Employers who receive an email from someone purporting to be a job applicant, with an attached resume, could fall victim to a difficult-to-detect phishing campaign peddling a remote-access tool used often for espionage.
Researchers with Cofense said they have recently spotted emails with malicious attachments delivering the Quasar open-source malware. While the “job seeker” phishing theme may be fairly common, this particular campaign employs several sophisticated tactics that make it harder both for researchers to analyze — and company employees to detect.
“Organizations find a higher degree of difficulty with the ‘.doc’ file attachment distributing Quasar RAT itself, because the document employs a multitude of measures to deter detection,” Max Gannon, with Cofense, said in a Monday post. “Such methods include password protection—which is a built-in feature of Microsoft Word—and encoded macros.”
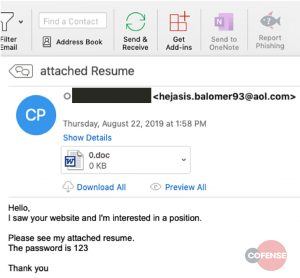
The phishing emails purport to be from a job-seeker, with the message reading, “Hello, I saw your website and I’m interested in a position. Please see my attached resume.” The message, which researchers told Threatpost was intended for hiring managers or someone from the HR department, then points to an attached Microsoft Word doc “resume.” This attachment, titled “0.doc,” in actuality delivers malware and uses several counter-detection measures.
The phishing attachment utilizes a built-in Microsoft password protection technique, and looks to trick victims into bypassing the typical “security warning” pop-ups.
Researchers said that by making the attachment password-protected, the threat actor is hoping to be able to bypass automated security systems. They’re not able to open and scan the attachment due to the inability to read and insert the password.
The phishing message tells victims to enter a password (“123”) to view the document: “A password of ‘123’ is not particularly inventive, but to an automated system that processes attachments separately from emails it means that the document will be opened and no malicious activity will be recorded because the system has not determined either a need for a password or what the password is,” researchers said.
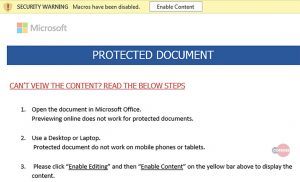
Then, once the document has been clicked, a message appears that it’s a “Protected Document,” which urges users to click on “Enable Content,” next to the warning bar that states that macros have been disabled.
In another attempt to evade detection, the attachment contains more than 1,200 lines of garbage code that appears to be base64-encoded – meaning if researchers attempt to decode it to analyze the document, it will crash due to the magnitude of decoding required.
 “If an analyst or automated system were then to attempt to analyze the macros using an analysis tool (such as the popular tool ‘olevba’ by Philippe Lagadec), the script would fail and potentially crash from using too much memory when it attempted to analyze the macro,” researchers said.
“If an analyst or automated system were then to attempt to analyze the macros using an analysis tool (such as the popular tool ‘olevba’ by Philippe Lagadec), the script would fail and potentially crash from using too much memory when it attempted to analyze the macro,” researchers said.
Finally, even if researchers attempt to decode the strings, the resulting content still lacks the payload URL, and partial strings and filler text give it some semblance of legitimacy. Portions of the payload URL, as well as additional information, are in fact hidden as meta-data for images and objects that were embedded in the document, researchers said.
Finally, the attack avoids detection by downloading a Microsoft self-extracting executable, which then unpacks a Quasar RAT binary at 401MB. The large size of this archive also makes it more difficult for researchers to analyze it.
The Quasar RAT, for its part, is a publicly available, open-source RAT and can be found on GitHub. It “has been observed being used maliciously by advanced persistent threat (APT) actors to facilitate network exploitation,” according to a US-CERT report, and has the capabilities to steal passwords, log keystrokes, take screenshots and record webcam footage.
However, “since the tool is easily accessible, attributing the activity to a specific threat actor is tedious at best,” researchers said.
Interested in more on the internet of things (IoT)? Don’t miss our free Threatpost webinar, “IoT: Implementing Security in a 5G World.” Please join Threatpost senior editor Tara Seals and a panel of experts as they offer enterprises and other organizations insight about how to approach security for the next wave of IoT deployments, which will be enabled by the rollout of 5G networks worldwide. Click here to register.