If it ain’t broke, don’t fix it. If there’s one thing the recent surge in threats using macros to spread malware has shown, it’s that the vector is clearly working for attackers.
Developers at Microsoft hope a feature in the latest version of Microsoft Office will reduce the frequency of those attacks by giving administrators the ability to block macros from running on machines on their network.
While macros – a series of commands stored in documents – are disabled by default on most networks, duplicitous hackers have taken to using email subject lines having to do with invoices and HR as phishing lures to get victims to open documents and enable them.
According to a post on the company’s Threat Research and Response blog this week the new macro blocking feature can be enabled on Word, Excel, and Powerpoint – either via a Group Policy, or on an individual basis.
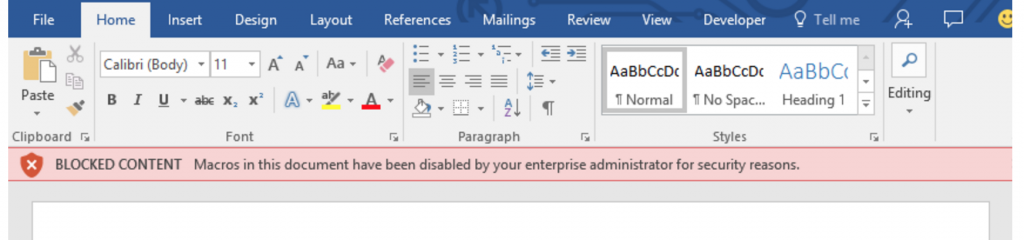
The feature, which can be found in Office’s Group Policy Management Console for Office 2016, allows admins to scope macro use to a set of trusted workflows, and block users’ ability to enable macros in scenarios it considers high risk. If a user attempts to enable macros in a document, they’re given a stricter notification, a red bar, warning them that macros have been disabled for security reasons.
“This feature relies on the security zone information that Windows uses to specify trust associated with a specific location. For example, if the location where the file originates from is considered the Internet zone by Windows, then macros are disabled in the document,” the post reads.
The company claims the mechanism should help thwart attacks spread in attachments from emails sent outside the organization, from documents downloaded from storage sites, like Dropbox and Google Drive, and from documents opened from public shares.
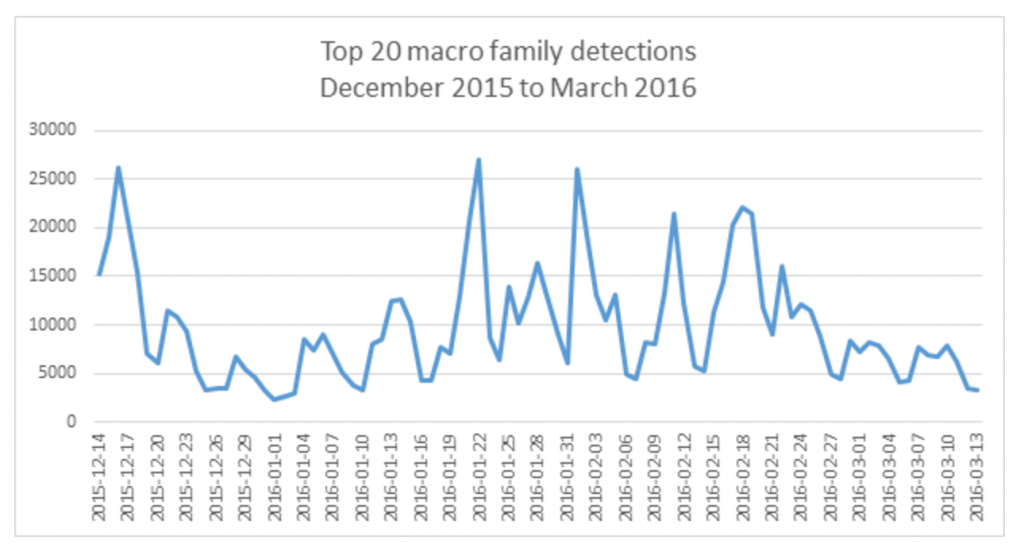
Microsoft’s Malware Protection Center first warned of campaigns beginning to use the old school technique again back in January 2015, claiming that over the course of December 2014 infections spiked to 8,000 on some days.
Since then, the technique has flourished and attackers have begun leveraging macros in document files to drop the banking Trojan Dridex, bots like Kasidet, and as of late, ransomware like Locky. While
Earlier this year attackers working with the BlackEnergy APT group were spotted using Word documents to drop payloads on Ukrainian users. The group is no stranger to using Office files; in the past they’ve also used weaponized Excel and Powerpoint documents to trick users into spreading infections.
According to stats from Microsoft’s Exchange Online Advanced Threat Protection service, the overwhelming majority of threats that target Office, 98 percent, are macros-based.
Taking the uptick in infections into account, the company is urging enterprise admins to turn on the macro-blocking feature if they haven’t already done so and turn off any workflows that involve macro usage.
“This is the most comprehensive mitigation that you can implement today.”