As people increasingly go mobile-first in their work and personal lives, cybercrime is keeping up: The latest is a phishing kit that specifically targets Verizon Wireless customers in the U.S.
According to Jeremy Richards, a researcher at Lookout Security, the kit pushes phishing links to users via email, masquerading as messages from Verizon Customer Support. These are tailored to mobile viewing: When the malicious URL is opened on a desktop, it looks sloppy and obviously not legitimate – however, when opened on a mobile device, “it looks like what you would expect from a Verizon customer support application,” he noted in an analysis on Monday. “In fact, the desktop version of it even looks like an ‘app’ interface.”
He added that the creators of the kit are clearly familiar with Verizon infrastructure in ways that go beyond spoofing customer service banners and graphics.
“For example, the first set of [phishing] domains include ‘ECRM,'” Richards noted. “The phisher is attempting to spoof ‘ecrm.verizonwireless[.]com.’ In this context, we believe ECRM stands for Electronic Customer Relationship Management as it is the domain used to send email from Verizon Customer Service to Verizon customers.”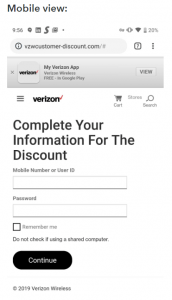
In all, Lookout observed three distinct campaigns that use the Verizon ECRM server address as part of their phishing sites. It also identified 51 potential other Verizon customer phishing domains registered in the last 90 days.
“This campaign shows that not only did the attackers research what Verizon’s infrastructure looks like, but that they were relentless in their attack,” Richards said. “We lack visibility into the effectiveness of this particular campaign, but for anyone that fell victim there is a very real risk of identity theft or account takeover – which is further compounded by the fact that mobile devices are frequently used in two-factor authentication.”
Attacks that target mobile devices have emerged as an effective attack vector, since many mobile devices lack traditional security, and because consumers don’t tend to think about mobile threats as often as they think about desktop concerns.
Yet, critical activities take place on the mobile platform every day: Think apps for mobile banking, communication, travel, work benefits and more; mobile email; and of course, mobile web browsing. Cybercriminals know this and are adapting accordingly.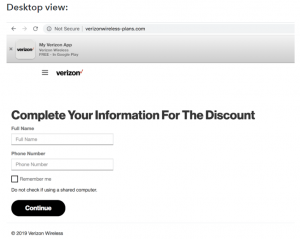
For instance, one well-known campaign spreads via WhatsApp – once a user is compromised, the malware sends a message out to everyone else in that person’s address book with a malicious link; because the message appears to come from someone they know, the user is much more likely to trust it.
“It would look like a pretty compelling, normal link,” said David Richardson, senior director of product management at Lookout, speaking on a recent Threatpost webinar. “If you click on that link on a mobile device, you would get a phishing page. If you would click on that link on a non-mobile device, you would actually get the real website that it was trying to point you to. This is a case where the attacker has actually decided, ‘I want to only target the mobile users.'”











