A set of address-bar spoofing vulnerabilities that affect a number of mobile browsers open the door for malware delivery, phishing and disinformation campaigns.
The bugs, reported by Rapid7 and independent researcher Rafay Baloch, affect six browsers, ranging from the common (Apple Safari, Opera Touch/Mini and Yandex), to the less common (Bolt Browser, RITS Browser and UC Browser). They allow an attacker to present a fake address for a web page – which is a problem in the mobile world, where a URL is often the only verification of legitimacy that users have before navigating to a website.
“Mobile browsers are a pretty special sort of software that end up acting as a user’s multipass for all types of critical applications in their day-to-day life,” explained Rapid7 research director Tod Beardsley, in a blog post on Tuesday. “Essentially, if your browser tells you that a pop-up notification or a page is ‘from’ your bank, your healthcare provider or some other critical service you depend on, you really should have some mechanism of validating that source. In mobile browsers, that source begins and ends with the URL as shown in the address bar. The fact of the matter is, we really don’t have much else to rely on.”
Because of the lack of real estate for security indicators on the mobile screen, browsers usually block developers from altering anything in the address bar. What’s shown on the screen must correspond with where the page is actually hosted, making it almost impossible to convincingly spoof the location of text or images. However, this group of bugs allows attackers to get around such protections.
“The bugs allow attackers to interfere with the timing between page loads and when the browser gets a chance to refresh the address bar,” said Baloch, in a technical paper also posted on Tuesday. “They can cause either a pop-up to appear to come from an arbitrary website or can render content in the browser window that falsely appears to come from an arbitrary website.”
Baloch released a proof-of-concept (PoC) exploit demonstrating the browser-based spoofing vulnerability in Safari for both iOS and Mac (CVE-2020-9987).
“The vulnerability occurs due to Safari preserving address bar of the URL when requested over an arbitrary port, the set interval function reloads bing.com:8080 every 2 milliseconds,” he explained. “Hence, the user is unable to recognize the redirection from the original URL to spoofed URL. What makes this vulnerability more effective in Safari by default does not reveal port number in URL unless and until focus is set via cursor.”
Essentially, all of this means that an attacker could set up a website for phishing, spreading malware or spoofing news sources for disinformation purposes, and then send the URL to a target via email, SMS or messaging app, or social media.
“Imagine a text message from a spoofed phone number that says, ‘There is an important message from your payment processor, click here,’ and then you click without really looking, and end up on a web page that clearly (but falsely) says it’s PayPal, and hey, can you give up your password real quick?” Beardsley noted. “This seems like a pretty effective attack, given that the address bar is really the only signal you have to tell ‘where’ your browser ‘is.'”
Here’s a list of affected browsers and assigned CVEs:
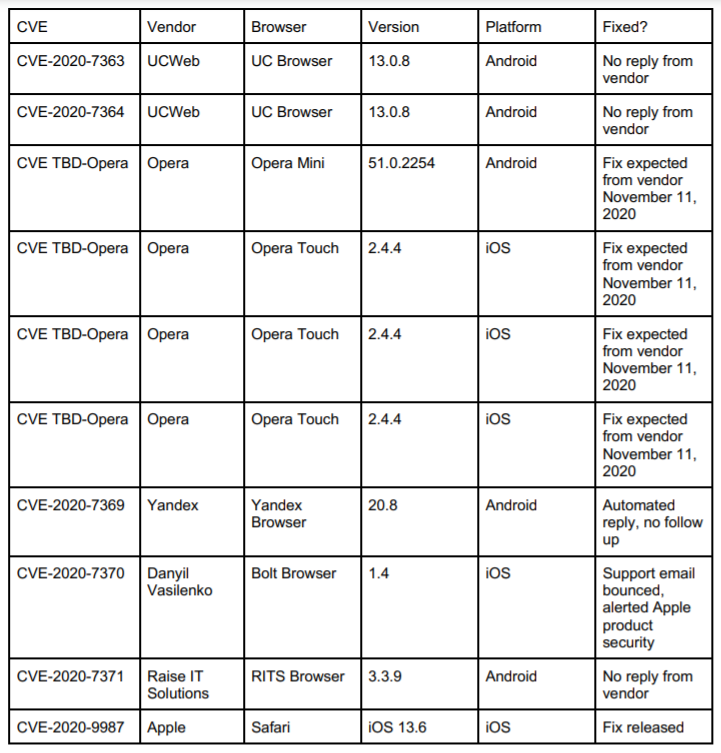
The bugs could affect a wide range of users, even for the lesser-used browsers. Bolt for instance has more than 210,000 reviews and ranks No. 47 in the App Store, and UC Browser has 500 million downloads from Google Play.
Users of the affected browsers should update where possible and otherwise remain wary.
“With the ever-growing sophistication of spear-phishing attacks, exploitation of browser-based vulnerabilities such as address-bar spoofing for conducting targeted phishing attacks may exacerbate the success of targeted attacks and hence prove to be very lethal,” Baloch concluded. “First and foremost, it is easy to persuade the victim into stealing credentials or distributing malware when the address bar points to a trusted website and giving no indicators forgery, secondly since the vulnerability exploits a specific feature in a browser, it can evade several anti-phishing schemes and solutions.”
The research also exposed similar bugs in some desktop browsers, according to the researchers, who said that those will be disclosed in a later writeup.
“It should be mentioned that MacOS Safari was also affected by the same issue (and fixed in the Big Sur MacOS release from a couple days ago),” Beardsley said.











