Two fresh business email compromise (BEC) tactics have emerged onto the phishing scene, involving the manipulation of Microsoft 365 automated email responses in order to evade email security filters.
In one case, scammers are targeting victims by redirecting legitimate out-of-office (OOO) replies from an employee to them; and in the other, read receipts are being manipulated. Both styles were seen being used in the wild in the U.S. in December, when auto-responders were more prevalent due to holiday vacation.
“These tactics indicate attackers are using every available tool and loophole to their advantage in the hopes of a successful BEC attempt,” said Roman Tobe, researcher with Abnormal Security, in a posting this week.
Return to Sender: Read Receipts
In the read-receipts attack, a scammer creates an extortion email, and manipulates the “Disposition-Notification-To” email header to generate a read-receipt notification from Microsoft 365 to the recipient.
The malicious email itself may be trapped by email security solutions, but the read receipt is sent to the target anyway. It includes the text of the original email, and will be able to bypass traditional security solutions and land in the employee’s inbox, since it’s generated from the internal system.
An example:
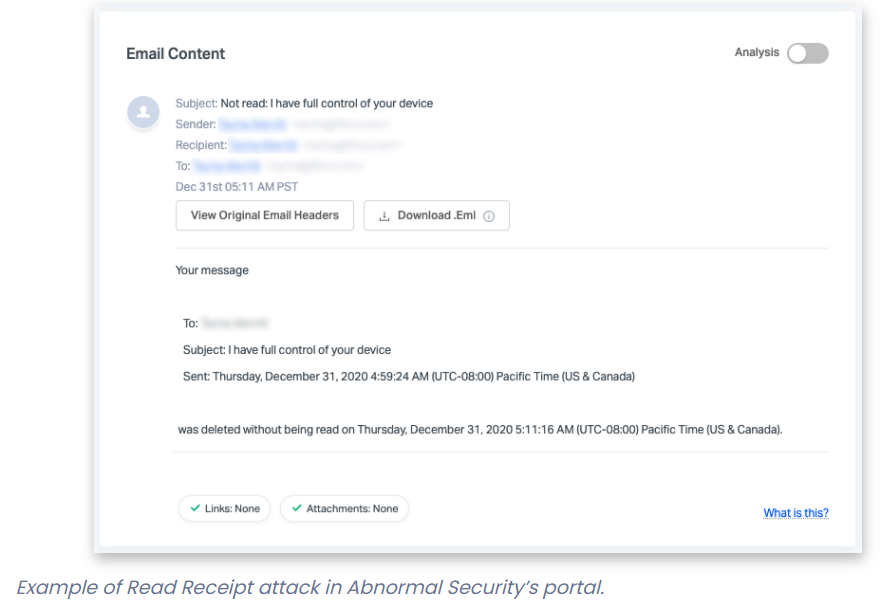
“Fear-based attacks such as these are designed to elicit an urgent response from recipients to click on a malicious link, and the attackers double down on this tactic by manipulating the email headers with fear-based language,” Austin Merritt, cyber-threat intelligence analyst at Digital Shadows, told Threatpost. “If a user clicks on a link, the compromise of their device could allow an attacker to escalate privileges across an organization’s network.”
Out-of-Office Attack
In the OOO attack, a cybercriminal creates a BEC email that impersonates someone inside the organization. The attacker can manipulate the “Reply-To” email header so that if the target has an OOO message turned on, that OOO notification (which includes the original text) will be directed to another individual within the organization.
“So, the email may be sent to one employee (let’s call them John), but the “Reply-to” header contains another employee’s email address (let’s call them Tina),” explained Graham Cluley, researcher at Bitdefender, in an analysis of the findings. “John has his out-of-office reply enabled, so when he receives the fraudulent email an automatic reply is generated. However, the out-of-office reply is not sent back to the true sender, but to Tina instead – and includes the extortion text.”
As with the read-receipt gambit, the message likely won’t be caught by email-security systems, because it originates from the original target’s account rather than someone external.
“This campaign demonstrates BEC actors’ ability to bypass security solutions and give email recipients the false impression that their account has been compromised,” said Merritt. “This is problematic for network defenders that already have traditional security solutions implemented because the phishing emails either trigger read receipt notifications or redirect to a separate recipient’s inbox, grabbing the attention of the intended victim.”
BEC: A Still-Serious Email Threat
BEC emails are designed to scam companies out of money. This is usually carried out by impersonating an employee, supplier or customer in an email or mobile message. The tactic usually involves asking for a bogus invoice to be paid; or for a recurring payment or wire transfer to be sent to a new, attacker-controlled destination.
The volume of BEC attacks has continued to grow, rising by 15 percent quarter-over-quarter in Q3 of 2020, according to Abnormal Security’s Quarterly BEC Report [PDF]. The average weekly volume of BEC attacks in the time period increased in six out of eight industries, with the biggest rise observed in the energy/infrastructure sector, at 93 percent. The industries which had the highest number of weekly BEC attacks were retail/consumer goods and manufacturing and technology.
Those campaigns geared towards invoice and payment fraud were particularly virulent, with a 155 percent QoQ, the study found.
The traditional defense for these kinds of attacks – user awareness and training to independently verify that a request is legitimate – becomes more difficult with a distributed footprint, researchers noted.
“Remote work has created more opportunity to execute BEC and other phishing attacks,” Hank Schless, senior manager of security solutions at Lookout, told Threatpost. “Without being able to walk over to another person’s desk in the office, employees will have a much harder time validating unknown texts or emails. Threat actors have taken note of these issues and are using remote work to their advantage to execute bigger BEC attacks.”
Also, as email-security systems get smarter, so are the cybercriminals. For instance, earlier in January a campaign was spotted that leverages Google’s Forms survey tool to prompt an ongoing dialogue between the email recipient and the attacker – setting them up as a victim for a future BEC trap, researchers said.
And Microsoft’s Office 365 in particular, which is the computing giant’s cloud-based Office suite, is an especially attractive avenue for BEC efforts, analysts have observed.
Microsoft and Office 365: A Ripe Target
“While Office 365 provides the distributed workforce with a primary domain to conduct business, it also creates a central repository of data and information that’s a prime target for attackers to exploit,” Chris Morales, head of security analytics at Vectra, told Threatpost. “Rather than leveraging malware, attackers are using the existing tools and capabilities already present in Office 365, living off the land to stay hidden for months.”
After attackers gain a foothold in an Office 365 environment, it’s easy for BEC scammers to leverage a trusted communication channel (i.e. sending an illegitimate email from the CEO’s official account, used to socially engineer employees, customers or partners). But there are several common bad outcomes, beyond mounting BEC attacks, he added.
These include the ability to search through emails, chat histories and files looking for passwords or other interesting data; setting up forwarding rules to obtain access to a steady stream of email without needing to sign in again; planting malware or malicious links in documents that many people trust and use, again manipulating trust to circumvent prevention controls that may trigger warnings; and stealing or holding files and data for ransom.
“The importance of keeping a watchful eye on the misuse of user access cannot be overstated given its prevalence in real-world attacks,” Morales said. “In the current cybersecurity landscape, security measures like multi-factor authentication (MFA) are no longer enough to deter attackers. SaaS platforms like Office 365 are a safe haven for attacker lateral movement, making it paramount to focus on user access to accounts and services. When security teams have solid information and expectations about SaaS platforms such as Office 365, malicious behaviors and privilege abuse are much easier to quickly identify and mitigate.”
Download our exclusive FREE Threatpost Insider eBook Healthcare Security Woes Balloon in a Covid-Era World, sponsored by ZeroNorth, to learn more about what these security risks mean for hospitals at the day-to-day level and how healthcare security teams can implement best practices to protect providers and patients. Get the whole story and DOWNLOAD the eBook now – on us!











