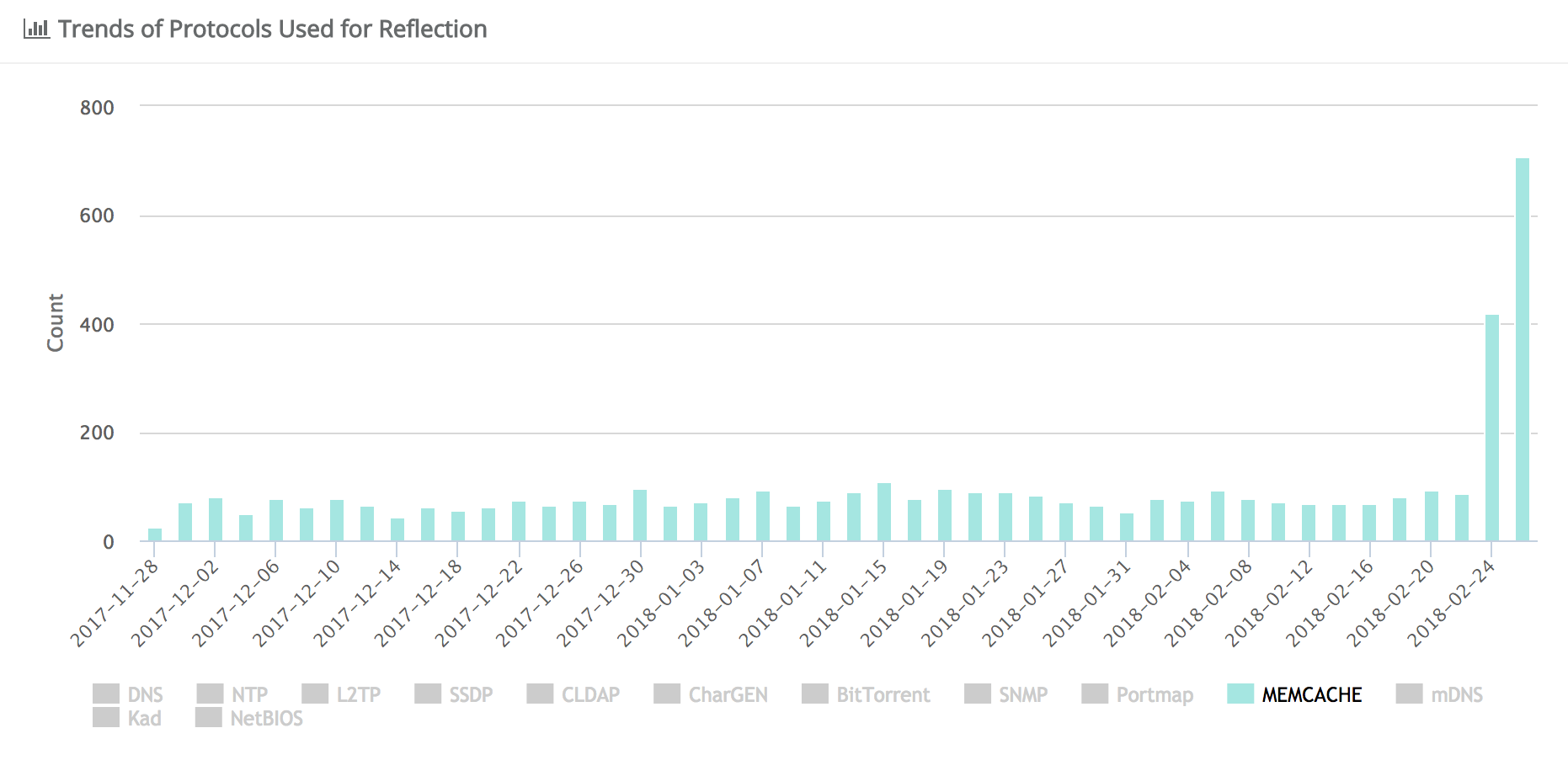
Cybercriminals behind distributed denial of service attacks have added a new and highly effective technique to their arsenal to amplify attacks by as much as 51,200x by using misconfigured memcached servers accessible via the public internet.
The technique was reported by Akamai, Arbor Networks and Cloudflare on Tuesday. All said they have observed an uptick in DDoS attacks using User Datagram Protocol (UDP) packets amplified by memcached servers over the past two days. Memcached servers are a type of server used to bolster responsiveness of database-driven websites by improving the memory caching system.
“Unfortunately, there are many memcached deployments worldwide which have been deployed using the default insecure configuration,” wrote Marek Majkowski, a Cloudflare engineer, in a technical description of the DDoS attacks posted on Tuesday.
Reflection attacks happen when an attacker forges its victim’s IP addresses in order to establish the victim’s systems as the source of requests sent to a massive number of machines. The recipients of those requests then issue an overwhelming flood of responses back to the victim’s network, ultimately crashing that network. These types of DDoS attacks differ from amplification attacks, where publicly accessible open DNS servers are used to flood victims with DNS responses.
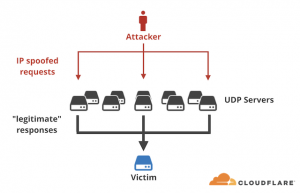 In the case of the amplification attacks identified by Akamai, Arbor Networks and Cloudflare, attackers were able to send a small byte-sized UDP-based packet request to a memcached server (on port 11211). The packets would be spoofed to appear as if they were sent from the intended target of the DDoS attack. In response, the memcached server responds by sending the spoofed target a massively disproportionate response.
In the case of the amplification attacks identified by Akamai, Arbor Networks and Cloudflare, attackers were able to send a small byte-sized UDP-based packet request to a memcached server (on port 11211). The packets would be spoofed to appear as if they were sent from the intended target of the DDoS attack. In response, the memcached server responds by sending the spoofed target a massively disproportionate response.
“Fifteen bytes of request triggered 134KB of response. This is amplification factor of 10,000x! In practice we’ve seen a 15 byte request result in a 750kB response (that’s a 51,200x amplification),” Majkowski said.
The implications of such an attack that requires so little resources with such a massive impact are far reaching on not only intended targets but also critical network infrastructure, researchers said.
“It is difficult to determine the exact amplification factor of memcached, but the attacks Akamai saw generated nearly 1 Gbps per reflector. Other organizations have reported attacks in excess of 500 Gbps using memcached reflection,” according to a Akamai SIRT Alert posted Tuesday.
By comparison, in 2016 security journalist Brian Krebs’ Krebs on Security website suffered a massive DDoS attacks, peaking at more than 620 Gbps of sustained traffic aimed at his site. That attack of course leveraged resource-intensive Mirai malware infected IoT botnets.
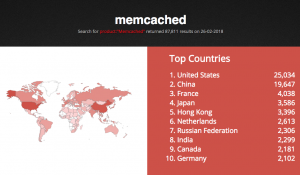 According to estimates, there are over 88,000 misconfigured open memcached servers vulnerable to abuse. Vulnerable memcached servers have been identified globally, with the highest concentration in North America and Europe, Cloudflare said.
According to estimates, there are over 88,000 misconfigured open memcached servers vulnerable to abuse. Vulnerable memcached servers have been identified globally, with the highest concentration in North America and Europe, Cloudflare said.
Making matters worse, memcached servers support UDP, an alternative communications protocol to Transmission Control Protocol and also considered ripe for abuse in amplification attacks.
“The (UDP) protocol specification shows that it’s one of the best protocols to use for amplification ever! There are absolutely zero checks, and the data WILL be delivered to the client, with blazing speed! Furthermore, the request can be tiny and the response huge,” Cloudflare researchers noted.
Mitigation includes configuring memcached servers to operate behind a firewall and turning off support for UDP.
“Similar to most reflection and amplification attacks before it, the primary solution to memcached attacks is to not have the reflectors exposed to the Internet. However, relying on remote systems administrators to remove their servers from the Internet is not a solution likely to see immediate results. In the meantime, organizations need to be prepared for more multigigabit attacks using this protocol and should plan accordingly,” Akamai said.