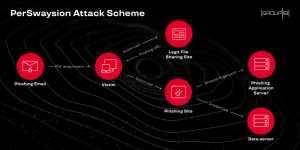
A highly targeted phishing campaign, with a Microsoft file platform twist, has successfully siphoned the Office 365 credentials of more than 150 executives since mid-2019.
Researchers attribute the campaign’s success to two parts: First, it leverages multiple Microsoft file-sharing services to convince victims to hand over their credentials. That includes Microsoft’s Sway platform used for newsletters and presentations (its use of Sway, in fact, inspired researchers to name the campaign “PerSwaysion”), as well as the SharePoint and OneNote collaboration platforms. Second, the initial phishing emails are sent from legitimate but previously compromised email addresses — which cloak the fact that they’re attacker-controlled.
Multiple threat groups are working together to carry out PerSwaysion, according to researchers.
“PerSwaysion campaign is yet another living example of highly specialized phishing threat actors working together to conduct effective attacks on a large scale,” said Feixiang He, senior threat intelligence analyst at Group-IB in a Thursday analysis.” The campaign phishing kit is primarily developed by a group of Vietnamese-speaking malware developers, while campaign proliferation and hacking activities are operated by other independent groups of scammers.”
The ongoing PerSwaysion campaign has targeted small- and medium-sized financial services companies, law firms and real estate groups across the U.S., Canada, Germany, the U.K. and other countries. Its impact is serious: Access to executives’ Office 365 accounts gives attackers a full range of top-level, sensitive corporate data, as well as the ability to launch subsequent phishing attacks on other high-profile targets.
The Campaign
Researchers first discovered PerSwaysion after inspecting a phishing email that came from an external business partner of the victim. While the initial email had some small red flags (strange typos in the body of the email, for example), the sender used a legitimate email address of the victim’s actual partner.
The email read, “Please+see+above+document+from[redacted] for your review and let me know if you have any concerns.” The document being referenced is a PDF file attachment, which pretends to be a notification for Office 365 file sharing. The “notification” includes the full name, email address and sender’s company to add an air of legitimacy – -however, researchers noted that it also contains glitchy, random strings (likely bugs in the automation software used by scammers to generate the PDF files).
If victims click on the link, its then sends them to yet another file pretending to be associated with Office 365, this one hosted on Microsoft Sway’s platform.
“For untrained eyes, this page resembles an authentic Microsoft Office 365 file-sharing page,” said researchers. “However, this is a specially crafted presentation page which abuses Sway’s default borderless view to trick the victim [into thinking it was] part of the Office 365 official login page.”
 The page tells the recipient that the sender has shared a document on behalf of the company, and again asks the target to click on a button to “Get Started.” Finally, this last link redirects the victim to the actual phishing landing page, which purports to be a Microsoft Single Sign On (SSO) page for Outlook, and asks the victim to input their credentials. This SSO page actually appears to be part of a phishing kit that’s been re-used over a long period of time — the kit developer copied a version of Microsoft’s Outlook login page from 2017.
The page tells the recipient that the sender has shared a document on behalf of the company, and again asks the target to click on a button to “Get Started.” Finally, this last link redirects the victim to the actual phishing landing page, which purports to be a Microsoft Single Sign On (SSO) page for Outlook, and asks the victim to input their credentials. This SSO page actually appears to be part of a phishing kit that’s been re-used over a long period of time — the kit developer copied a version of Microsoft’s Outlook login page from 2017.
“When the victim submits his or her corporate Office 365 credentials as if for a normal login, the sensitive data is sent to a separate data server with an extra email address which is hidden on the page,” said researchers. “This extra email seems to be used as a real-time notification method to make sure scammers react on freshly harvested credentials.”
Different attack variants swap in other file-sharing platforms, including Microsoft SharePoint and OneNote. By going to such lengths in using Microsoft’s services, “the scammers pick legit file-sharing services which have the ability of rendering seamless preview of uploaded files with phishing links,” researchers noted. “This key feature helps scammers construct web pages that strongly resemble authentic Microsoft experience.”
Follow Up Operations
After swiping victims’ credentials, the attackers then rinse and repeat the attack by targeting victims’ email correspondents.
After logging into victim email accounts to double-check that they’re valid, they then access the victims’ corporate email server and dump their email data. Then, the attackers generate new phishing PDF files using the victims’ full names, email addresses, company legal names and sometimes victims’ official titles. These PDFs are then sent to users who victims have interacted with recently.
“These PDF files are sent to a selection of new people who have recent email communications with the current victim,” said researchers. “It’s of note that PerSwaysion scammers typically delete impersonating emails from the victim’s outbox to avoid suspicion.”
Inbox security is your best defense against today’s fastest growing security threat – phishing and Business Email Compromise attacks. On May 13 at 2 p.m. ET, join Valimail security experts and Threatpost for a FREE webinar, 5 Proven Strategies to Prevent Email Compromise. Get exclusive insights and advanced takeaways on how to lockdown your inbox to fend off the latest phishing and BEC assaults. Please register here for this sponsored webinar.
Also, don’t miss our latest on-demand webinar from DivvyCloud and Threatpost, A Practical Guide to Securing the Cloud in the Face of Crisis, with critical, advanced takeaways on how to avoid cloud disruption and chaos.