Microsoft on Tuesday released a patch for a zero-day vulnerability that was discovered late last week and used to spread the Dridex banking Trojan.
Attacks were spreading via a massive spam campaign where emails contain Microsoft Word documents with malicious attachments that exploited a vulnerability in the way Microsoft handles OLE2Link objects. According to researchers, the attacks were effective at bypassing most mitigation efforts.
The patch was part of Microsoft’s scheduled Patch Tuesday software updates.
“This is the first campaign we have observed that leverages the newly disclosed Microsoft zero-day,” Proofpoint wrote in a technical analysis of the zero day. “This represents a significant level of agility and innovation for Dridex actors.”
The Microsoft zero-day vulnerability, according to Proofpoint, was extremely effective. “When recipients open the document, the exploit–if successful–is used to carry out a series of actions that lead to the installation of Dridex botnet ID 7500 on the user’s system,” researchers wrote.
“The Microsoft OLE2Link object can open application data based on the server-provided MIME type, which can allow an unauthenticated remote attacker to execute arbitrary code on a vulnerable system,” according an advisory released by the DHS-sponsored CERT hosted at the Software Engineering Institute at Carnegie Mellon University.
The zero-day, first reported by McAfee on Friday, is notable because in most cases macro-laden documents attached to emails are blocked by mitigations built into Office and Microsoft’s Windows 10. In this case, users also do not have to enable macros for the exploit to execute.
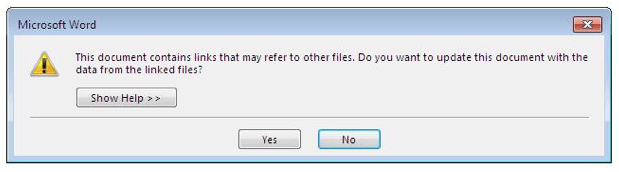
In a test by Proofpoint, a system was exploited just by opening an Office 2010 document. As the document opened, users were presented with a dialogue box that asked “This document contains links that may refer to other files. Do you want to update this document with the data from the linked files?”
According to Proofpoint, “user interaction was not required” and once the dialogue box appeared, the Dridex malware injection process began.
The attack involves a Microsoft Office RTF document that contain an embedded OLE2link object. “When the user opens the document, winword.exe issues a HTTP request to a remote server to retrieve a malicious .hta file, which appears as a fake RTF file,” according to an analysis of the zero day by FireEye researchers.
The HTA application then loads and executes malicious scripts that halt the winword.exe loading process. Next, the scripts download payloads and load a decoy document for the user to see, according to FireEye.
“The original winword.exe process is terminated in order to hide a user prompt generated by the OLE2link,” FireEye researcher wrote.
“Clearly the fact that the RTF file is able download the malicious HTML that enables local execution of malware points to a lack of control in interpreting untrusted input from the outside world,” said Paul Farrington, manager of EMEA Solution Architects at Veracode. “The Microsoft engineers will not only need to devise a patch for this vulnerability, but also to remodel their threat assessment of this type of file interaction,” Farrington said.
The spam campaigns delivering the zero day spoofed the recipient’s domain in the sender’s email address and appear to be from either “copier”, “documents”, “noreply”, “no-reply”, or “scanner”. The subject line in all cases is “Scan Data” and included attachments named “Scan_123456.doc” or “Scan_123456.pdf” – with the numbers randomly generated.
The vulnerability affects Microsoft Office, including the latest Office 2016 edition running on Windows 10.
Mitigation includes installing the Microsoft patch. However, Microsoft notes “you must have the release version of Service Pack 2 for Office 2010 installed on the computer” to apply the security update. Alternatively, security experts recommend blocking RTF documents in Microsoft Word via the File Block Settings in the Microsoft Office Trust Center. They also recommend using Microsoft Office Protected View, which they say can help prevent exploitation without user interaction.