A phishing campaign was recently discovered leveraging OneNote, Microsoft’s digital notebook that automatically saves and syncs notes, to bypass detection tools and download malware onto victims’ systems.
The attacker was utilizing OneNote as a way to easily experiment with various lures that either delivered the credential-stealing Agent Tesla keylogger or linked to a phishing page – or both. The attack first started with an email to victims that contained a link to the OneNote document.
“Thanks to the ease of use and accessibility of OneNote, the threat actor was able to update a ‘phishing notebook’ multiple times a day, experiment with various intrusion methods, and improve the odds to successfully evade email security controls,” said researchers with Cofense in a Tuesday analysis. “Numerous Agent Tesla Keylogger payloads as well as links to different credential phishing websites were included in the campaign.”
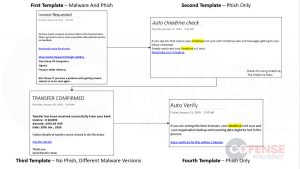
The threat actor first sent an email to companies purporting to be a marketing manager sending an order invoice (Cofense did not list the scope of targets or how effective the campaign has been thus far). The link to the order request invoice was actually a tiny[.]cc link, which eventually brought victims to a OneNote document. Over the span of two weeks, researchers said that threat actors swapped out the layout of this OneNote page, cycling between four different templates to deliver a credential phishing portal and unique malware samples.
For instance, in one of the earlier template versions the page sends two URLs – one with an Office 365 credential phishing page and the other that downloads malware. Other later template versions were tweaked so that they linked to malware downloads rather than also linking to credential phishing sites.
The various OneNote versions had different lures as well. One told victims that a transfer had been successfully received from their bank invoice and told them to click on a link to view the details of the transfer (which actually downloaded malware), while another told them that their OneDrive isn’t synced with their organization’s backup, and asked them to “auto verify” in order to fix the issue — which brought them to a phishing page. 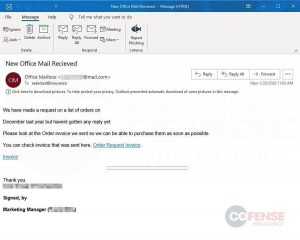
In all cases where malware was delivered, the malware was a first-stage downloader, which attempted to download an encrypted binary. This binary, the Agent Tesla keylogger, was then decrypted and run in memory. Agent Tesla, used in various campaigns over the years, collects and exfiltrates stored logins and keystrokes on victims’ systems. Interestingly, the malware tied to this specific campaign failed due to improper customization, indicating that the threat actor may be inexperienced, researchers said.
“Initially, the two first-stage malware downloaders had their encrypted payloads stored on Google Drive,” said researchers. “Newer loaders attempted to fetch payloads from a compromised host, the same host that provided the malware downloaders. The newer loaders did, however, fail to accomplish their tasks due to improper customization by the threat actor. Such error is indicative of a less-capable operator who leverages pre-made kits but falls short on modifying them.”
Microsoft OneNote
The use of OneNote in this campaign gives attackers several advantages, said researchers. For one, it allowed the threat actor to easily swap between various templates and adapt to different lures for different victims. The use of OneNote also allowed threat actors to slip their phishing attack against traditional defenses set up in environments protected by Microsoft Exchange Online Protection and FireEye enterprise gateways.
“Based on the inherent risk posed by trusted sources, traditional protections trained against OneNote and similar services may prove ineffective,” said researchers. “If not properly addressed, this could pave the way to a prolific infection vector for malware.”
Beyond OneNote being hosted on OneDrive, cybercriminals can – and have been found to – leverage a wide array of trusted cloud hosting sources for credential phishing, including documents hosted on Microsoft Sway, Microsoft SharePoint, Google Docs or even Zoho Docs (offered up by CRM software and free mail provider Zoho).
“Having a readily accessible service that requires no maintenance and effectively acts as a free database significantly lowers the upkeep needed for the credential phish,” said researchers. “A downside is that these services have evolved to look for nefarious activity, and Google displays a warning at the bottom of the form that warns the user to ‘never submit passwords through Google Forms.’ Other services such as Microsoft Forms and survey sites can also enable this type of attack.”
Interested in security for the Internet of Things and how 5G will change the threat landscape? Join our free Threatpost webinar, “5G, the Olympics and Next-Gen Security Challenges,” as our panel discusses what use cases to expect in 2020 (the Olympics will be a first test), why 5G security risks are different, the role of AI in defense and how enterprises can manage their risk. Register here.