An academic analysis of cryptomining malware has determined that the Monero virtual currency (XMR) is “by far” the most popular cryptocurrency to mine among cybercriminals. And, it would appear that cryptomining as a criminal enterprise is unlikely to wane anytime soon.
After examining approximately 4.4 million malware samples (1 million of which turned out to be malicious miners) over a period of twelve years from 2007 to 2018, Sergio Pastrana of the Universidad Carlos III de Madrid and Guillermo Suarez-Tangil of King’s College London carried out a profit analysis that shows that criminals have mined more than 4.32 percent of the circulating XMR.
“Although this depends on when criminals cash-out their earnings, we estimate that the total revenue accounts for nearly $57 million,” they said in the paper [PDF], published earlier this month.
It should be noted that the estimates don’t take into account activity or profit from browser-based cryptojacking efforts (such as illicit use of the Coinhive mining code), which the team said is responsible for an equivalent amount of activity and profit.
To arrive at their conclusions, Pastrana and Suarez-Tangil employed a multistep approach, using both static and dynamic analysis to extract wallet addresses and pool domains; from there they aggregated related samples into larger campaigns, which were then cross-referenced with information gathered from various open-source intelligence repositories (such as VirusTotal). This data was then organized into a longitudinal graph, and then, focusing on Monero, the researchers measured the earnings gained by each of the campaigns.
The researchers saw both short-lived and longer-lasting Monero-mining campaigns — including multi-million campaigns operating for a continuous period of up to five years.
“Most profitable campaigns have longer activity (50 percent have been active since 2014),” they said. “However, we also observe a high portion of campaigns (around 43 percent) operating only for one or two years.”
2018 however saw a major uptick in coin-mining: There was a 1,500 percent increase in cryptomining malware when compared to 2017, according to a December report from eSentire Threat Intelligence.
This makes sense when considering macro factors: With the recent decline in the value of cryptocurrencies, the computing, power and cooling costs to legitimately mine stalwarts like Bitcoin now exceeds its value on the open market, eSentire noted. Monero mining however is comparatively lightweight and yields measurable amounts of currency without using industrial-level resources like Bitcoin does.
Compiling the mining code into a malware further overcomes economic challenges because the mining costs are absorbed by the unwitting device owner, while all of the profit goes to the threat actor.
Also, Pastrana and Suarez-Tangil noted that underground markets play a key role in pushing cryptomining forward in the criminal ecosystem, offering users with few technical skills the ability to acquire services and tools to set up their own mining campaigns.
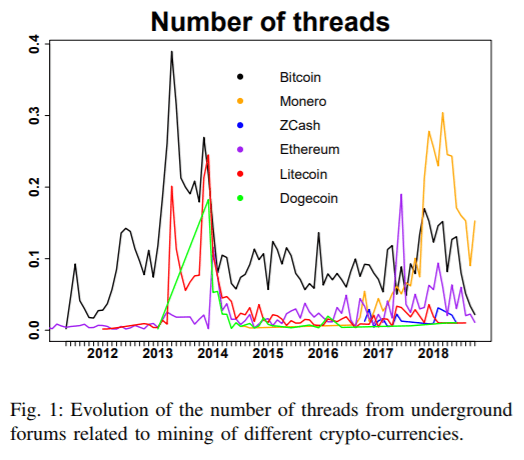 “We have analyzed a dataset of posts collected from various underground forums, looking for conversations related to crypto-mining. We observe that crypto-mining malware can be easily purchased online, for a few dollars (e.g., the average cost for an encrypted miner for Monero is $35),” they said.
“We have analyzed a dataset of posts collected from various underground forums, looking for conversations related to crypto-mining. We observe that crypto-mining malware can be easily purchased online, for a few dollars (e.g., the average cost for an encrypted miner for Monero is $35),” they said.
Further, Pastrana and Suarez-Tangil found that about 12 percent of the analyzed crypto-malware campaigns were supported by pay-per-install botnets. This dovetails with another eSentire finding, that activity from botnets saw a 500 percent increase over 2017.
“Botnets are often used to spread malware to a large number of machines and devices,” Mike Bittner, digital security and operations manager at The Media Trust, said via email. “The use of botnets as workhorses for illicit cryptomining operations makes economic sense because the same botnet used for cyptomining can also be used to spread the malware that puts infected machines under the botnet owner’s control.”
All in all, the cryptomining malware scene is unlikely to wane anytime soon, according to the researchers.
Pastrana and Suarez-Tangil noted that “one of the main reasons of the success of this criminal business is its relatively low cost and high return of investment. Our findings complement [previous] studies, corroborating that malicious crypto-mining is a growing and complex threat that requires effective countermeasures and intervention approaches. We also show that the profits made by the criminals are massive.”










