As 5G private networks roll out in the coming years, security may be a key issue for enterprises. A survey released at Mobile World Congress on Monday shows that major gaps persist in security capabilities among mobile operators.
Some 68 percent of operators already sell private wireless networks to enterprise customers, with the rest planning to do so by 2025, according to the study, from the GSMA and Trend Micro. However, from a security perspective, these may not be ready for prime time: 41 percent of surveyed operators said they face challenges when it comes to solving vulnerabilities related to 5G’s network virtualization, for instance.
Also, 48 percent of them said they don’t have enough internal knowledge or tools to discover and solve security vulnerabilities at all. A contributing factor to the problem is a limited pool of mobile-network security experts for 39 percent of surveyed operators.
5G Networks: Different Architecture, Different Risks
5G networks represent a sea change from prior wireless networks in that they are largely software-defined and virtualized. Network functions, historically defined in hardware, become virtual software capabilities in 5G, all orchestrated via a flexible software control plane. Even the air interfaces in the radio access network (RAN) are software-defined in 5G.
The problem is that this raises the possibility for rafts of exploitable vulnerabilities to emerge throughout the architecture in places that were never exposed before.
“Because so much of the environment is virtualized, there will be a lot of software creating images and tearing them down – the volume of virtualization is unlike anything we have experienced so far,” William Malik, vice president of infrastructure strategies at Trend Micro, told Threatpost. “The risk there is that we do not know how well the software will perform under such huge loads. Every experience with distributed software under load suggests that things will fail, services will drop and any vulnerability will be wide open for exploitation.” 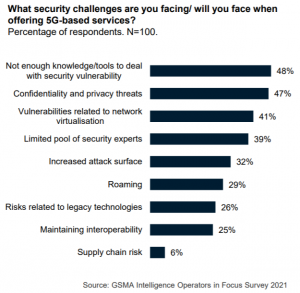
The stakes are higher, too. When it comes to 5G, it’s faster and has lower latency than earlier generations of wireless networks and will support a range of next-gen applications, including smart-factory installations, smart cities, autonomous vehicles, tele-surgery, advanced data analytics and artificial intelligence, among others. As such, 5G private networks will roll out in a variety of settings, including factories, where they’ll connect sensors and a range of industrial internet of things (IoT) devices; hospital and educational campuses; stadiums; industrial locations such as mines, ports and oil rigs; and to support public-safety applications.
“These networks will manage complex factories, distribution centers and logistics operations,” said Malik. “Think about the traffic at a major port – much of the work is not done by individuals but by application software coordinated by scheduling and orchestration software. If you can take this over, you can dump containers into Long Beach Harbor, or ship 2,000 pounds of Cream O’ Wheat to your neighbor. In the port of Amsterdam, the bad guys took over the scheduling software and actually had containers full of guns, drugs, and in some cases criminals, delivered without inspection into the port then smuggled onwards throughout Europe.”
And, instead of sending all data to a cloud for processing, 5G uses multi-access edge computing (MEC), which means that the network edge analyzes, processes and stores the data generated from endpoints. Collecting and processing data closer to the customer reduces latency and brings real-time performance to high-bandwidth applications, but it also presents a new footprint to secure, with new data pools scattered around the network.
“We’re focusing on corporate 5G implementations, generally called NPN – non-public networks. In these environments the 5G signal is restricted to a specific area – a port, a distribution center, a manufacturing facility – so we don’t have random devices connecting, and every application and device can be authenticated (note that this is not an architectural requirement but it is a really good idea),” Malik said. “Even with that, the 5G network will be a very efficient way to move data around the site, so if malware gets into something, it will spread fast.”
The survey found that half (51 percent) of the operators reported that MEC is a key part of their strategy for addressing enterprises’ private network needs within the next two years. Yet only 18 percent of surveyed operators offer security for both the edge and endpoints.
Best Practices for 5G Private Network Security
“The bad guys will try to take over the 5G network by either sneaking some rogue software into the mix, using a supply-chain attack like SolarWinds; or sneaking past authentication to launch their own processes that can cryptomine (stealing resources), exfiltrate data or set off a ransomware attack,” Malik said.
Even though security capabilities are lagging for now, nearly half (45 percent) of operators in the survey said they consider it extremely important to invest in security to achieve their long-term enterprise revenue goals – compared with just 22 percent in 2020.
A full 44 percent of operators said they have seen increased growth in demand for security services from their enterprise clients due to COVID-19, while 77 percent of operators look to security as a top opportunity for revenue generation, forecasting that 20 percent of 5G revenue will come from security add-on services.
The 3GPP, the standards body in charge of wireless network specifications, has built some security controls into the 5G spec:

There’s more that carriers can do, however, to help differentiate their offerings, according to Malik.
“Best practices for securing these NPN environments would include authenticating everything and everyone – that’s the idea behind zero trust,” Malik told Threatpost. “You have to prove you are who you say you are before you can do anything on the network.”
It’s also a good idea to log and audit message traffic and to use tools to note when lots of data seems to be flowing where it shouldn’t, he added.
“Also, use tools to detect processes that are misbehaving – like a process that starts encrypting everything it can touch,” according to Malik. “To help recover from an attack, take frequent backups and make sure they are valid. Also, buy technology from trusted vendors and use reliable integrators to hook things up.”
Join Threatpost for “Tips and Tactics for Better Threat Hunting” — a LIVE event on Wed., June 30 at 2:00 PM ET in partnership with Palo Alto Networks. Learn from Palo Alto’s Unit 42 experts the best way to hunt down threats and how to use automation to help. Register HERE for free!










