Exploit kits come and go, but the exploits they utilize remain the same, according to Securelist’s mid-year analysis of exploit kits and attack vectors.
In 2010, the top five exploit kits, ordered by prevalence, were the Phoenix, Eleanor, NeoSploit, YESExploitKit, and SEOSPloitPack exploit kits. The following year saw the emergence of the Blackhole exploit kit as the new number one, NeoSploit jumped to the second spot, Phoenix fell to third, the Incognito kit appeared at number four, and Phoenix fell to fifth.
What is more interesting than the apparent revolving door of exploit kits, according to Kaspersky Lab expert Vicente Diaz, is how the exploits are used and what they target.
In 2010, the report claims that some 40 percent of new exploits targeted Java, and according to another security expert, Dan Guido, 11 of the top 15 kits include at least one java exploit, seven of which include more than one.
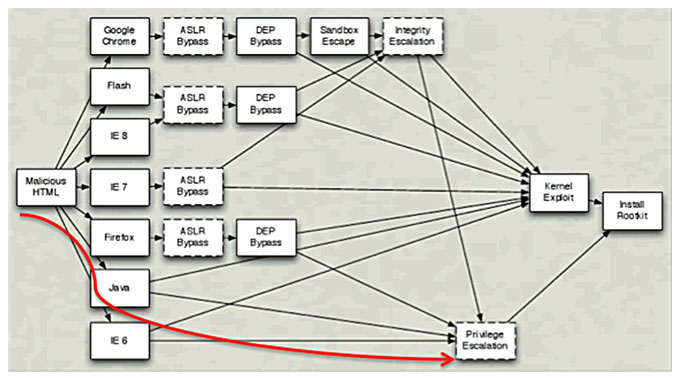
The Java spike began in mid-2010, and according to Diaz, there is a simple solution for the popularity of kits with Java exploits: they bypass operating system security measures more easily than other exploits (as illustrated by the accompanying image).
Another interesting aspect of Diaz’s analysis is that two of the emerging kits, Blackhole and Incognito, serve a nearly identical list of exploits. Furthermore, Diaz claims this list isn’t all that different from older kits either.
“These two kits are not adding anything new to the landscape,” says Diaz, “and [they] are still using the same exploits and targeting Java.”
Diaz claims that as long as these relatively old exploits continue to compromise unpatched systems, there is no need to seek out and use valuable zero-days.









