the distribution of such malware. Mexico doesn’t have any specific legal regulations on the books governing the use of malware. The law does allow for the authorization to conduct intercepts, but only when there’s an imminent threat to national security. Researchers suggest that carrying out surveillance like this is a standard – but unpoliced – practice there.
“It is difficult to conceive of what legitimate investigation would include these journalists, human rights defenders, and a minor child,” the report reads. “There is no clear basis for them to be categorized as threats to national security… Regardless of the legitimacy of the targets, this type of aggressive surveillance with malware may not pass the necessary and proportionate tests under Mexican law.”