 Spammers and malware writers have wasted no time in taking advantage of Monday’s bombings in Moscow, opening up a campaign on Twitter to point users to malicious sites.
Spammers and malware writers have wasted no time in taking advantage of Monday’s bombings in Moscow, opening up a campaign on Twitter to point users to malicious sites.
The pair of suicide bombings that hit the Metro system in Moscow Monday morning inevitably led to a flood of messages on Twitter and other social networking sites. The term Moscow became one of the top trending topics on Twitter very quickly Monday, and attackers have moved quickly to take advantage of that by spamming out messages using the word Moscow to attract unsuspecting followers.
Dmitry Bestuzhev, a malware analyst in Kaspersky Lab’s Latin America division, found that many of the links in these messages were pointing to malware, and also discovered that some of these malicious profiles have legitimate Twitter users as followers. This is a clear indication of the effectiveness of these types of campaigns. Users are eager for news about big events, and they’re not very careful about where they look for it.
Attackers took a similar tack when news broke late last week about the sentencing of convicted TJX hacker Albert Gonzalez. Within an hour of the news hitting the Web, attackers had started a black-hat SEO campaign designed to poison the search results for Gonzalez’s name with links to sites that would redirect users to malware.
The campaign was remarkably efficient, gaining second position, just behind a legitimate news story in Wired about the sentencing. The goal of this campaign was to infect users with rogue AV programs, a familiar tactic these days.
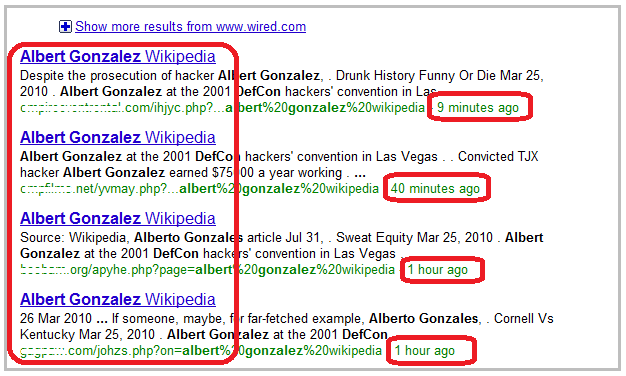
As you can see, some odd looking
links are among the first results. And those links appeared very
recently in the Google results page, within the last hour to be more
specific. Still, the link that showed up just “9 minutes ago” is
actually the second result in the Google ranking, right after the Wired
article. Makes you think of how hard the cybercriminals are working to
bypass Google’s algorithms, eh?
But what’s with these links? Well,
they might look like legitimate Wikipedia articles to the untrained
eye, but they’re not. These randomly named PHP scripts were uploaded to
compromised legitimate websites and then spammed using black SEO
techniques right to the top of the Google results page.
What’s novel about these attacks isn’t necessarily their techniques, but rather the speed with which they’re being executed. Attackers have been using major news events such as elections, natural disasters and terrorist attacks as fodder for these SEO and spam campaigns for some time now. But they’re clearly becoming much faster and more efficient at their craft, which is troubling news.









