Microsoft lifted the curtain on a new Azure DevOps bug bounty program, designed to sniff out flaws in its Azure DevOps online services and servers.
Azure DevOps is a cloud service launched in 2018 that enables collaboration on code development across the breadth of a development lifecycle. Microsoft said its new bug bounty program, which launched on Thursday, offers rewards of up to $20,000 for eligible flaws in its Azure DevOps products, according to a Thursday post.
“We’ll continue to employ careful code reviews and examine the security of our infrastructure. We’ll still run our security scanning and monitoring tools. And we’ll keep assembling a red team on a regular basis to attack our own systems to identify weaknesses,” said Buck Hodges, director of engineering for Azure DevOps in the post.
The two in-scope services include Azure DevOps Services (formerly Visual Studio Team Services) and the latest publicly available versions of Azure DevOps Server and Team Foundation Server.
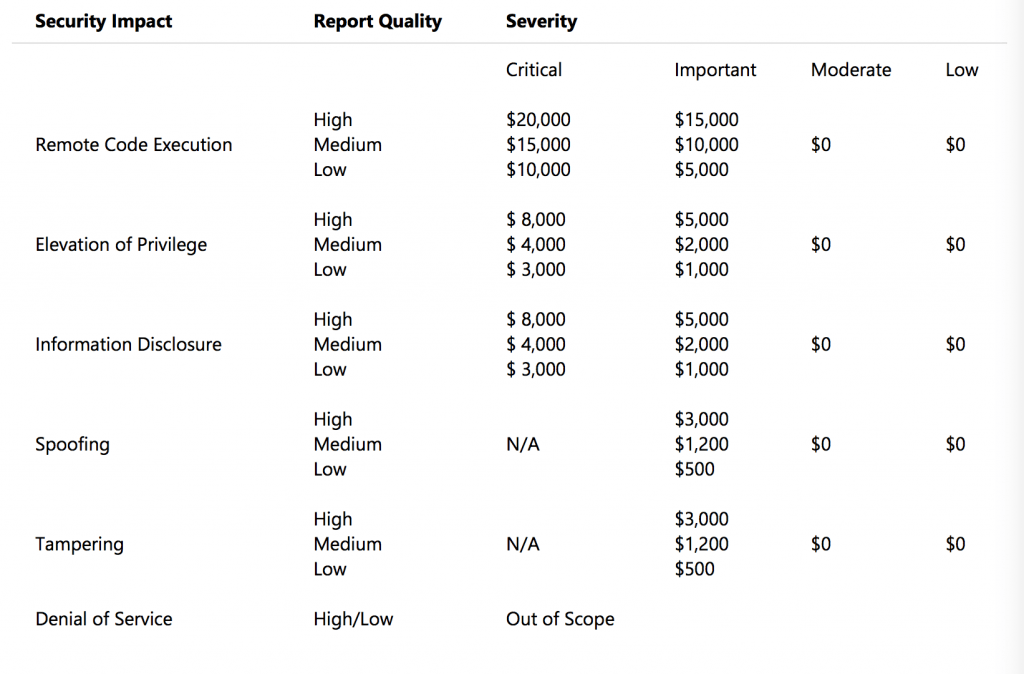
Qualified submissions are eligible for bug bounty rewards from $500 all the way up to $20,000 (see chart below).
Rewards are offered for flaws including critical and important-severity remote code execution, elevation of privilege, information disclosure, spoofing, and tampering vulnerabilities. The bounty program doesn’t have an end date and any researcher can participate, a Microsoft spokesperson told Threatpost.
“At first glance, Azure DevOps appears to have a fairly big attack surface and is packed with features which will attract a lot of bug bounty hunters,” Edwin Foudil, a security researcher who usually goes under the alias “EdOverflow,” told Threatpost. “On top of that, similar services such as GitHub and GitLab have seen great success with their bug bounty programs attracting reputable bug bounty hunters, so I can imagine some hunters will be interested in testing other development tools.”
The high-velocity application- and process-development practices collectively known as DevOps has become a core goal for many enterprises, as they look to respond to market forces more dynamically.
“As workload migration accelerates to the public cloud, security risk professionals will need to get more actively involved in their DevOps team’s processes, so they can automate the application of governance and compliance controls,” said Tim Jefferson, VP of public cloud at Barracuda Networks. “That’s why I expect to see more teams embracing automation to continuously monitor cloud security and remediate problems automatically.”
It’s only the latest recently launched bug bounty program started by the tech giant.
In July, Microsoft kicked off a bug-bounty program, offering payouts as high as $100,000 for holes in identity services and implementations of the OpenID standard.
The bounty program touches on Microsoft’s array of digital identity solutions, which tout strong authentication, secure sign-in sessions and API security. Those solutions include Microsoft Account and Azure Active Directory, which offer identity and access capabilities for both consumer and enterprise applications – as well as its OpenID authentication protocol.
And in March, in the wake of the Meltdown and Spectre flaws, Microsoft started a new bug bounty program targeting speculative execution side channel vulnerabilities. That limited time program operated until December 31, and offers up to $250,000 for identifying new categories of speculative execution attacks that Microsoft and other industry partners are not yet aware of.