Update: Facebook has said that some of the Nemucod infections spreading over Facebook Messenger are not dropping Locky ransomware on victims’ computers as was initially reported. A Facebook spokesperson told Threatpost: “We maintain a number of automated systems to help stop harmful links and files from appearing on Facebook, and we are already blocking these ones from our platform. In our investigation, we determined that these were not in fact installing Locky malware—rather, they were associated with Chrome extensions. We have reported the bad browser extensions to the appropriate parties.”
The downturn in Locky ransomware infections toward the tail end of the summer was due in large part to successful efforts to halt the spread of the Nemucod downloader. Nemucod was one of the main vehicles delivering the malware to infected computers, usually via .zip email attachments hiding a .wsf extension.
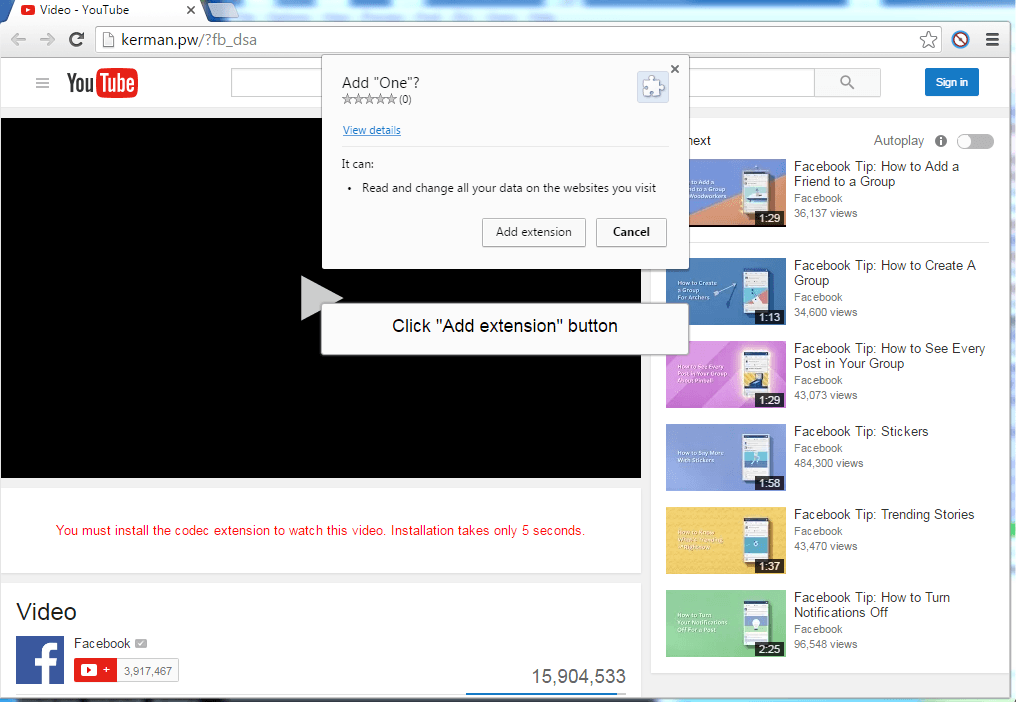
On Sunday, researcher Bart Parys said that a new campaign has popped up on Facebook Messenger where users are receiving images that are SVG files that contain embedded JavaScript. The script redirects users to a phony YouTube page that instructs them to install an extension to view the content.
The extension, instead, downloads a payload to the user’s machine. Researcher Peter Kruse of CSIS in Denmark said samples he’s seen are downloading Locky ransomware, though Parys said he has not seen the ransomware payload.
Confirmed! #Locky spreading on #Facebook through #Nemucod camouflaged as .svg file. Bypasses FB file whitelist. https://t.co/WYRE6BlXIF pic.twitter.com/jgKs29zcaG
— Peter Kruse | Cybercrime Research (@peterkruse) November 20, 2016
“Some have reported Locky ransomware, but I have been unable to reproduce that for now,”Parys told Threatpost. “As for the ones I found, only Chrome extensions were installed. I believe however they serve as a platform to download any additional malware.”
Requests for additional comment from Kruse and Facebook were not returned in time for publication. Kruse did tweet this morning that there are several different payloads, confirming a number of the same Chrome extensions that Parys wrote about, in addition to others that he said download Locky. Detection on VirusTotal, Kruse said, remains relatively low, with 11 of 55 detecting the threat.
Several payloads. On is a Chrome plugin named "Ubo" but others fetch Locky. https://t.co/a0n9NOjYxG
— Peter Kruse | Cybercrime Research (@peterkruse) November 20, 2016
The key is that the SVG file redirecting victims to the download is bypassing Facebook’s filters.
“My guess would simply be they weren’t filtering for this filetype before,”Parys said. “The exact details are unknown and I doubt Facebook will share them (and I think that’s for the best. we don’t want the cybercriminals to know how their filtering works).”
Once the victim installs the malicious extension,Parys said, they are redirected back to Facebook.
“So it probably steals your FB credentials as well (hence how it’s able to spread and send the message to all your friends),”Parys said.
SVG files, or scalable vector graphics, are in an XML format and are used for two-dimensional graphics. The use of the SVG file is also crucial to the campaign’s success given that an attacker could embed almost anything and the browser will open it.Parys cautions that Facebook users should be wary of messages containing only an image.
“There have been quite a lot of reports about it so it’s definitely successful,”Parys said. “The approach however is a classic: the lure of a photo (possibly of you) always works. Curiosity killed the cat.”
Parys said the script is heavily obfuscated and redirects to the phony YouTube page with a dialog box telling the user to download and install another extension in order to see the video.
“It seems like a downloader, at the very least it can pretty much change and do everything in your browser,”Parys said. “In either case, the JavaScript in the original file is heavily obfuscated, and so are all the JScripts in the Chrome extension itself.”
Parys said that he disclosed the issue to the Facebook and Chrome security teams. As temporary mitigations, he suggests disabling JavaScript in the browser, enabling click-to-play, blocking Wscript, or changing the Open With option for .svg, .js and .jse files to Notepad.
“This will effectively block the malware from being able to execute,”Parys said. “From Facebook’s side, this can definitely be fixed as well.”