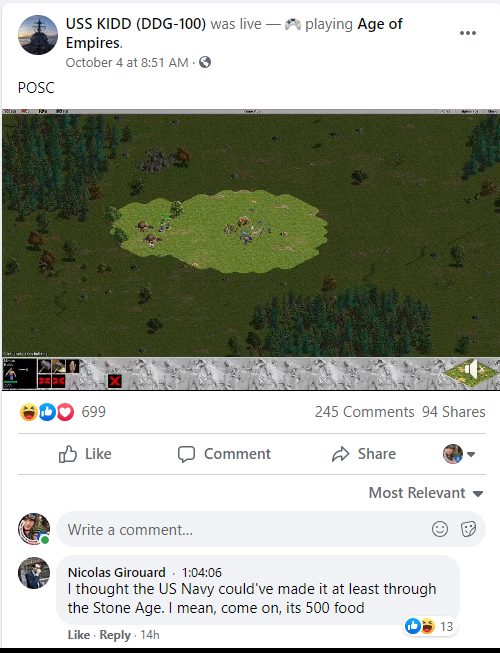
The official Facebook page of a destroyer-class Navy warship, the USS Kidd, has gone rogue: Someone has taken over the page in order to…stream Age of Empires play.
Age of Empires is a real-time online multiplayer strategy game in which the objective is to advance one’s civilization. Players “build, settle, trade and fight” their way from the Stone Age into the future, reaching certain milestones (inventing the wheel, ending feudalism) along the way. In the USS Kidd incident, practical jokers have anthropomorphized the warship, so that it appears to be having a great time playing the addictive game:
The pranksters have also changed the page type listing in the “About” information to “Gaming Video Creator.”
The incident was first reported by military news specialist Task & Purpose, which said that the USS Kidd‘s page was officially taken over at 10:26 p.m. on Sunday. The hijacked page of the warship, which finished up its latest active deployment in late September, then posted a joyful “Hahahahaha” and commenced four hours of live Age of Empires action.
One person commented on the post, “Just in time for Cyber Awareness month.”
Another five livestreams of the game followed before the posts stopped the next day, on Oct. 4. The posts garnered tens of thousands of views and hundreds of amused comments, including thoughts on the ship’s gaming prowess (i.e., “this guy is awesome but can’t get out of the Stone Age”).
And indeed, it never did progress – not great for a ship whose motto is “On to Victory.”
For its part, the Navy admitted the attack: “The official Facebook page for USS Kidd (DDG 100) was hacked,” Cmdr. Nicole Schwegman, a Navy spokesperson, confirmed to Task & Purpose on Tuesday. “USS Kidd‘s Facebook page had an unauthorized access from an unknown entity.”
In an update on Thursday, she said, “access has been secured by Facebook, and once their procedures are complete we’ll regain access to the page.” However, the page is still not recovered as of press time (4:15 p.m. ET on Oct. 7).
Serious Cybersecurity Concerns
Obvious humor value aside, there are serious security concerns underlying the incident, researchers pointed out. Essentially, the U.S. Navy lost control of the page and could do nothing but watch (literally) as unauthorized people posted unauthorized content.
“It’s easy to look at a compromised Facebook page and think that it’s no big deal,” said Jake Williams, co-founder and CTO at BreachQuest. “But many military units use Facebook pages as an official communication channel, particularly for family-readiness groups. A threat actor compromising an official Facebook page could create confusion and morale problems.”
As for speculating about the cause of the hack, reused credentials might be a good bet, he added.
“Unfortunately, many official pages are managed using a shared login, and as a result, multifactor authentication (MFA) is not enabled,” he said. “Where possible, organizations should not use shared logins for official pages. Instead, they should delegate control of the pages to individual accounts and ensure they have MFA enabled.”
Social-media account takeover (ATO) is a popular activity for cyberattackers, who are putting more and more resources into the activity. For instance, a malware called CopperStealer was recently discovered targeting Facebook and Instagram accounts, along with Apple, Amazon, Bing, Google, PayPal, Tumblr and Twitter credentials.
Crooks can monetize the data by selling credential collections that can be used for brute-force attacks against other, higher-value accounts; they can cause reputational damage through impersonation and rogue posts; or they can use the account to mount malware or phishing attacks on the followers or friends of the original account owner.
Check out our free upcoming live and on-demand online town halls – unique, dynamic discussions with cybersecurity experts and the Threatpost community.











