A botnet of connected things strung together by the Mirai malware is responsible for Friday’s distributed denial-of-service attacks against DNS provider Dyn. The DDoS attacks impacted Internet service on the East Coast of the United States, and were responsible for keeping Dyn and a number of its high-profile customers offline during different times during the day.
Level 3 Communications, a large service provider located in Colorado, said that it was monitoring the attacks and that it believed 10 percent of the IP-enabled cameras, DVRs, home networking gear and other connected devices compromised by Mirai were involved in Friday’s attacks.
Mirai’s purpose is to continuously scan the public Internet for IoT devices and tries to access them using known default or weak credentials before exploiting and forcing devices to join botnets used in DDoS attacks. The danger posed by Mirai was exacerbated when the hacker allegedly responsible for a 620 Gbps DDoS attack against Krebs on Security and French webhost OVH released the source code for the malware to the public.
Level 3 and security company Flashpoint confirmed on Friday that Mirai was behind Friday’s attacks, which were still ongoing as of last night. Flashpoint said it is working with law enforcement and other resources to track the source of the attacks.
Dyn, a New Hampshire-based DNS provider, said the attacks began shortly after 7 a.m. Eastern time and the first wave ended at 9:36 a.m., before ramping up again at 11:52 a.m. when a second attack targeted its managed DNS platform.
“This attack was distributed in a more global fashion,” Dyn said in a status update Friday afternoon.
The New York Times said Friday that the FBI and the Department of Homeland Security were investigating the attacks and were not ruling out either criminals or nation-state actors as responsible parties.
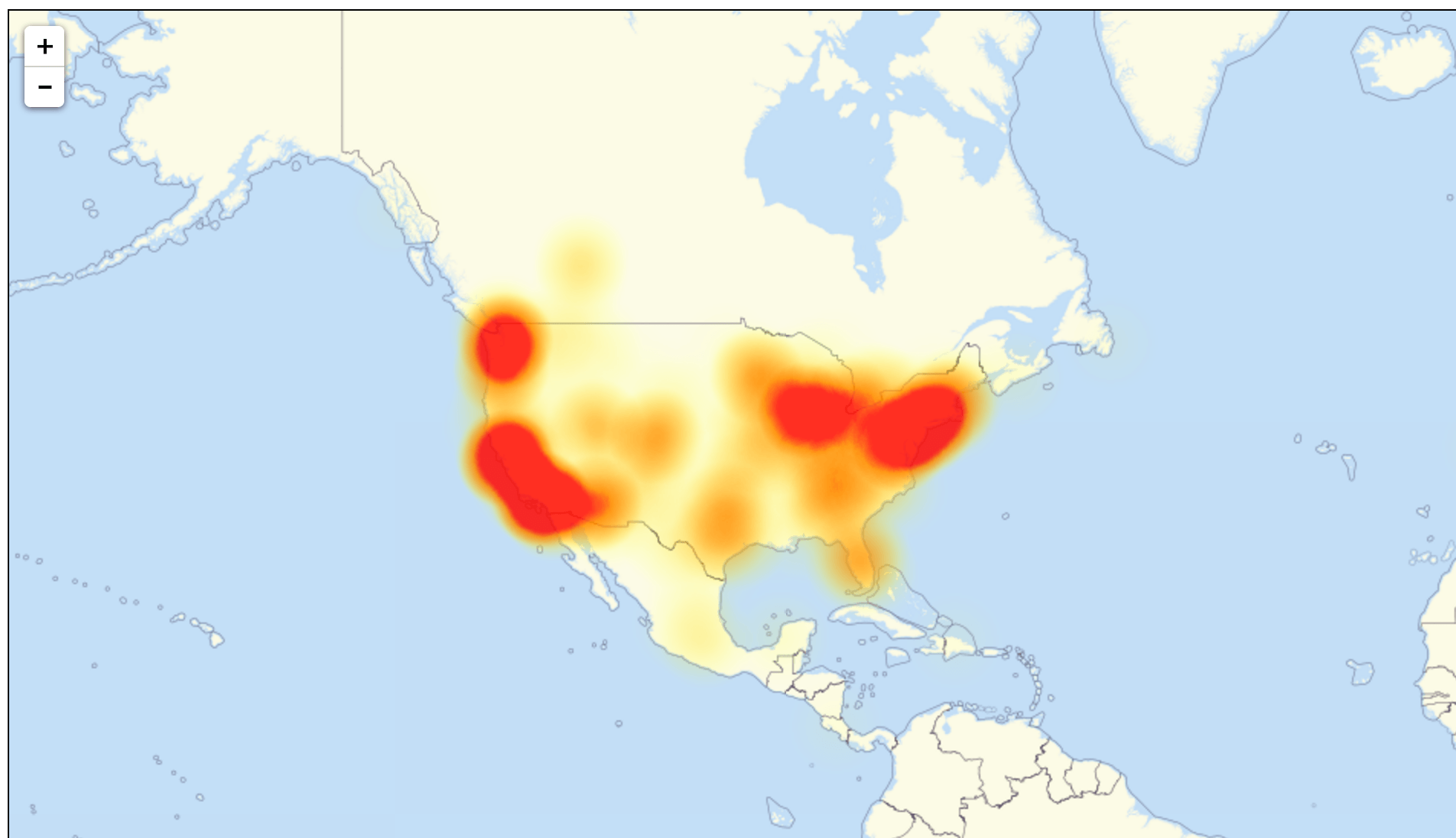
Dale Drew, CISO of Level 3 Communications, said this afternoon on Periscope that the Mirai botnet was at about 550,000 nodes, and that approximately 10 percent were involved in the attack on Dyn (Level 3’s outage map is below). Earlier this week, Level 3 identified much of the command and control infrastructure used to communicate with bots, and said the number of bots had more than doubled since the source code as released.
“We are seeing others involved as well,” Drew said. “Mirai is a DDoS-for-rent environment. People buying time on that botnet could be buying time on other botnets as well. They are hitting a number of other DNS sites as well.” Drew did not identify those sites.
DNS providers translate domain names into IP addresses. In Friday’s attacks, someone used compromised connected devices to make an overwhelming number of queries of Dyn and other providers, so much so that they’re unable to keep up and answer legitimate queries.
On Friday, prominent services such as Twitter, Github, Spotify, Reddit, SoundCloud and others were inaccessible for periods of time.
“When the directory service is down, DNS cannot provide and IP address and you cannot get to the host,” Drew said. “It looks like the host is down when, in fact, is the directory service that is down.”
Earlier this week, Level 3 said that a number of attackers were taking advantage of the publicly available source code to hack into IoT devices; it said, for example, that 24 percent of the bots in the Mirai botnet overlapped with another IoT botnet uncovered this summer called Bashlite.
The major source of bots used in the Krebs and OVH attacks are connected DVRs manufactured by XiongMai Technologies of China. The DVRs used in the attack share the same username-password combination root:xc3511 making it child’s play for the attackers to telnet into the devices and recruit them into botnets, Flashpoint said.
“Unlike your PC or your phone, IoT devices don’t have the memory and processing to be secured properly, so they are easily compromised by adversaries and it’s very difficult to detect when that happens,” said Core Security’s Chris Sullivan. “This is what’s driving the new ultra-high volume DDoS attacks like we saw today. Ultra-large IoT botnets are instructed to make so many superfluous requests of the target that legitimate requests cannot get through. No real damage is done but service is denied for legitimate users.”