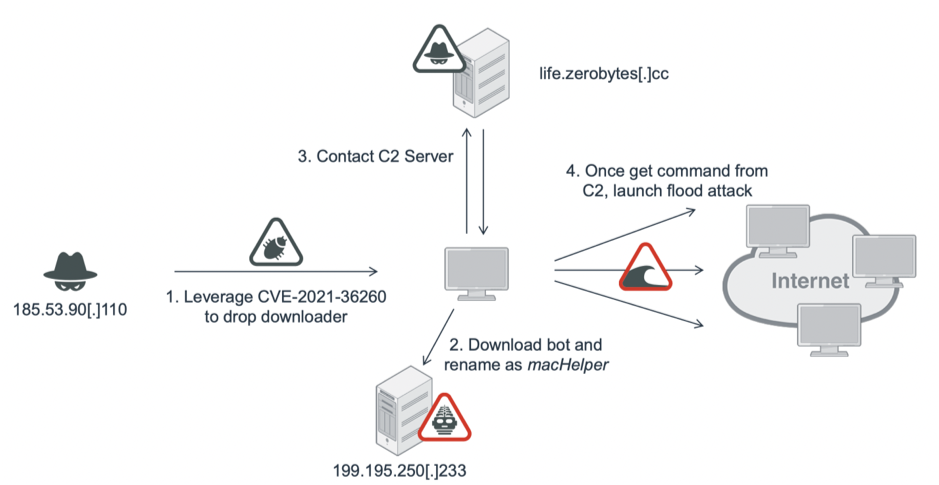
Although a patch was released in September, any still-vulnerable Hikvision IP Network Video Recorder (NVR) products are being actively targeted by the Mirai-based botnet known as Moobot.
FortiGuard Labs has released a report detailing how the Moobot botnet is leveraging a known remote code execution (RCE) vulnerability in Hikvision products (CVE-2021-36260) to spread a Moobot, which carries out distributed denial of service (DDoS) attacks.
The attack surface could be significant: China-based Hikvision touted itself as the “world’s leading video-surveillance products supplier” on the company site.
Once the attacker finds a vulnerable system, a downloader drops the malware, which FortiGuard identified as Moobot, a variant of Mirai with traces of Satori code. Sartori is another Mirai-based botnet and one of dozens that have been spun off the original source code.
“Its most obvious feature is that it contains the data string “w5q6he3dbrsgmclkiu4to18npavj702f”, which is used in the “rand_alphastr” function,” the researchers found in analyzing the binary. “It is used to create random alphanumeric strings with different purposes, such as for a setup process name or to generate data for attacking.”
Once it makes a connection with the command-and-control server (C2), it launches the DDoS attack, the report added, which looks like this:
Tracked to DDoS Service Provider
The analysts were able to track the code to a DDoS service provider’s Telegram channel called “tianrian,” which has been operating since August, they added.
“From the chatting channel we can see that the service is still updating,” FortiGuard’s report cautioned. “Users should always look out for DDoS attacks and apply patches to vulnerable devices.”
During Q3, threat researchers at Kaspersky found that the number of DDoS attacks shattered records, often topping thousands per day.
Linux-based Mirai was first identified in September of 2016 when it was used in a DDoS attack against Krebs on Security. A month later it took out a vast swath of the internet with a hit on Dyn. And despite its source code being released in October 2016, it has since become one of the most powerful internet of things botnets, infecting products and gadgets from brands including D-Link, SonicWall and Netgear, and other connected devices.
Fortinet listed Mirai as the top botnet threat in its analysis of the first half of 2021. The report’s author Derek Manky, Fortiguard Labs’ chief of security insights and global threat alliances doesn’t expect Mirai, or its related threat variants, to go away anytime soon.
“We’re going to fully expect to see more of [Mirai],” Manky said. “More Linux-based botnets. A lot of these targets, we’re not talking about Windows, but MacOS, we’ve already seen more and more … code written for Linux itself, and that is a majority of the [internet of things, or IoT] space.”
Any organizations running unpatched Hikvision systems are urged to get the firmware update provided by the company.
There’s a sea of unstructured data on the internet relating to the latest security threats. REGISTER TODAY to learn key concepts of natural language processing (NLP) and how to use it to navigate the data ocean and add context to cybersecurity threats (without being an expert!). This LIVE, interactive Threatpost Town Hall, sponsored by Rapid 7, will feature security researchers Erick Galinkin of Rapid7 and Izzy Lazerson of IntSights (a Rapid7 company), plus Threatpost journalist and webinar host, Becky Bracken.
Register NOW for the LIVE event!