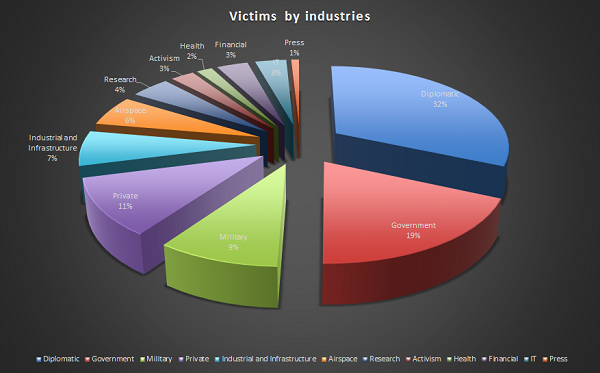
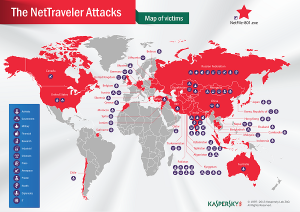
A new cyberespionage malware campaign with ties to China going back to the Titan Rain and Gh0stNet attacks has been targeting diplomats, military contractors and government agencies in 40 countries.
Researchers at Kaspersky Lab today unveiled details on NetTraveler, a data exfiltration tool, which has infected more than 350 high profile victims using primarily exploits targeting two patched Microsoft vulnerabilities. Costin Raiu, senior security researcher and head of the Global Research and Analysis Team, told attendees today at the 2013 Cybersecurity Forum in Washington, D.C., that one backdoor used in the NetTraveler campaign was probably written by the same developers responsible for Gh0st RAT. In fact, Raiu said, the same group of 50 or so developers could be behind a number of similar espionage attacks dating back close to a decade.
“There is a very common misconception that all these attacks are separate. In reality all these operations are connected to each other,” Raiu said. “The NetTraveler attacks are loosely connected with the Gh0stNet attacks, which are loosely connected with Titan Rain.
“They’re just one big ugly gorilla with a thousand faces and of course we haven’t seen all of them yet,” Raiu said.
In addition to diplomats and government targets, NetTraveler samples were found to be targeting Tibetan and Uyghur activists, oil production facilities, scientific research outfits, universities and private companies. The tool is capable of extracting system information, drop keylogging malware, steal Office documents such as Word, Excel and PowerPoint files, and its configuration can be modified if necessary to steal Corel Draw designs, AutoCAD files and other file types used in manufacturing and defense circles. The files are then compressed and encoded via custom protocols that resemble BASE64 code and sent to a command and control server via HTTP.
The attacker’s IP operation ranges, the Kaspersky report said, overlap with that of a malware family known as Zegost, or the Gh0st remote access Trojan; one of the Zegost command and control servers was still active as of a few weeks ago. They’re also used to distribute the Saker, a backdoor module used to steal system information that shares export functions via two DLLs named JustTempFun and ServiceMain. Those DLL names are also found in Gh0st RAT, the Kaspersky researchers said.
Some of the victims targeted by NetTraveler, meanwhile, are also victims of Red October. However, Kaspersky has not connected the attackers in these two campaigns.
“Although we see no direct links between the NetTraveler attackers and the Red October threat actor, the existence of victims infected by both of these campaigns is interesting. These infections indicate that certain high profile victims are targeted by multiple threat actors; the target information is a valuable commodity,” the report said, adding that the victims include a Russian military contractor, a Tajikistan government entity and embassy workers in Iran, Belguim, Kazakhstan and Belarus.
The attacks start with a spear phishing campaign targeting vulnerabilities described in CVE-2012-0158 and CVE-2010-3333. The messages and attached decoy documents vary according to the various targets and use a number of exploits that enable remote code execution and exploit of memory vulnerabilities in Office documents. Both have been patched, yet these attacks demonstrate the vulnerabilities are still reachable on some systems; no zero-days, rootkits or other advanced malware have been used in the NetTraveler campaign.
Kaspersky researchers found more than 22 gigabytes of stolen data on command and control servers they were able to sinkhole and analyze.
“However this data represents only a small fraction which we managed to see – the rest of the it had been previously downloaded and deleted from the C&C servers by the attackers,” a report on the campaign said.
Kaspersky researchers said the command and control servers were running IIS 6 and 7 and a Microsoft ASP backend. The attackers transferred the stolen data from the command infrastructure using FTP through a VPN connection to a server in the U.S. hosted by Krypt Technologies. “The infrastructure is secured by allowing FTP access only to remote users coming from predefined IPs, including the VPN provider in the U.S.,” the report said.
In all, more than 30 command and control servers are used in the NetTraveler campaign and all either collect stolen data or help with obfuscation of the attacks. NetTraveler is so named because of a string found in all early versions of the malware: “NetTraveler Is Running!”
Most of the victims are diplomats, government agencies or military contractors, the report said. Combining data from the command and control servers and Kaspersky Security Network, almost 30 percent of infections happened in Mongolia, followed by Russia, India and Kazakhstan.
Kaspersky’s GReAT team released a research report on NetTraveler, which includes indicators of compromise, that can be downloaded here.