A new version of the Adwind remote access trojan (RAT) has been discovered taking aim at new targets.
Adwind (a.k.a. JRAT or SockRat) is a Java-based remote access trojan that sniffs out data – mainly login credentials – from victims’ machines. While Adwind has historically been platform-agnostic, researchers say they have discovered a new four-month-old version targeting specifically Windows applications – like Explorer and Outlook – as well as Chromium-based browsers (Chromium is a free and open-source web browser developed by Google), including newer browsers like Brave.
The swap up in targeting “shows that attackers are closely keeping track of newly released applications that are gaining traction amongst end users and adapt their RAT functionality to steal information from these new applications,” Krishnan Subramanian, security researcher at Menlo Labs, told Threatpost.
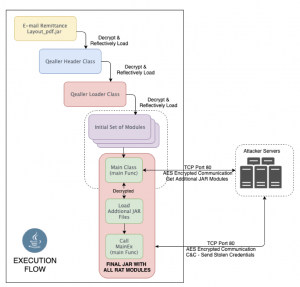
The new variant is a JAR file (Java ARchive; a package file format typically used to aggregate many Java class files) that researchers say is typically delivered from a link in a phishing email or downloaded from a legitimate site serving up insecure third-party content.
Researchers said they have also observed many infections originating from outdated WordPress sites, which is “growing in popularity due to the vulnerabilities in the publishing platform.”
“Going by the uptick in the number of wordpress vulnerabilities being exploited in the wild, we believe that the initial JAR file was served from compromised WordPress servers,” Subramanian told Threatpost.
Attack Vector
Once delivered, this new Adwind variant obfuscates the initial JAR file, blocking against any signature-based detection methods.
“Malware that takes advantage of common Java functionality is notoriously difficult to detect or detonate in a sandbox for the simple fact that Java is so common on the web,” researchers with Menlo Security said in a Tuesday post. “In fact, any effort to block or limit Java would result in much of the internet breaking down — a non-starter for users who increasingly rely on rich web apps or SaaS platforms for their day-to-day responsibilities.”
The JAR file then decrypts and loads a loader, which then loads an initial set of modules and sends out a request that is responsible for initializing the RAT with the command-and-control (C2) server.
Adwind is then able to decrypt a configuration file to get a list of C2 server IP addresses. Once an address is selected, an AES-encrypted request is made (via TCP Port 80) to remotely load a set of additional JAR files, researchers said.
Once downloaded, the JAR files activate the trojan, which becomes fully functional and is able to send a C2 request to access and send credentials from the browser and various Windows applications to a remote server.
These credentials can include personal bank credentials or business app logins – basically any password saved in a browser or application running on Windows.
Adwind has been around for a while, but continues to make waves with evolving variants and new targets.
The trojan was most recently seen in an August 2019 phishing campaign that took aim at national grid utilities infrastructure. Adwind, was being used as a a malware-as-a-service model in that campaign, researchers said, with features including the ability to take screenshots, harvest credentials from Chrome, Internet Explorer and Microsoft Edge, record video and audio, take photos, steal files, perform keylogging, read emails and steal VPN certificates.
Detection Difficult
Adwind has made bypassing and disabling security tools a hallmark. Last year, a new variant emerged that used a fresh take on the Dynamic Data Exchange (DDE) code-injection technique for anti-virus evasion.
Most notably, the Adwind trojan is able to mask its behavior by acting like any other Java command, researchers said.
“Without dynamic construction of the initial JAR file, threat intelligence has very little or no heuristics with which to create a static rule or signature that can effectively detect the initial JAR payload among the millions of Java commands flowing in and out of the corporate network,” said researchers. “It’s like wading through a crowd of a million people and trying to pick out the one person wearing a green undershirt without being able to look under people’s jackets. There’s nothing suspicious about its existence, its appearance or even its initial behavior. Everything about it seems normal.”
What are the top mistakes leading to data breaches at modern enterprises? Find out: Join experts from SpyCloud and Threatpost senior editor Tara Seals on our upcoming free Threatpost webinar, “Trends in Fortune 1000 Breach Exposure.” Click here to register.