Researchers with Microsoft have spotted a spike in Crowti, a ransomware similar to Cryptolocker that encrypts files on victims’ machines and then asks for payment to unlock them.
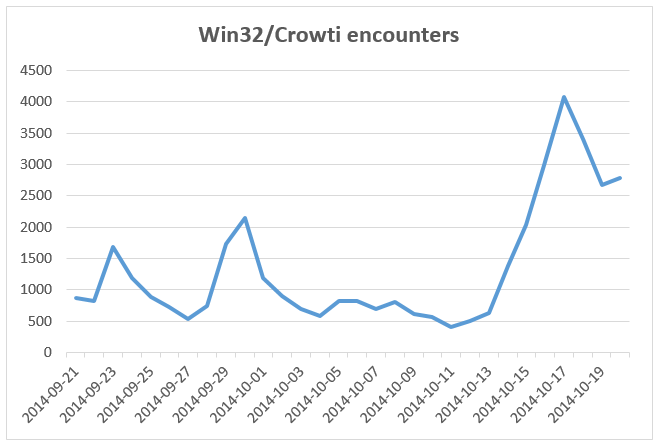
The malware has existed for several months but it wasn’t until mid-October that Microsoft’s Malware Protection Center noticed its biggest swell to date. The campaign infected 4000 different systems at its peak, with the bulk of those, 71 percent, confined to machines in the United States.
Similar to CryptoWall, a fairly recent Cryptolocker variant, Crowti uses a valid digital signature to appear legitimate and then, once installed, demands users pay in Bitcoin to purportedly decrypt their files.
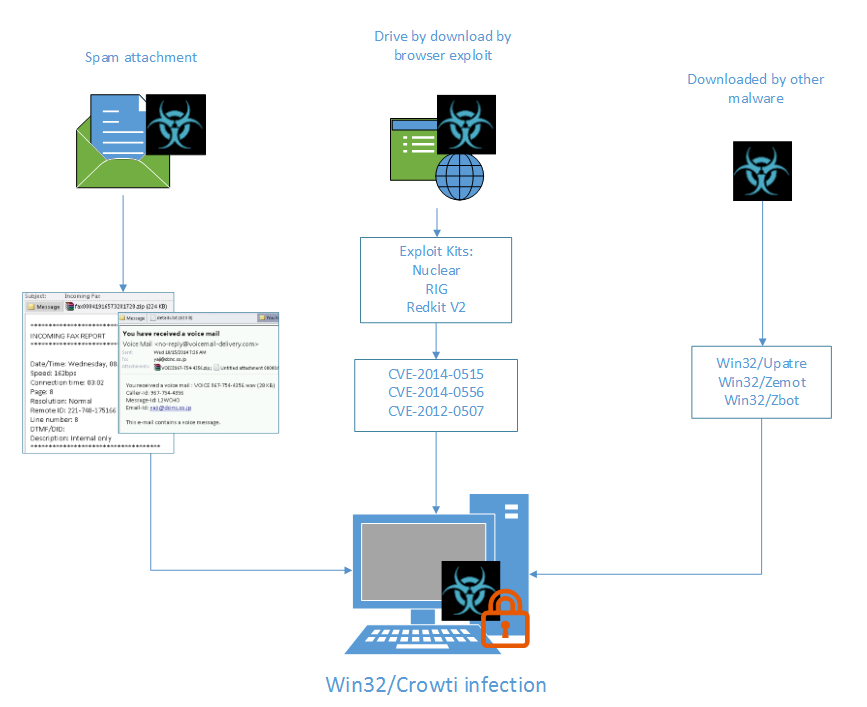
Like most ransomware campaigns, Crowti relies on several methods of infection.
Primarily it’s being launched via .ZIP files that come as an attachment in spam emails. Microsoft has discovered a handful of generically titled attachments – VOICE, IncomingFax, document, Complaint_IRS_id, etc. – all designed to dupe users into clicking and installing the malware.
Researchers have also seen Crowti propagating via popular exploit kits like Nuclear, RIG and RedKit V2, exploiting old and out-of-date versions of Adobe Flash and Oracle Java.
Most of the exploits being used to spread Crowti have long since been patched. Adobe remedied CVE-2014-0556 just last month and 2014-0515 in April while Oracle pushed an update to address the Java issue, CVE-2012-0507, way back in February 2012 but that hasn’t stopped attackers from targeting depreciated apps running on those systems.
Crowti has also made its way onto systems alongside other types of malware, including Upatre, Zbot and Zemot, according to Microsoft, who warned of the ransomware in a blog entry on Tuesday.
While Crowti shares several traits with other types of ransomware, it’s even borrowing their names as well. In some cases Microsoft claims the malware is branding itself as CryptoWall or CryptoDefense when it informs victims their information has been encrypted. Like CryptoWall and its variants, Crowti eventually directs its victims to a Tor page and gives them instructions on how to purchase Bitcoin to unlock their information.
The similarities don’t end there.
Much like how Barracuda Labs discovered a CryptoWall variant with a valid digital signature last month, Microsoft stumbled upon a sample of Crowti at the end of September that was also being distributed with a seemingly legitimate certificate.
That certificate—since revoked, like the CryptoWall variant, was issued by Comodo yet researchers claim they’ve seen instances of the ransomware using a certificate from The Nielsen Company as well.